Finding the signal of community in all the noise at Black Hat
I don’t know about you, but I find large conferences overwhelming. Don’t get me wrong, nothing beats the innovative potential of bringing a diverse group of brilliant people together to hash through thorny issues and share insights. But there are so many speakers, booths, and people, it can be a challenge to find the signal in all the noise—did I mention conferences are also really loud?
So last week when I stepped into the first of multiple showrooms at the Mandalay Hotel in Las Vegas for the Black Hat Briefing, I have to admit I felt a little nostalgia for the very first Black Hat Conference. It was 1997 at the old Aladdin Casino in Las Vegas. A casino with a long and colorful history, slated to close a few months after the conference ended. 1997: That was before Facebook and the iPhone, before the cloud. At the time, the RSA Conference was still mostly focused on cryptography, and those of us concerned about security vulnerabilities and how they impacted practitioner’s day in and day out had few opportunities to just get together and talk. The first Black Hat Briefing was very special. If my memory serves, there were only a couple hundred of us in attendance—compared to thousands today—and through those connections we built a community and an industry.
Building a community was key to creating the information security industry that exists today, and I believe that building community is just as critical now as we face down the new security threats of a cloud-and-edge world, an IoT world. We need the whole defender community—white hat hackers, industry, and government—working together to protect the security of our customers.
The security research community plays a fundamental role in community-based defense
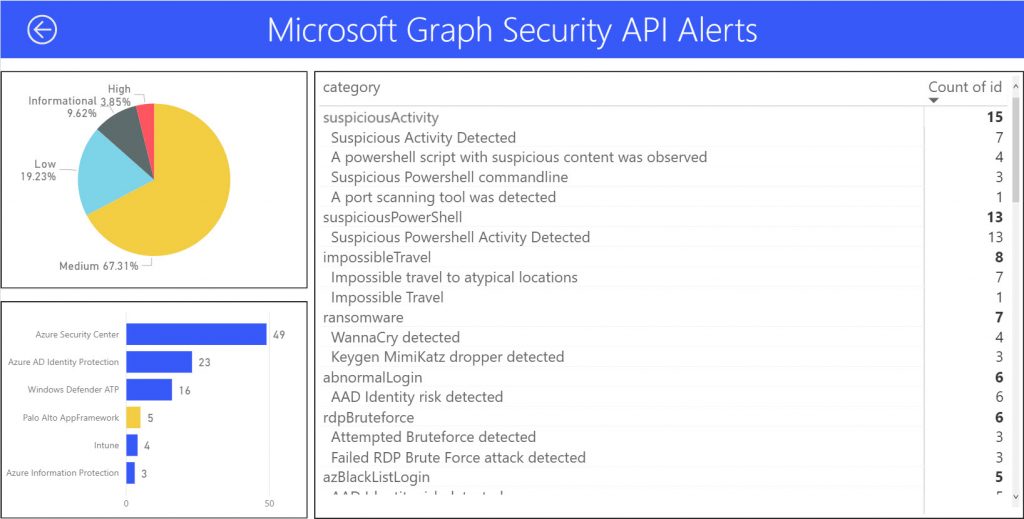
Over the last few years, Microsoft has been expanding and redefining what makes up our security community—one of the many positive evolutions since that first Black Hat. Like most tech companies, we once believed that any hacker outside of the organization posed a risk, but as we’ve gotten to know each other through many years of hard-earned trust and collaboration, we, and the security research community, have learned that our values aren’t so different. Sometimes the only way to make something stronger is to break it. We know we can’t on our own find all the gaps and errors in code that lead to vulnerabilities that criminals exploit to steal money and data. We need great minds both inside and outside our organization. Many of those great minds in the security research community collaborate with us through the Microsoft Security Response Center, and Black Hat was the perfect place to announce the subset of those researchers that made our annual “Top 100 Security Researchers List.”

We really appreciate the ongoing support from the community and encourage new researchers to report vulnerabilities to the Microsoft Security Response Center and participate in the Microsoft Bounty Program.
It takes a community to protect the security of our customers
As much as Microsoft values the relationship we have with researchers, we also attended Black Hat as industry partners. We want to help educate our peers on notable vulnerabilities and exploits, and share knowledge following major security events. As an example, one of our sessions focused on how Spectre and Meltdown are a wake-up call on multiple dimensions: how we engineer, how we partner, how we react when we find new security vulnerabilities, and how we need to become more coordinated. When I think about what was so exciting about that first conference, this is what comes to mind: those moments when we hear what our partners have learned, share what we know, and build on those insights to strengthen our collective response. The tech industry is increasingly interdependent. It’s going to take all of us working together to protect the safety and security of our customers’ devices and data.

But the meeting of the minds at annual security conferences, while important, is not enough. Microsoft also believes that we need a more structured approach to our collaboration. Cybersecurity is not just about threats from hackers and criminal groups; it has increasingly become a situation where we’re facing a cyberweapons arms race with governments attacking users around the world. We know this is a challenge we must pursue with our partners and customers, with a sense of shared responsibility and a focus on constantly making it easier for everyone to benefit from the latest in security advances. Microsoft has been working to help organize the industry in pursuit of this goal.
This past April during the RSA Conference, we came together as initially 34 companies, now 44 companies, and agreed to a new Cybersecurity Tech Accord. In this accord, we all pledge to help protect every customer, regardless of nationality, and will refrain from helping governments attack innocent civilians. It’s a foundation—on which we are building—to take coordinated action and to work with all our partners and many others to strengthen the resilience of the ecosystem for all our customers.
I admit it, I do sometimes miss attending those small, tightly knit conferences of old. But I’m even more inspired about the possibilities that I see as we continue to build on these collaborative models. We’ve seen a lot of progress recently working with our partners and the security research community. If you listen closely, I think you can hear the signal breaking through.
READ MORE HERE