Full Operational Shutdown—another cybercrime case from the Microsoft Detection and Response Team

Recently, we published our first case report (001: …And Then There Were Six) by the Microsoft Detection and Response Team (DART). We received significant positive response from our customers and colleagues and our team has been getting inquiries asking for more reports. We are glad to share the DART Case Report 002: Full Operational Shutdown.
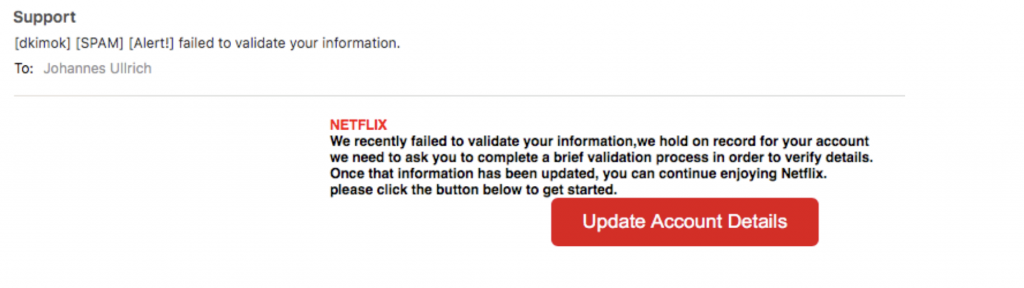
In the report 002, we cover an actual incident response engagement where a polymorphic malware spread through the entire network of an organization. After a phishing email delivered Emotet, a polymorphic virus that propagates via network shares and legacy protocols, the virus shut down the organization’s core services. The virus avoided detection by antivirus solutions through regular updates from an attacker-controlled command-and-control (C2) infrastructure, and spread through the company’s systems, causing network outages and shutting down essential services for nearly a week. In our report, you can read the details of the attack and how DART responded, review the attack lateral progression diagram and learn best practices from DART experts.
Stay tuned for more DART case reports where you’ll find unique stories from our team’s engagements around the globe. As always, you can reach out to your Microsoft account manager or Premier Support contact for more information on DART services.
DART provides the most complete and thorough investigations by leveraging a combination of proprietary tools and Microsoft Security products, close connections with internal Microsoft threat intelligence and product groups, as well as strategic partnerships with security organizations around the world.
READ MORE HERE