Google Play Apps Downloaded 300,000 Times Stole Bank Credentials

Researchers said they’ve discovered a batch of apps downloaded from Google Play more than 300,000 times before the apps were revealed to be banking trojans that surreptitiously siphoned user passwords and two-factor authentication codes, logged keystrokes, and took screenshots.
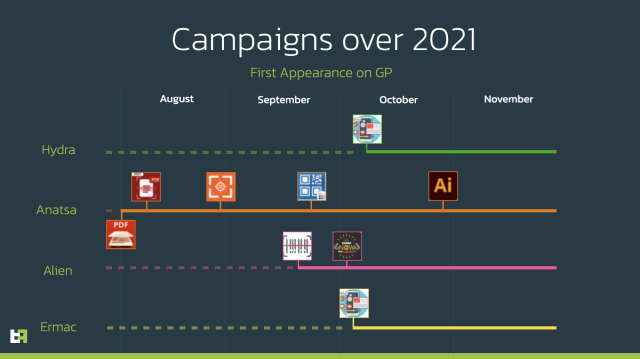
The apps—posing as QR scanners, PDF scanners, and cryptocurrency wallets—belonged to four separate Android malware families that were distributed over four months. They used several tricks to sidestep restrictions that Google has devised in an attempt to rein in the unending distribution of fraudulent apps in its official marketplace. Those limitations include restricting the use of accessibility services for sight-impaired users to prevent the automatic installation of apps without user consent.
Small footprint
“What makes these Google Play distribution campaigns very difficult to detect from an automation (sandbox) and machine learning perspective is that dropper apps all have a very small malicious footprint,” researchers from mobile security company ThreatFabric wrote in a post. “This small footprint is a (direct) consequence of the permission restrictions enforced by Google Play.”
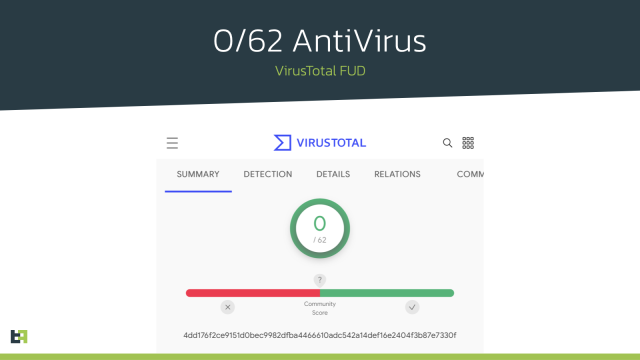
Instead, the campaigns typically delivered a benign app at first. After the app was installed, users received messages instructing them to download updates that installed additional features. The apps often required updates to be downloaded from third-party sources, but by then, many users had come to trust them. Most of the apps initially had zero detections by malware checkers available on VirusTotal.
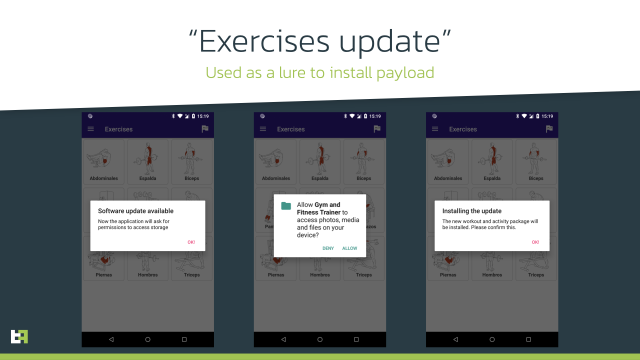
The apps also flew under the radar by using other mechanisms. In many cases, the malware operators manually installed malicious updates only after checking the geographic location of the infected phone or by updating phones incrementally.
“This incredible attention dedicated to evading unwanted attention renders automated malware detection less reliable,” the ThreatFabric post explained. “This consideration is confirmed by the very low overall VirusTotal score of the 9 number of droppers we have investigated in this blogpost.”
The malware family responsible for the largest number of infections is known as Anatsa. This “rather advanced Android banking trojan” offers a variety of capabilities, including remote access and automatic transfer systems, which automatically empty victims’ accounts and send the contents to accounts belonging to the malware operators.
The researchers wrote:
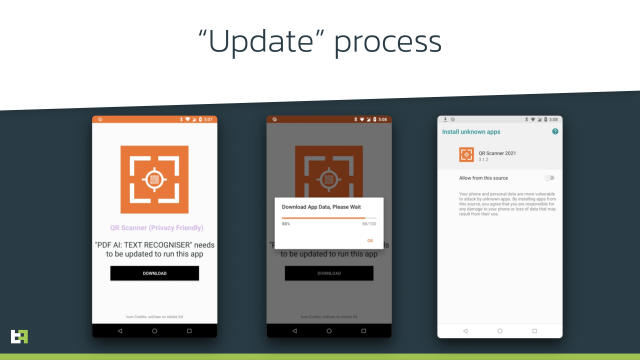
The process of infection with Anatsa looks like this: upon the start of installation from Google Play, the user is forced to update the app in order to continue using the app. In this moment, [the] Anatsa payload is downloaded from the C2 server(s) and installed on the device of the unsuspecting victim.
Actors behind it took care of making their apps look legitimate and useful. There are large numbers of positive reviews for the apps. The number of installations and presence of reviews may convince Android users to install the app. Moreover, these apps indeed possess the claimed functionality; after installation, they do operate normally and further convince [the] victim [of] their legitimacy.
Despite the overwhelming number of installations, not every device that has these droppers installed will receive Anatsa, as the actors made efforts to target only regions of their interest.
Three other malware families found by the researchers included Alien, Hydra, and Ermac. One of the droppers used to download and install malicious payloads was known as Gymdrop. It used filter rules based on the model of the infected device to prevent the targeting of researcher devices.
New workout exercises
“If all conditions are met, the payload will be downloaded and installed,” the post stated. “This dropper also does not request Accessibility Service privileges; it just requests permission to install packages, spiced with the promise to install new workout exercises—to entice the user to grant this permission. When installed, the payload is launched. Our threat intelligence shows that at the moment, this dropper is used to distribute [the] Alien banking trojan.”
The researchers listed 12 Android apps that participated in the fraud. The apps are:
| App name | Package name | SHA-256 |
|---|---|---|
| Two Factor Authenticator | com.flowdivison | a3bd136f14cc38d6647020b2632bc35f21fc643c0d3741caaf92f48df0fc6997 |
| Protection Guard | com.protectionguard.app | d3dc4e22611ed20d700b6dd292ffddbc595c42453f18879f2ae4693a4d4d925a |
| QR CreatorScanner | com.ready.qrscanner.mix | ed537f8686824595cb3ae45f0e659437b3ae96c0a04203482d80a3e51dd915ab |
| Master Scanner Live | com.multifuction.combine.qr | 7aa60296b771bdf6f2b52ad62ffd2176dc66cb38b4e6d2b658496a6754650ad4 |
| QR Scanner 2021 | com.qr.code.generate | 2db34aa26b1ca5b3619a0cf26d166ae9e85a98babf1bc41f784389ccc6f54afb |
| QR Scanner | com.qr.barqr.scangen | d4e9a95719e4b4748dba1338fdc5e4c7622b029bbcd9aac8a1caec30b5508db4 |
| PDF Document Scanner – Scan to PDF | com.xaviermuches.docscannerpro2 | 2080061fe7f219fa0ed6e4c765a12a5bc2075d18482fa8cf27f7a090deca54c5 |
| PDF Document Scanner | com.docscanverifier.mobile | 974eb933d687a9dd3539b97821a6a777a8e5b4d65e1f32092d5ae30991d4b544 |
| PDF Document Scanner Free | com.doscanner.mobile | 16c3123574523a3f1fb24bbe6748e957afff21bef0e05cdb3b3e601a753b8f9d |
| CryptoTracker | cryptolistapp.app.com.cryptotracker | 1aafe8407e52dc4a27ea800577d0eae3d389cb61af54e0d69b89639115d5273c |
| Gym and Fitness Trainer | com.gym.trainer.jeux | 30ee6f4ea71958c2b8d3c98a73408979f8179159acccc01b6fd53ccb20579b6b |
| Gym and Fitness Trainer | com.gym.trainer.jeux | b3c408eafe73cad0bb989135169a8314aae656357501683678eff9be9bcc618f |
Asked for comment, a Google spokesman pointed to this post from April detailing the company’s methods for detecting malicious apps submitted to Play.
Over the past decade, malicious apps have plagued Google Play on a regular basis. As was the case this time, Google is quick to remove the fraudulent apps once it has been notified of them, but the company has been chronically unable to find thousands of apps that have infiltrated the bazaar and infected thousands or even millions of users.
It’s not always easy to spot these scams. Reading user comments can help, but not always, since crooks often seed their submissions with fake reviews. Steering clear of obscure apps with small user bases can also help, but that tactic would have been ineffective in this case. Users should also think carefully before downloading apps or app updates from third-party markets.
The best advice for staying safe from malicious Android apps is to be extremely sparing in installing them. And if you haven’t used an app for a while, uninstalling it is a good idea.
READ MORE HERE
