Hackers Can Eavesdrop On Mobile Calls With $7,000 Worth Of Equipment
The emergence of mobile voice calls over the standard known as Long Term Evolution has been a boon for millions of cell phone users around the world. VoLTE, short for Voice over LTE, provides up to three times the capacity of the earlier 3G standard, resulting in high-definition sound quality that’s a huge improvement over earlier generations. VoLTE also uses the same IP standard used to send data over the Internet, so it has the ability to work with a wider range of devices. VoLTE does all of this while also providing a layer of security not available in predecessor cellular technologies.
Now, researchers have demonstrated a weakness that allows attackers with modest resources to eavesdrop on calls. Their technique, dubbed ReVoLTE, uses a software-defined radio to pull the signal a carrier’s base station transmits to a phone of an attacker’s choosing, as long as the attacker is connected to the same cell tower (typically, within a few hundred meters to few kilometers) and knows the phone number. Because of an error in the way many carriers implement VoLTE, the attack converts cryptographically scrambled data into unencrypted sound. The result is a threat to the privacy of a growing segment of cell phone users. The cost: about $7,000.
So much for more secure
“Data confidentiality is one of the central LTE security aims and a fundamental requirement for trust in our communication infrastructure,” the researchers, from Ruhr University Bochum and New York University, wrote in a paper presented Wednesday at the 29th USENIX Security Symposium. “We introduced the ReVoLTE attack, which enables an adversary to eavesdrop and recover encrypted VoLTE calls based on an implementation flaw of the LTE protocol.”
VoLTE encrypts call data as it passes between a phone and a base station. The base station then decrypts the traffic to allow it to be passed to any circuit-switched portion of a cellular network. The base station on the other end will then encrypt the call as it’s transmitted to the other party.
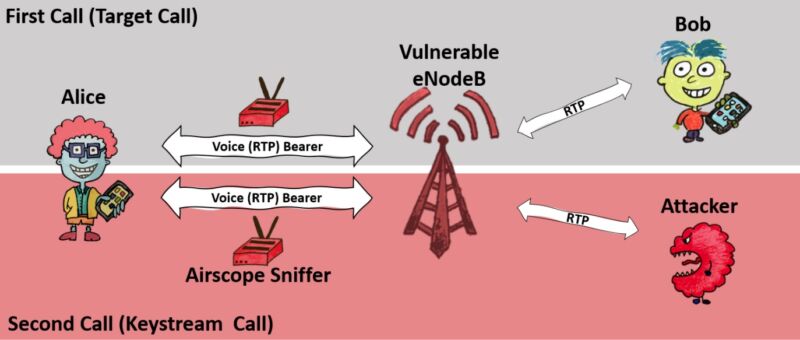
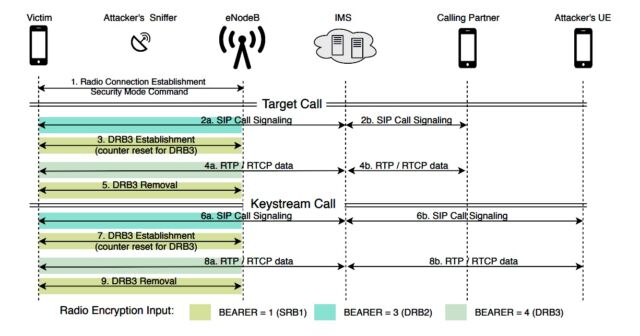
The implementation error ReVoLTE exploits is the tendency for base stations to use some of the same cryptographic material to encrypt two or more calls when they’re made in close succession. The attack seizes on this error by capturing the encrypted radio traffic of a target’s call, which the researchers call the target or first call. When the first call ends, the attacker quickly initiates what the researchers call a keystream call with the target and simultaneously sniffs the encrypted traffic and records the unencrypted sound, commonly known as plaintext.
The researchers described it this way:
The attack consists of two main phases: the recording phase in which the adversary records the target call of the victim, and the call phase with a subsequent call with the victim. For the first phase, the adversary must be capable of sniffing radiolayer transmissions in downlink direction, which is possible with affordable hardware for less than $1,400 [1]. Furthermore, the adversary can decode recorded traffic up to the encryption data (PDCP) when she has learned the radio configuration of the targeted eNodeB. However, our attacker model does not require the possession of any valid key material of the victim. The second phase requires a Commercial Off-TheShelf (COTS) phone and knowledge of the victim’s phone number along with his/her current position (i.e., radio cell).
The attacker then compares the encrypted and plaintext traffic from the second call to deduce the cryptographic bits used to encrypt the call. Once in possession of this so-called “keystream, the attacker uses it to recover the plaintext of the target call.
“The ReVoLTE attacks exploit the reuse of the same keystream for two subsequent calls within one radio connection,” the researchers wrote in a post explaining the attack. “This weakness is caused by an implementation flaw of the base station (eNodeB).”
The figure below depicts the steps involved, and the video below the figure shows ReVoLTE in action:
Limited, but practical in the real world
ReVoLTE has its limitations. Matt Green, a Johns Hopkins University professor who specializes in cryptography, explained that real-world constraints—including the specific codecs in use, vagaries in the way encoded audio is transcoded, and compression of packet headers—can make it difficult to obtain the full digital plaintext of a call. Without the plaintext, the decryption attack won’t work. He also said that keystream calls must be made within about 10 seconds of the target call ending.
Additionally, the amount of the target call that can be decrypted depends on how long the keystream call lasts. A keystream call that lasts only 30 seconds will provide only enough keystream material to recover 30 seconds of the target call. ReVoLTE also won’t work when base stations follow the LTE standard that dictates against the reuse of keystreams. And as already mentioned, the attacker has to be in radio range of the same cell tower as the target.
Despite the limitations, the researchers were able to recover 89 percent of the conversations they eavesdropped on, an accomplishment that demonstrates that ReVoLTE is effective in real-world settings, as long as base stations incorrectly implement LTE. The equipment required includes (1) commercial off-the-shelf phones that connect to cellular networks and record traffic and (2) commercially available Airscope software radio to perform real-time decoding of LTE downlink traffic.
“An adversary needs to invest less than $7,000 to create a setup with the same functionality and, eventually, the ability to decrypt downlink traffic,” the researchers wrote. “While our downlink ReVoLTE is already feasible, a more sophisticated adversary can improve the attack’s efficiency by extending the setup with an uplink sniffer, e. g., the WaveJudge5000 by SanJole where we can exploit the same attack vector, and access both directions simultaneously.”
Am I vulnerable?
In initial tests, the researchers found that 12 of 15 randomly selected base stations in Germany reused keystreams, making all VoLTE calls transmitted through them vulnerable. After reporting their findings to the industry group Global System for Mobile Applications, a retest found that the affected German carriers had fixed their base stations. With more than 120 providers around the world and over 1,200 different device types supporting VoLTE, it will likely take more time for the eavesdropping weakness to be fully eradicated.
“However, we need to consider a large number of providers worldwide and their large deployments,” the researchers wrote. “It is thus crucial to raise awareness about the vulnerability.”
The researchers have released an Android app that will test if a network connection is vulnerable. The app requires a rooted device that supports VoLTE and runs a Qualcomm chipset. Unfortunately, those requirements will make it hard for most people to use the app.
I emailed AT&T, Verizon and Sprint/T-Mobile to ask if any of their base stations are vulnerable to ReVoLTE. So far none of them has responded. This post will be updated if replies come later.
“Utterly devastating”
ReVoLTE builds off of a seminal research paper published in 2018 by computer scientists at the University of California at Los Angeles. They found that LTE data was often encrypted in a way that used the same keystream more than once. By using what’s known as an XOR operation on the encrypted data and the corresponding plaintext traffic, the researchers could generate keystream. With that in hand, it was trivial to decrypt the data from the first call.
The figure below shows how ReVoLTE does this:
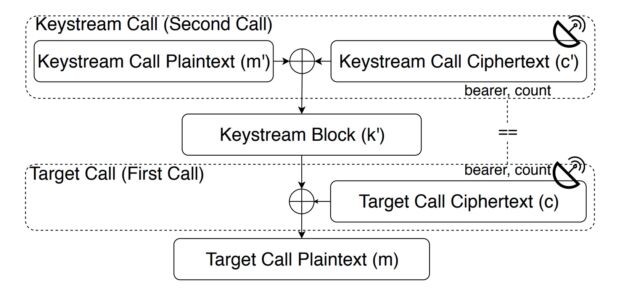
“The keystream call allows the attacker to extract the keystream by XOR-ing the sniffed traffic with the keystream call plaintext,” ReVoLTE researchers explained. “The keystream block is then used to decrypt the corresponding captured target ciphertext. The attacker thus computes the target call plaintext.”
While ReVoLTE exploits the incorrect implementation of LTE, Johns Hopkins’ Green said some of the fault lies in the opaqueness of the standard itself, a shortcoming that he likens to “begging toddlers not to play with a gun.”
“Inevitably, they’re going to do that and terrible things will happen,” he wrote. “In this case, the discharging gun is a keystream re-use attack in which two different messages get XORed with the same keystream bytes. This is known to be utterly devastating for message confidentiality.”
The researchers provide several suggestions that cellular providers can follow to fix the problem. Obviously, that means not reusing the same keystream, but it turns out that’s not as straightforward as it might seem. A short-term countermeasure is to increase the number of what are known as radio bearer identities, but because there’s a finite number of these, carriers should also use inter-cell handovers. Normally, these handovers allow a phone to remain connected as it transfers from one cell to another. A built-in key reuse avoidance makes the procedure useful for security as well.
“[As] a long-term solution, we recommend specifying mandatory media encryption and integrity protection for VoLTE,” the researchers wrote. “This provides long-term mitigation for known issues, e. g., key reuse, and missing integrity protection on the radio layer, and introduces an additional layer of security.”
READ MORE HERE