Future Exploitation Vector: File Extensions as Top-Level Domains

Cyber Threats
In this blog entry, we will examine the security risks related to file extension-related Top-Level Domains (TLDs) while also providing best practices and recommendations on how both individual users and organizations can protect themselves from these hazards.
In May 2023, Google launched eight new top-level domains (TLDs) that included .zip and .mov. Although seemingly harmless at first glance, it sparked discussion and debate across the internet since these domains can pose security risks due to cybercriminals exploiting them for malicious purposes. In this blog entry, we will examine these security risks while also providing best practices and recommendations on how both individual users and organizations can protect themselves from these hazards.
The use of legitimate websites for masking malicious URLs to avoid detection and minimize suspicion is a technique that cybercriminals have used for a long time. These websites are often used as referrer URLs that redirect to the malicious URLs. In the case of the .zip TLDs, one of the things that make it a potential security concern is the use of the @ operator on a website URL.
In an example provided by Medium’s Bobby Rauch, accessing the URL shown in Figure 1 will direct a user to bing.com instead of google.com. This just means that the URL before @ is, in practice, ignored and just act as a mask, whereas the one after the symbol is the actual target URL. In other words, the ” is just a delimiter.
Take note that this will not always be the case. It will require a special forward slash for domains that have subdirectories for the delimiter to work.
Elevating phishing campaigns
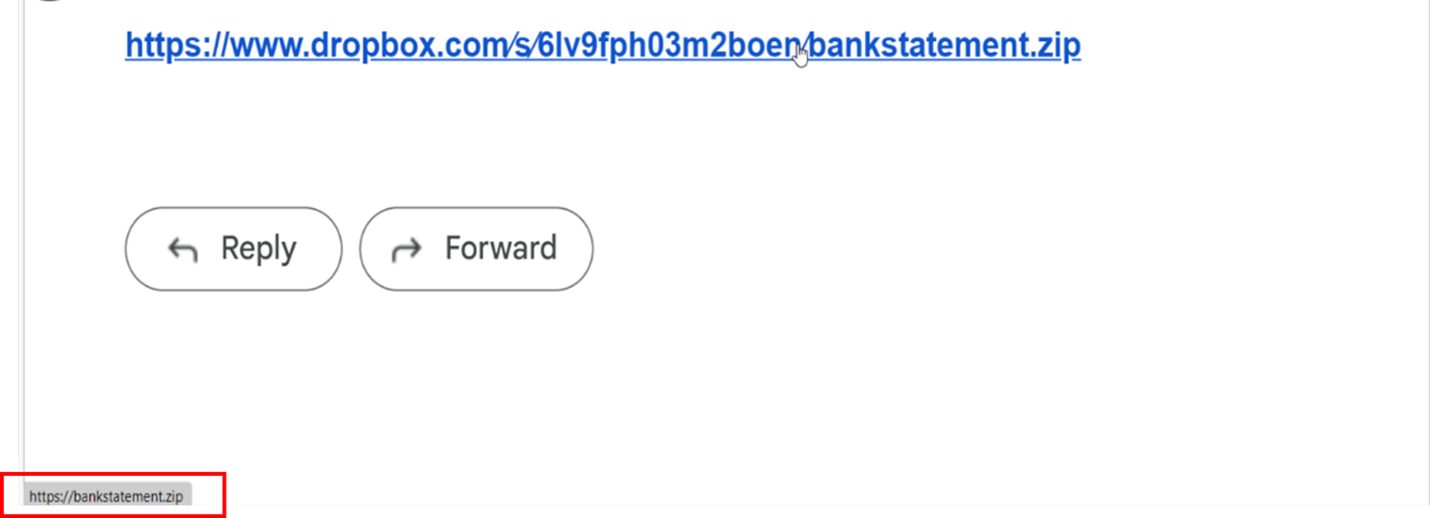
Figure 2 shows a Dropbox link embedded in an e-mail that can be assumed to download a file labeled bankstatement.zip. However, if users hover their mouse over the link, it shows that the “zip file” is not an archive but actually a website. In this case, the malicious actor can use the .zip domain as an attack vector by tricking users into accessing the intended website. Note that this is a mild version that doesn’t use Unicode characters in the URL or replace the forward slashes.
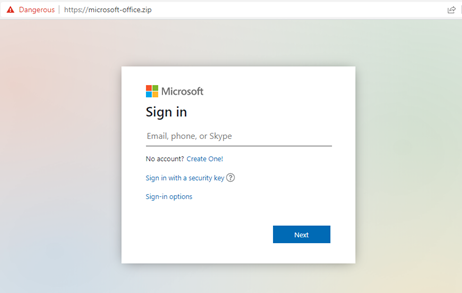
Figure 3 shows another example of a fake Microsoft Office login page using the URL microsoft-office[.]zip.
Malware delivery and other potential uses
ZIP files are often used as part of the initial stage of an attack chain, typically being downloaded after a user accesses a malicious URL or opens an email attachment (prominently employed by malware such as Emotet and QAKBOT). Beyond ZIP archives being used as a payload, it’s also likely that malicious actors will use ZIP-related URLs for downloading malware with the introduction of the .zip TLD.
Rauch provides another example of this, as shown in Figure 5, where a malicious actor can mimic the actual Kubernetes release URL by replacing the normal forward slashes with Unicode characters and adding an @ before the ZIP archive name. In this instance, the first URL is a legitimate GitHub page that will download v1271.zip while the second URL will access v1271[.]zip, where a malicious actor can potentially host a malicious file.
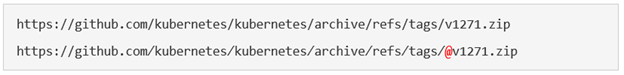
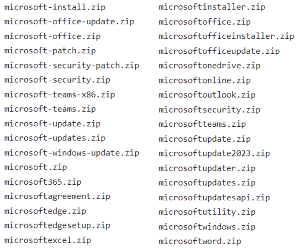
Figure 6 shows a set of websites from indicators of compromise (IoCs) of Vidar stealer that act as fake download URLs for Zoom. Once a user accesses these URLs, it will automatically download the malicious file Zoom.zip.
If a malicious actor used a .zip TLD with the @ delimiter, these websites could have been even more convincing as legitimate Zoom download URLs to potential victims.
Aside from malware delivery, these TLDs could be used in other ways, for example as a command-and-control (C&C) server. In extreme cases, organizations might resort to blocking all URLs using potentially exploitable TLDs since there is a high chance that they will be used for malicious purposes.
As of today, Trend Micro has not yet received URLs related to these new TLDs from internal and customer cases. However, we will continue to monitor any related URLs we come across and block them as needed in preparation for potential phishing campaigns.
Organizations and individual users can protect themselves from attacks that exploit TLDs by staying vigilant and exercising caution when receiving URLs with unfamiliar top-level domains (TLDs) and avoiding clicking on them unless certain that they are legitimate. Hovering the mouse cursor over links can provide a preview of their actual intended URLs. Furthermore, companies and developers should ensure that their tools, scripts, and applications do not rely on filename extensions, but instead should check the file type based on the file headers — otherwise a URL could trigger unwanted or risky behavior from these tools and scripts.
Organizations should also consider adopting user awareness training to cover emerging malware and techniques.
Users can also consider installing Trend Micro™ Check, a browser extension that blocks harmful links, intrusive pop-ups, and verifies the accuracy of online content. Meanwhile security technologies such as Maximum Security provide protection for various devices such as PCs, Macs, and mobile devices, helping users steer clear of fraud and scams.
Meanwhile, businesses using Trend products should implement the following:
- Enable advanced detection features such as Predictive Machine Learning (PML) or Behavior Monitoring (AEGIS) to prevent the execution of files exhibiting malware-like behavior.
- Always ensure that the latest pattern updates are installed to safeguard against potential malware threats.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE