Gmail Spoofing Vulnerability Sparks Google Priority 1 Probe
Google launched a “Priority 1” investigation into a Gmail security vulnerability after initially dismissing it as “intended behavior” that did not require a fix.
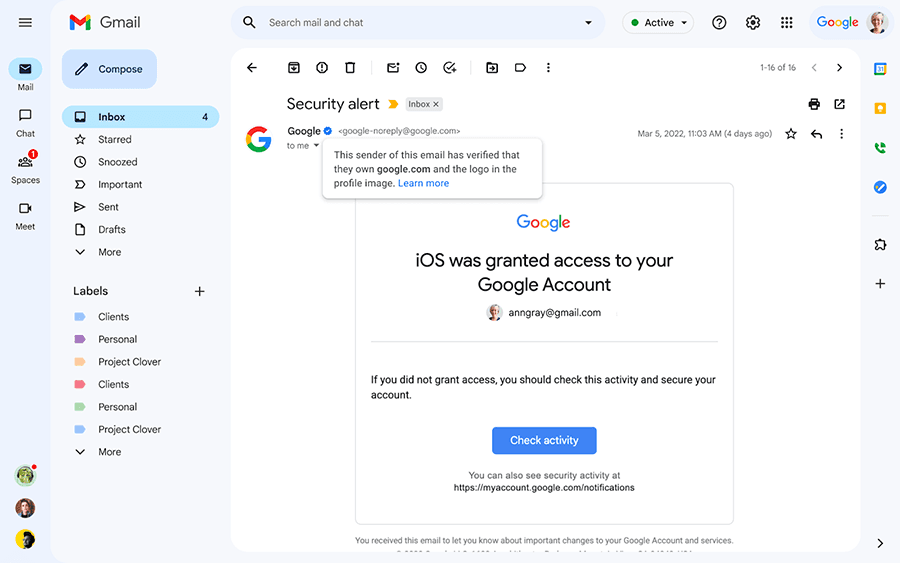
The vulnerability relates to the Brand Indicators for Message Identification (BIMI) email authentication method, a feature Google introduced to Gmail in 2021 but only recently rolled out to all 1.8 billion users of its email services.
With BIMI, a blue tick verification symbol is displayed on emails when the brand logo displayed as the sender’s avatar has been authenticated as matching the company claiming to be sending the email. BIMI is not exclusive to Google, rather it is part of ongoing efforts by a working group with a broad range of members who support the verification standard. The flaw brought to Google’s attention only impacts its own implementation of BIMI.
UPDATE (6/5 1:45pm ET): In a statement to SC Media sent after this report initially published Google said:
“This issue stems from a third-party security vulnerability allowing bad actors to appear more trustworthy than they are. To keep users safe, we are requiring senders to use the more robust DomainKeys Identified Mail (DKIM) authentication standard to qualify for Brand Indicators for Message Identification (blue checkmark) status.”
Spoof-proof, at least in theory
When Google announced the universal availability of BIMI to all Google Workspace customers and personal Google account users on May 3, the company emphasized the security benefits of the feature.
“This will help users identify messages from legitimate senders versus impersonators,” Google said.
“Strong email authentication helps users and email security systems identify and stop spam, and also enables senders to leverage their brand trust. This increases confidence in email sources and gives readers an immersive experience, creating a better email ecosystem for everyone.”
Given Gmail Google Workspace’s popularity as personal and business email platforms, users of the services are natural targets for threat actors.
Less than a month after rolling out BIMI across the platforms, New Hampshire security architect Chris Plummer received a malicious spoofed email in his Google inbox that had been incorrectly check-marked to indicate it was sent by UPS.
Ups and downs of BIMI
Plummer said on Twitter he alerted Google to the vulnerability through its bug bounty program but the company rejected his report with the message “won’t fix – intended behavior”.
The sender found a way to dupe @gmail’s authoritative stamp of approval, which end users are going to trust. This message went from a Facebook account, to a UK netblock, to O365, to me. Nothing about this is legit. Google just doesn’t want to deal with this report honestly.
— plum (@chrisplummer) June 1, 2023
“How is a scammer impersonating @UPS in such a convincing way ‘intended’[?] he wrote. “The sender found a way to dupe @gmail’s authoritative stamp of approval, which end users are going to trust. This message went from a Facebook account, to a UK netblock, to O365, to me. Nothing about this is legit.”
Plummer posted the email headers which indicated the spoofed message had failed the Sender Policy Framework (SPF) authentication process, another verification method.
After his tweet went viral, Google’s security team contacted Plummer to say they had had a change of heart over his bug bounty claim.
“After taking a closer look we realized that this indeed doesn’t seem like a generic SPF vulnerability. Thus we are reopening this and the appropriate team is taking a closer look at what is going on,” their message said.
It’s a bug, not a feature
“We apologize again for the confusion and we understand our initial response might have been frustrating, thank you so much for pressing on for us to take a closer look at this!”
Plummer posted a screenshot showing the investigation had been assigned a “Priority P1” status by Google.
Commenting on Plummer’s posts, one Twitter user said the problem appeared to be that UPS’s main domain had an SPF record and the spoofer had circumvented that protection by using a related subdomain.
“That subdomain don’t have a SPF record, and SPF is not meant to be inherited by subdomains. Perhaps it falls between the cracks because they’re using a subdomain.”
Another Twitter user said the email appeared to comply with BIMI because it passed the requirements of the Domain Message Authentication Reporting and Conformance (DMARC) authentication method.
Best laid plans of DMARK and SPF
“It passed DMARC because UPS use Microsoft for email (and it’s in their SPF record), so you just need to send it from any Microsoft account.”
Another commenter said: “Gmail can’t fix the fact that [Microsoft] knowingly delivered [an email] that it KNEW failed SPF and DMARC.”
Plummer told the Manchester Ink Link he did not know “why Google would get into the business of certifying email”.
“It was interesting that they were so bold in putting their own name on some of these communications [about the security benefits of the BIMI feature] when it relies on imperfect standards that are not within Google’s control.”
He said he learned on June 2, via LinkedIn, that UPS had taken action as a result of him raising the vulnerability with Google.
“That is unbelievable,” he said. “That’s an all-hands-on-deck kind of situation. I couldn’t believe the research I did compelled a company like UPS to change its infrastructure and actually got Google interested in changing its product.”
READ MORE HERE
