Hundreds Of WordPress Sites Infected By Recently Discovered Backdoor

Malware that exploits unpatched vulnerabilities in 30 different WordPress plugins has infected hundreds if not thousands of sites and may have been in active use for years, according to a writeup published last week.
The Linux-based malware installs a backdoor that causes infected sites to redirect visitors to malicious sites, researchers from security firm Dr.Web said. It’s also able to disable event logging, go into standby mode, and shut itself down. It gets installed by exploiting already-patched vulnerabilities in plugins that website owners use to add functionality like live chat or metrics-reporting to the core WordPress content management system.
“If sites use outdated versions of such add-ons, lacking crucial fixes, the targeted web pages are injected with malicious JavaScripts,” Dr.Web researchers wrote. “As a result, when users click on any area of an attacked page, they are redirected to other sites.”
Searches such as this one indicate that more than 1,300 sites contain the JavaScript that powers the backdoor. It’s possible that some of those sites have removed the malicious code since the last scan. Still, it provides an indication of the reach of the malware.
The plugins exploited include:
- WP Live Chat Support Plugin
- WordPress – Yuzo Related Posts
- Yellow Pencil Visual Theme Customizer Plugin
- Easysmtp
- WP GDPR Compliance Plugin
- Newspaper Theme on WordPress Access Control (vulnerability CVE-2016-10972)
- Thim Core
- Google Code Inserter
- Total Donations Plugin
- Post Custom Templates Lite
- WP Quick Booking Manager
- Facebook Live Chat by Zotabox
- Blog Designer WordPress Plugin
- WordPress Ultimate FAQ (vulnerabilities CVE-2019-17232 and CVE-2019-17233)
- WP-Matomo Integration (WP-Piwik)
- WordPress ND Shortcodes For Visual Composer
- WP Live Chat
- Coming Soon Page and Maintenance Mode
- Hybrid
- Brizy WordPress Plugin
- FV Flowplayer Video Player
- WooCommerce
- WordPress Coming Soon Page
- WordPress theme OneTone
- Simple Fields WordPress Plugin
- WordPress Delucks SEO plugin
- Poll, Survey, Form & Quiz Maker by OpinionStage
- Social Metrics Tracker
- WPeMatico RSS Feed Fetcher
- Rich Reviews plugin
“If one or more vulnerabilities are successfully exploited, the targeted page is injected with a malicious JavaScript that is downloaded from a remote server,” the Dr.Web writeup explained. “With that, the injection is done in such a way that when the infected page is loaded, this JavaScript will be initiated first—regardless of the original contents of the page. At this point, whenever users click anywhere on the infected page, they will be transferred to the website the attackers need users to go to.”
The JavaScript contains links to a variety of malicious domains, including:
lobbydesires[.]com
letsmakeparty3[.]ga
deliverygoodstrategies[.]com
gabriellalovecats[.]com
css[.]digestcolect[.]com
clon[.]collectfasttracks[.]com
Count[.]trackstatisticsss[.]com
The screenshot below shows how the JavaScript appears in the page source of the infected site:
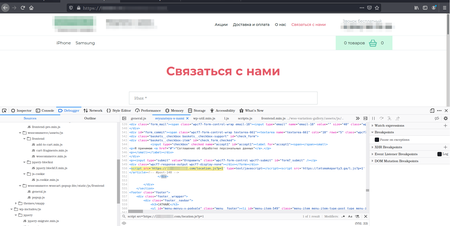
The researchers found two versions of the backdoor: Linux.BackDoor.WordPressExploit.1 and Linux.BackDoor.WordPressExploit.2. They said the malware may have been in use for three years.
WordPress plugins have long been a common means for infecting sites. While the security of the main application is fairly robust, many plugins are riddled with vulnerabilities that can lead to infection. Criminals use infected sites to redirect visitors to sites used for phishing, ad fraud, and distributing malware.
People running WordPress sites should ensure that they’re using the most current versions of the main software as well as any plugins. They should prioritize updating any of the plugins listed above.
READ MORE HERE
