How to use Google’s new dependency mapping tool to find security flaws buried in your projects
Google has built an online tool that maps out all the dependencies in millions of open-source software libraries and flags up any unpatched vulnerabilities.
This is useful for finding out what exactly is inside the libraries used by your programming projects, and crucially, whether they contain hidden security bugs that haven’t been fixed. Thus, you can choose another set of packages, or help get the holes patched, to avoid leaving your application exploitable.
These days, when you pull a library into a project, you’re typically pulling in dozens of dependencies and sub-dependencies of that library. And any of these components could – and do – contain security holes, which may leave the parent program vulnerable to attack.
These dependencies can also break or vanish, preventing code from building, deploying, or building as expected. Programs can import out-of-date libraries and not stay up to date, meaning they miss out on bug fixes, security patches, and new features.
It’s safe to say developers rarely know what they’re getting into, or what issues lie beneath the surface, when they add a library to their project. This fragile state of software engineering affects commercial applications as well as free software and it’s an issue Googlers are increasingly vocal about.
Goals
Which leads us to the web giant’s experimental dependency exploration tool, dubbed Open Source Insights, which was announced today and is available at deps.dev. You can search for a package, and browse its contents as a table or a graph, and any known security holes in those dependencies are flagged up.
We’re told the service is, right now, indexing, scanning, and monitoring 1.63 million JavaScript libraries in npm, 624,000 Go modules, 404,000 Maven artifacts of Java code, and 62,000 Rust Cargo crates. PyPi and NuGet packages are set to be added next. It is also free to use.
“Open Source Insights continuously scans millions of projects in the open source software ecosystem, gathering information about packages, including licensing, ownership, security issues, and other metadata such as download counts, popularity signals, and OpenSSF Scorecards,” said the project’s Andrew Gerrand, Michael Goddard, Rob Pike, and Nicky Ringland in their announcement.
“It then constructs a full dependency graph — transitively tracking dependencies, dependencies’ dependencies, and so on — and incorporates the metadata, then publishes it so you can see how it all might affect your software. And the information it provides is continually updated.”
How well does it work?
Your humble vulture decided to take the service out for a spin with a library, picking off the top of his head a useful Rust crate called tui.
This software can be used to create great looking text-based user interfaces within a terminal. It’s been starred more than 5,100 times on GitHub, has scores of contributors, and is used to build various apps, including a terminal-based Spotify client.
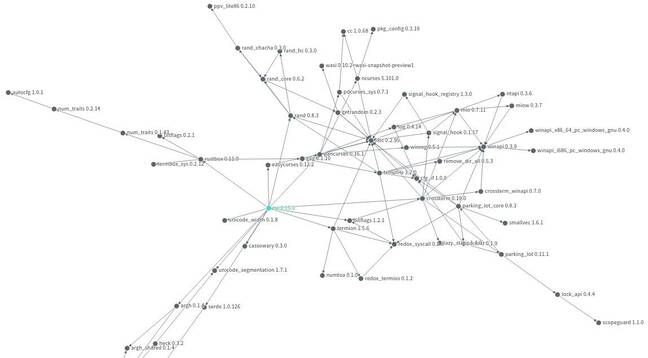
Entering tui into the deps.dev search bar, and selecting the Cargo crate, brings up the library’s dashboard. Clicking on the dependencies tab shows a table of its components, which can be searched, and clicking on the graph button on the right opens a visualization of tui‘s libraries.
You can zoom in and out by scrolling in the graph view, and move points around by click-and-dragging them. Each crate, starting with tui, has lines with arrowheads pointing to its dependencies. You can see, for instance, the chain of dependencies to the crates that handle Windows API calls on that operating system, and all the paths leading to libc.
More importantly, and unexpectedly for a Rust project, Google’s service shows the latest version of tui, 0.15.0, has a couple of security holes.
However, it’s clear these are in tui‘s dependencies, and programmers who use the interface library in their applications may not be aware of the buried bugs.
One of these vulnerabilities is RUSTSEC-2019-0005 in tui‘s pancurses dependency. This library is one of the available backends for tui that takes care of sending the necessary character sequences to the terminal, be it on Linux or Windows, to display the text-based user interface.
The bug can be exploited in “a format string attack, which trivially allows writing arbitrary data to stack memory.” This is present in version 0.16.1 of pancurses, the latest version and the one used by tui in its latest release.
That suggests it may be possible to hijack an application that uses tui with pancurses by giving it a string of data, such as a specially crafted filename, or contents of a file, or information from the network, that takes advantage of the aforementioned security oversight.
The other vulnerability is RUSTSEC-2019-0006, which is in the ncurses crate that is a thin wrapper around the ncurses C library. This bug is present in the latest version of the wrapper crate, 5.101.0, and in the version used by pancurses, version 5.91.0. It is exploitable through buffer overflow and format string attacks, and so like the above flaw, may be potentially used to hijack applications using maliciously crafted input data.
The two bugs are documented here in detail with a proof-of-concept crash exploit, if you’re interested. Even if they are not practicably exploitable in real-world applications, they still serve as an example of how Google’s Open Source Insights can be used to discover potential security flaws lurking in your project’s dependency graph.
There are other dependency vulnerability scanners out there – GitHub‘s springs to mind. OWASP has one. Snyk, too. Feel free to share your recommendations in the comments. ®
READ MORE HERE