Franchises, partnerships emerge in Ransomware-as-a-Service operations
Over the past year, many ‘franchise’ deals and new partnerships have emerged in the Ransomware-as-a-Service (RaaS) industry.
RaaS has arguably become one of the most prolific and dangerous threats to enterprise security today. Cybercriminals have worked out that they can make serious profits from leasing out their ransomware creations, and especially if it is used against large companies able to pay high ‘ransom’ payments to have their data decrypted after a successful infection.
Furthermore, the industry has evolved over recent years to also include other roles — malware developers, native speakers of a language able to manage negotiations, and Initial Access Brokers (IABs) who offer network access to a target system, thereby speeding up RaaS operations.
Leak sites, too, are now common. When a ransomware group attacks a victim, they may steal sensitive corporate information before encrypting systems. The cybercriminals will then threaten to publish this data unless a payment is made.
On Friday, KELA published a report on ransomware operators’ overall trends and movements over 2021. The cybersecurity firm says that the number of major organizations tracked as ransomware victims increased from 1460 to 2860, with many appearing on ransomware leak sites and negotiation platforms.
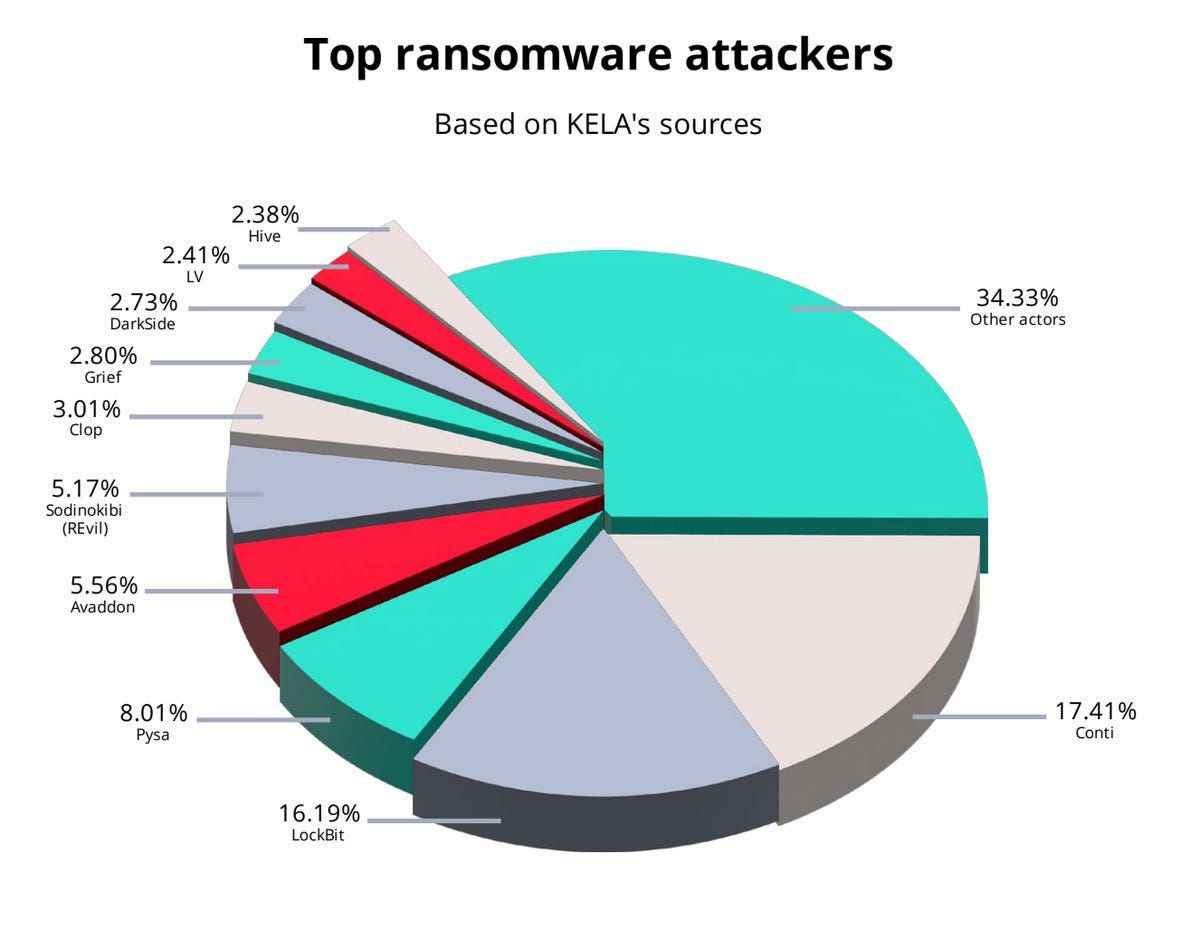
In total, 65% of the leak sites monitored last year were managed by new players on the scene. The majority of targets are based in developed nations, including the US, Canada, Germany, Australia, Japan, and France.
Manufacturing, industrial companies, professional services, technology, engineering, and retail are among the sectors that are at the most risk of being targeted by ransomware operators.
However, once a company has been breached, this does not mean that the security headache is restricted to only one incident.
As an example, Party Rental appeared on Avaddon’s leak site in February 2021, and Conti allegedly claimed the same victim in September. Both groups shared data belonging to the company. Amey, too, appeared on Mount Locker’s domain and then Clop’s.
According to KELA, roughly 40 organizations compromised in 2020 were then hit by a separate ransomware group last year, and “it is possible the groups used the same initial access vector.”
“Operators of data leak sites, namely Marketo and Snatch, frequently claimed the same victims as many ransomware groups (Conti, Ragnar Locker, and more), hinting about possible collaboration,” the report says.
Over 1300 access listings were posted in the underground by at least 300 IABs over 2021. LockBit, Avaddon, DarkSide, Conti, and BlackByte are among the Russian-speaking ransomware operators who frequently purchase access.
While some intrusions may be coincidental, it does appear that “franchise” businesses are emerging. Trend Micro previously connected the dots between Astro Team and Xing Team, both of which were allowed to use the Mount Locker ransomware under their own brand names.
The same malware was in use, while each cybercriminal group maintained their own name-and-shame blogs. Some of the victims were duplicated in Astro/Xing Team and Mount Locker disclosures. In addition, 14 victim organizations were published under Quantum, Marketo, and Snatch blogs in 2021.
“Collaboration can mean that ransomware operators share stolen data with actors behind data leak sites on specific conditions,” the researchers say. “For operators, it can mean additional profits if the data is sold on a data leak site or simply more intimidating to the victim (or future victims). Aside from collaboration, as between ransomware groups, actors behind these data leak sites can use the same entry vector or attack the same company via different initial access.”
Some of the major ransomware players vanished in 2021 — although they may emerge again under different brands — including BlackMatter and REvil. New groups including Alphv, Hive, and AvosLocker have emerged to fill the gap.
See also
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
READ MORE HERE

