How to eliminate the default route for greater security
If portions of enterprise data-center networks have no need to communicate directly with the internet, then why do we configure routers so every system on the network winds up with internet access by default?
Part of the reason is that many enterprises use an internet perimeter firewall performing port address translation (PAT) with a default policy that allows access the internet, a solution that leaves open a possible path by which attackers can breach security.
+Also on Network World: IPv6 deployment guide; What is edge computing and how it’s changing the network?+
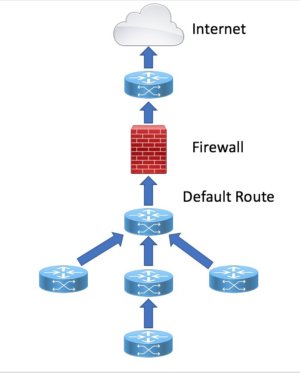
Traditional Network Design with Default Routing
Network engineers configure static or dynamic (e.g. BGP) routing with upstream ISPs on the routers northbound of the firewall. It is tradition and habit for network engineers also configure a static default route (e.g. 0.0.0.0/0, ::/0) toward the firewall on the router internal to the firewall. As shown in the below diagram, this internal router then redistributes this static default into the internal dynamic routing protocol (e.g. OSPF, EIGRP). Therefore, when any internal router receives a packet destined for an IP address that does not appear in its routing table, the packet is forwarded using the default route (e.g. Gateway of Last Resort). As a result, every system on every internal network has a path to the Internet whether it needs it or not.
Removing the Default Gateway
Now, the end-nodes connected to these internal edge routers also use a default gateway that directs all non-local network traffic toward the first-hop router. For access networks, the end-user devices receive this default route from DHCP options. Although it is possible to remove the default route from all hosts, it would be an administrative burden to do this manually for each-and-every server. It would be easier to configure the presence or absence of the default route on a limited set of data center network equipment to achieve the same result.
READ MORE HERE