Feeling bad about your last security audit? Check out what just happened to the US Department of Interior
The US Department of the Interior (DoI) spectacularly failed its latest computer security assessment, mostly for a lack of Wi-Fi defenses.
This is according to a report [PDF] from the department’s inspector general (via NextGov) which found that, among other failings, the DoI internal wireless network could be broken into over the air using a smartphone and less than $200 of gear stuffed into a backpack.
For those unfamiliar, the Department of Interior manages America’s natural parks, government-owned lands, and services for indigenous people. It is a massive organization with about 70,000 employees spread around hundreds of different programs.
“These attacks — which went undetected by security guards and IT security staff as we explored department facilities — were highly successful,” the penetration-test report noted. “In fact, we intercepted and decrypted wireless network traffic in multiple bureaus.”
It went on: “Even worse, with regard to two bureaus, our penetration test went far beyond the wireless network at issue and gained access to their internal networks. In addition, we successfully obtained the credentials of a bureau IT employee and were able to use that person’s credentials to log into the bureau’s help desk ticketing system and view the list of tickets assigned to the employee.”
In short, a red team set up malicious wireless access points that masqueraded as legit Wi-Fi base stations, aka evil twins, and used these to harvest network credentials from unsuspecting users who connected to the gadgets. Thus federal staff joining what they thought were proper wireless networks were connecting to bogus ones that collected their login details.
Using this information, the would-be baddies then joined the legit networks, accessed internal systems at two bureau offices, and also sniffed and cracked a number of account credentials going over the air. From the report:
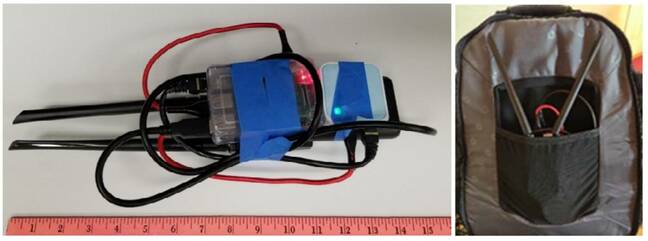
In fact, the attacks were so successful, “one bureau shut down its enterprise-wide wireless infrastructure for three weeks” to shore up its defenses. Here’s what those units – containing unspecified hardware but likely some kind of Wi-Fi-enabled RaspberryPi-like gizmos attached to batteries – looked like:
The infosec experts also noted other security shortfalls, such as a lack of network segmentation that would allow intruders to casually move between systems, incomplete inventory records of wireless networks, and a reliance on pre-shared keys that could be exploited by miscreants to eavesdrop on network traffic.
“Without network segmentation, an attacker, once inside a bureau’s network, can pivot to other bureaus and their computer networks without restriction or detection,” the red team explained.
Ultimately, the pen-testers said, the department’s failings came from the top down. Many of the branch offices, it is said, were not given guidance on how to keep their networks secure. A lack of attention to basic security practices cleared the way for outsiders to harvest user credentials, and gain access to the inner-workings of the US government with nothing more than a backpack of electronics from Amazon.

You weren’t hacked because you lacked space-age network defenses. Nor because cyber-gurus picked on you. It’s far simpler than that
“The department’s contradictory and outdated guidance, incomplete inventory, and lack of technical security testing led to its implementation of insecure wireless networks,” the report thundered. “We exploited vulnerabilities in the protocols used to authenticate individuals using unique user credentials and those using pre-shared keys. In addition, we gained more access than necessary because the department did not follow the principle of least privilege and did not have the proper defense-in-depth security controls.”
What’s worse, the red teamers said they could have done more theoretical damage had it not been for bureaucracy getting in the way. Get these peeps a few more laptops and some expense accounts, stat.
“We were unable to perform additional planned tests due to the lack of a reliable inventory,” they noted. “We were also limited in our ability to focus our testing on high-risk networks.”
While the watchdog’s report involves a government IT setup, its findings and recommendations should be noted by private organizations, particularly those that do contract work for Uncle Sam. Multiple attacks on governments have been carried out by first targeting the networks of contractors. ®
READ MORE HERE