How to Improve Cybersecurity Awareness and Training

Cybersecurity Awareness Month
Bill Malik, former Research Director at Gartner, discusses how to leverage the Capability Maturity Model to create an effective awareness program.
Safety training programs have been around since the invention of fire. They were the first step in a series of engineering and procedural measures to mitigate the consequences of fire, and led to such innovations as
- Placing flammable materials away from the fire
- Building a border around the fire to prevent its spread
- Using durable materials to guide the fire towards the object being cooked or smelted
- Keeping fire-suppressants nearby to put out the fire when it was no longer wanted
These reasonable measures kept prior generations safe. The people who developed them used their experience and available materials to enhance the value that fire brought to civilization. Since then, awareness and training program evolved with our understanding of fire.
In cybersecurity, awareness and training programs have become a grab-bag of half-measures that haven’t made it to formal procedures, well-defined product requirements, or clear policies. When something goes wrong, if there is no obvious resolution, organizations default is to put some generic solution into the “awareness and training” bucket. Someone later may take the time to refine that lesson observed into something concrete, but there never seems to be enough time to fully develop that solution. This activity, of taking a lesson partially learned and lump it into the grab-bag of awareness and training, will always be ineffective.
Creating an effective cybersecurity awareness and training program
A better and more effective use of a cybersecurity after-action report will be:
- Define a formal procedure to prohibit the set of circumstances or actions that led to the breach or fault.
- Develop a set of product requirements that will guide the developers to improve the user interface toward the more desirable outcome (“nudge”).
- Enhance existing processes to clarify the correct response or behavior to the problematic or contradictory symptoms.
- Develop a runbook codifying the appropriate.
How do we get there? Achieving an effective and fully-developed awareness and training program requires a high level of process maturity within the organization. The effective model for this process follows from the Capability Maturity Model (CMM), shown in this diagram:
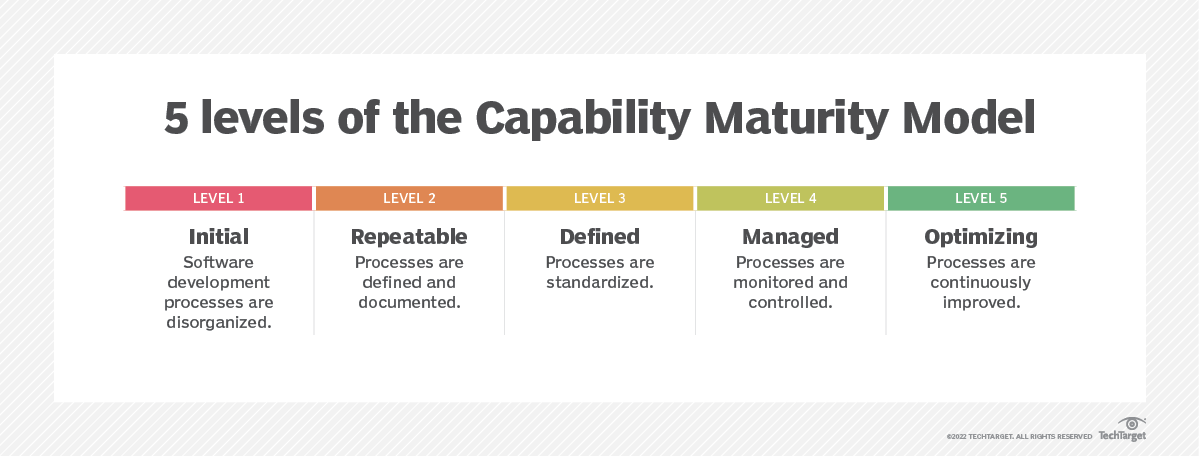
The Capability Maturity Model (CMM) was developed and sponsored by the Software Engineering Institute (SEI), a research and development center sponsored by the U.S. Department of Defense (DOD) and now part of Carnegie Mellon University. It is now managed by ISACA.
In brief, the CMM describes five levels of organizational response to problems:
- Initial state treats problems as emergencies for which the organization has no thought-out response. The reaction to a problem is a crisis.
- Managed state usually relies on an individual with specialized expertise who uses their tacit knowledge to deal with the problem.
- Defined state makes use of explicit knowledge, with comprehensive and complete documentation to diagnose and respond to the incident.
- Quantitatively Managed maturity performs actions such as first-failure diagnosis to eliminate the possibility of future occurrences of the incident.
- Optimizing maturity treats a problem as a symptom of a procedural defect and inspires both the corrective action (fix the problem) and the procedural improvements to prevent the circumstances that allowed the problem to happen (fix the process).
A mature awareness and training program incorporates findings and lessons from an incident into one of the top three categories.
The US military distinguishes between “lessons observed” – passively noting that a failure happened, and “lessons learned” – taking the consequences of a failure or problem and modifying processes, procedures, and tools to mitigate or eliminate the circumstances that led to the failure.
Currently organizations tend toward:
- Write up a description of a serious breach.
- Craft some ad-hoc possible general improvement.
- Add that to the awareness and training program.
- Call it a day.
The contents of the awareness and training program are only useful if they have been validated and exercised.
However, getting programs validated and exercised is a challenge of its own. Without buy-in from staff, even the best technical measures will be ineffective. A report from the European Union Agency for Cybersecurity (ENISA) analyzed the human aspects of cybersecurity to help practitioners take significant steps towards helping employees to act in a more secure way. The report includes the following recommendations for CISOs and security specialists:
- Calculate the impact of your policies. People are smart at work. They know the organization’s goals and metrics. If the security policy gets in the way of getting the job done, they will either imitate what their boss does, or avoid it altogether. According to the report, CISOs need to fully understand the time and effort compliance requires before putting a security measure in place.
- Be visible and approachable. CISOs should be “security cheerleaders, not policemen.” They need to listen and negotiate with staff rather than “throttle innovation and experimentation.”
- You need soft skills. Developing soft skills takes time and effort for most people, but it is a necessity in this role if you wish to be an effective leader.
- Stop verbally bashing people. People do not respond to fear, they work to avoid it. Awareness campaigns relying on scaring folks don’t connect. Avoid phrases like “humans/users are the weakest link” or referring to users as “the problem.”
Final thoughts
If your security tool makes you choose between doing the right thing for the job and doing the safe thing, get a better tool. If your business process makes you choose between doing the productive thing and doing the secure thing, fix your business process. And finally, only put material into the awareness and training program after it has been verified and proven. Given the right tools and processes, you can ensure that your people will remain the strongest link.
What do you think? Let me know in the comments below or reach me @wjmalik@noc.social.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




