Google’s ghost busters: We can scare off Spectre haunting Chrome tabs
Google is touting the benefits of a recently rolled out browser security feature called Site Isolation.
Site Isolation has been gradually introduced to users of the Chrome browser over several months, and now Google has officially unveiled this important piece of tech.
With Site Isolation is enabled, Chrome runs a different browser process for each internet domain. Google initially described Site Isolation as an “additional security boundary between websites,” preventing malicious webpages in a tab from messing with or spying on tabs and iframes displaying pages from other domains.
Rather than solely defending against cross-site scripting attacks, the technology is now positioned as a necessary defence against infamous data-leaking Spectre CPU vulnerabilities, as a blog post by Google explained this week:
Speculative execution side-channel attacks like Spectre are a newly discovered security risk for web browsers. A website could use such attacks to steal data or login information from other websites that are open in the browser. To better mitigate these attacks, we’re excited to announce that Chrome 67 has enabled a security feature called Site Isolation on Windows, Mac, Linux, and Chrome OS.
Site Isolation has been optionally available as an experimental enterprise policy since Chrome 63, but many known issues have been resolved since then, making it practical to enable by default for all desktop Chrome users.
In other words, on Windows, macOS, Linux, and Chrome OS devices, Chrome uses the security boundaries provided by the operating system to ringfence each domain into its own browser process. Threads used to render the page in one process cannot interfere with nor snoop on, via speculative execution or crafty JavaScript, other sites, preventing malicious pages from lifting passwords and other secrets.
Site Isolation was enabled by default on desktops with the release of Chrome 67, at the end of May, as previously reported.
In its blog post, Google goes on to explain how the tech works, adding that it had been working on Site Isolation even before Spectre appeared in January:
When Site Isolation is enabled, each renderer process contains documents from at most one site. This means all navigations to cross-site documents cause a tab to switch processes. It also means all cross-site iframes are put into a different process than their parent frame, using “out-of-process iframes.”
Splitting a single page across multiple processes is a major change to how Chrome works, and the Chrome Security team has been pursuing this for several years, independently of Spectre.
Site Isolation changes Chrome’s behaviour under the hood, but this “generally shouldn’t cause visible changes for most users or web developers,” according to Google. Although the vast majority (99 per cent) of Chrome users are being moved onto Site Isolation by default, Google is keeping one in a 100 on a temporary holdback to “monitor and improve performance.”
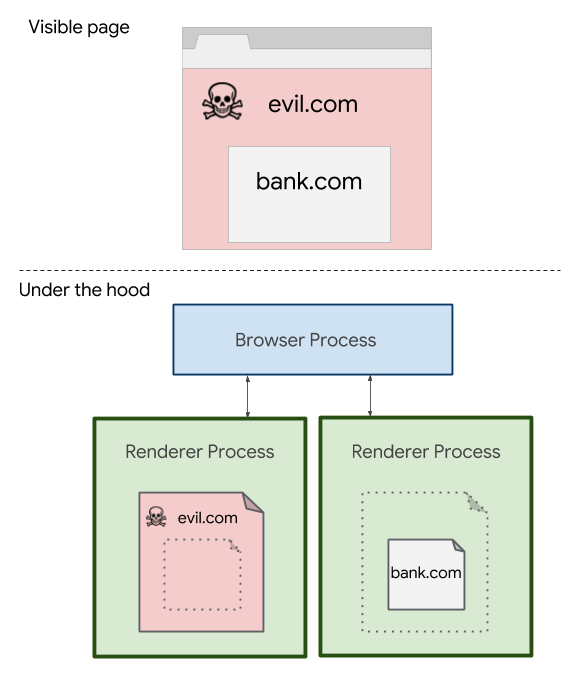
With Site Isolation, a single page may now be split across multiple renderer processes, preventing bad sites from snooping on legit ones … Source: Google
Spectre mitigations in software have been known to impair performance of applications, but it doesn’t seem the Chocolate Factory fears any major issues. The long soft launch of the technology provided plenty of time to iron out any wrinkles, after all.
Google is investigating how to extend Site Isolation coverage to Chrome for Android, where there are additional known issues. Ahead of prime time, experimental enterprise policies for enabling Site Isolation will be available in Chrome 68 for Android. ®
Sponsored: Minds Mastering Machines – Call for papers now open
READ MORE HERE
