How to hack your own Wi-Fi network
One way to bolster your understanding of Wi-Fi security is to do some hacking yourself. That doesn’t mean you should infiltrate a company’s network or snoop on a neighbor’s setup. Rather, ethical hacking and legitimate Wi-Fi penetration testing – done in cooperation with the network owner – can help you learn more about the strengths and limitations of wireless security. Understanding potential Wi-Fi vulnerabilities can help you to better protect the networks you manage and ensure safer connections when you access other wireless networks.
Start with a Wi-Fi stumbler
General purpose Wi-Fi stumblers are the simplest and most innocent tools to add to your pen testing kit. Though typically passive tools, they serve an important purpose. They allow you to see what access points (AP) are nearby and their details, such as the signal level, security/encryption type, and media access control (MAC) address. It’s a tool even a hacker would utilize to find the next victim.
Using a stumbler, you might find networks set with weak security, like WEP or the original version of WPA. Or, a walk throughout a property might reveal rogue APs set up by employees or others that could be opening your network to attack. Even if there are APs set with a hidden or non-broadcasted service set identifier (SSID), some stumblers can quickly reveal them.
Vistumbler is an open source Windows application that displays the basic AP details, including the exact authentication and encryption methods, and can even speak the SSID and signal level.
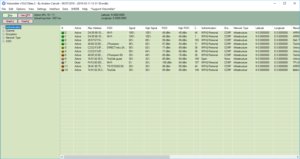 Vistumbler
Vistumbler
Vistumbler is a Wi-Fi stumbler that displays details of nearby wireless networks.
It also displays graphs of signal levels and channel usage. It’s highly customizable and offers flexible configuration options. Vistumbler supports AP names to help distinguish them, also helping to detect rogue access points. It also supports GPS logging and live tracking within the application using Google Earth.
If don’t want to lug around a laptop and have a mobile device, consider using the AirPort Utility on your iOS device or a download an app on your Android. If a free stumbling app doesn’t cut it, check out our review of some commercial options.
Wifi Analyzer is a free Android app you can use for finding access points on your Android-based smartphone or tablet. It lists the basic details for access points on the 2.4-GHz band and on supported devices on the 5-GHz band as well.
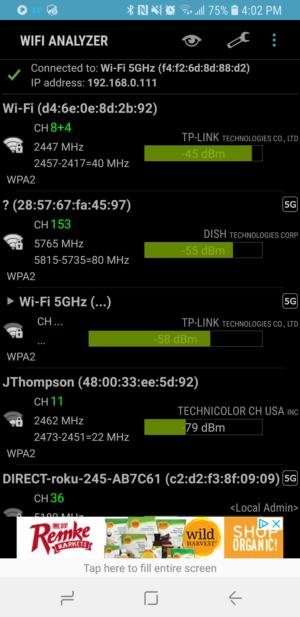 farproc
farproc
WiFi Analyzer is an Android app that shows nearby wireless channels.
You can export the access point list (in XML format) by sending it to email or another app or take a snapshot of the screens. It also features graphs showing signals by channel, history and usage rating, and it has a signal meter feature to help find access points.
Wi-Fi sniffers
Wi-Fi sniffers go further than stumblers. Instead of just grabbing the network details, sniffers capture and show and/or analyze the raw packets sent over the air waves. Captured traffic can be imported into other tools, such as an encryption cracker. Or, some sniffers have the functionality included to do some analysis or cracking as well. In addition, some sniffers look for and report only on certain network traffic, such as those designed to reveal passwords sent in clear-text.
CommView for WiFi is a popular commercial Wi-Fi sniffer and analyzer that offers a 30-day limited trial. It has a stumbler feature to show network details, plus channel utilization stats and graphs. It can track IP connections and records any VoIP sessions. The tool also lets you capture and see the raw packets.
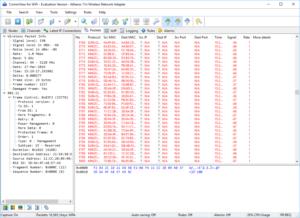 CommView for WiFi
CommView for WiFi
CommView for WiFi is a wireless sniffer available for trying out through a 30-day limited trial.
If you’re connected to a Wi-Fi network, you can input its PSK passphrase so the decrypted packets will be shown. You can also set rules to filter the data you see and set alarms to track rogue devices. Other cool features include a traffic generator to do some spoofing, node reassociation to manually kick clients off, and TCP reconstruction to better view the captured data (text or photos).
Kismet is an open source Wi-Fi stumbler, packet sniffer, and intrusion-detection system that can run on Windows (with WSL framework), Mac OS X, Linux, and BSD. It shows the access point details, including the SSID of “hidden” networks. It can also capture the raw wireless packets, which you can then import into Wireshark, TCPdump, and other tools. In Windows, Kismet only works with CACE AirPcap wireless adapters due to the limitation of Windows drivers. It does, however, support a variety of wireless adapters in Mac OS X and Linux.
Tools reveal Wi-Fi details
WirelessKeyView from NirSoft is a simple yet neat tool that lists all the WEP, WPA, and WPA2 keys or passphrases stored on the Windows computer you run it on.
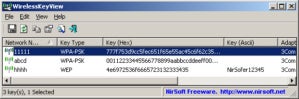 NirSoft
NirSoft
WirelessKeyView doesn’t capture anything from the airwaves, but it demonstrates a significant Wi-Fi vulnerability.
Although it was pretty easy to reveal saved keys in Windows 7 and prior versions via the usual Windows GUI, Microsoft made it more difficult in Windows 10. WirelessKeyView quickly gets you an exportable list of all saved networks no matter the OS versions.
Tools like WirelessKeyView can reveal how a compromised or stolen device may contain sensitive information beyond documents. It also shows the importance of using 802.1x authentication, where users would have individual login credentials for the Wi-Fi and aren’t susceptible to this type of issue.
Aircrack-ng is an open source suite of tools to perform WEP and WPA/WPA2-Personal key cracking.
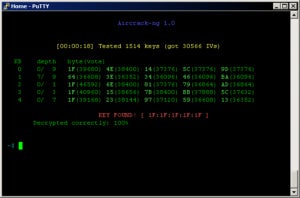 Aircrack-ng
Aircrack-ng
Aircrack-ng is a popular Wi-Fi penetration testing app that’s available as a stand-alone tool and included in many toolkits.
It runs on Windows, Mac OS X, Linux, and OpenBSD. It’s also downloadable as a VMware image and Live CD. You can view nearby Wi-Fi networks, including hidden or non-broadcasted SSIDs. You can also capture the raw packets, inject and replay traffic, and possibly crack the encryption keys once enough packets have been captured.
Get a full software suite with a Linux distro
One of the most popular pen testing distros is Kali Linux. In addition to a typical Linux OS install on a computer, you can make a live bootable disc or download VMware or VirtualBox images. It contains a huge list of security and forensics tools, some of which you can utilize for Wi-Fi pen testing. For instance, Kismet and Aircrack-ng tools are included.
A few of the other Wi-Fi tools included with Kali Linux are Reaver to hack a network via an insecure WPS PIN, FreeRadius-WPE to perform man-in-the-middle attacks on 802.1X authentication, and Wifi Honey to create a honey pot to lure in clients to connect to a fake AP in hopes of capturing their traffic and performing man-in-the-middle attacks.
Go all out with a hardware tool
If you’re really serious about wireless security and playing around with its vulnerabilities, you have to get a taste of WiFi Pineapple. It’s a hardware-based solution specifically designed for Wi-Fi auditing and pen testing. You can scan, target, intercept, and report on many wireless threats and weaknesses.
WiFi Pineapple has a router-like look and feel, including its web GUI.
 WiFi Pineapple from Hak5
WiFi Pineapple from Hak5
The WiFi Pineapple TETRA device allows you to perform some really cool wireless tricks.
You can do things like see client details of each AP, send de-authentication packets, and automatically create fake APs by mimicking nearby SSIDs for some man-in-the-middle fun. You can also capture the web browsing data of others and spoof DNS replies to confuse users or send them to spoof sites.
WiFi Pineapple currently offers two hardware options: a pocket-sized single-band NANO starting at $99.99 and a router-like dual-band TETRA (see a full review) starting at $199.99.
Eric Geier is a freelance tech writer. Keep up with his writings on Facebook or Twitter. He’s also the founder of NoWiresSecurity, which provides a cloud-based Wi-Fi security service, and Wi-Fi Surveyors, which provides RF site surveying.
READ MORE HERE



