Identity-Focused Security Controls Prevail
As the military saying goes, “No plan survives contact with the enemy.” We spend a great deal of time teaching our military leaders to improvise, adapt, and overcome as a way to deal with this reality. For many of us, the COVID-19 pandemic induced an instant shift to a fully remote workforce and presented a challenge we hadn’t prepared for. New research provides some insight into just how well we’re improvising, adapting, and overcoming.
In spite of transitioning to a fully remote workforce almost overnight as a result of the pandemic, according to the “2021 Trends in Securing Digital Identities” report, 79% of organizations suffered an identity-related breach within the last two years. Surprisingly, this response is identical to the results of a similar 2020 survey conducted pre-pandemic. This is an unexpected win given the previously mentioned drastic change to the way we all work. If breaches stayed flat, what did change? Eighty-three percent of respondents say the shift to remote work increased the number of identities in their organization, and their confidence in the ability to manage employee identities dropped significantly, from 49% to 32%.
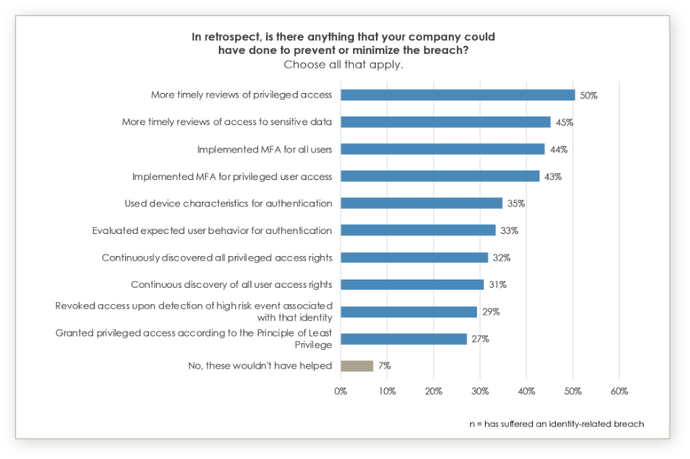
According to the same report, 93% believe they may have prevented or minimized security breaches if they had implemented some specific identity-related security outcomes. That’s a key takeaway for how to mitigate the risk of a future attack — at least those we can anticipate today. For security practitioners, it’s about putting up enough roadblocks to slow down the attackers and make it harder for them. They might even decide to move on to easier targets.
Putting Together Your Identity Security Road Map
Security is an organizational mindset. It’s important to establish a common security language, a security conscious culture and an approved set of identity-related security controls. To make the task less daunting, these core identity-related outcomes should be prioritized and adopted throughout the organization. Resources like theIDSA’s Identity Defined Security Outcome library are a great place to start, but organizations will need to prioritize implementation based on their unique situation.
- Multifactor authentication (MFA). Deploying MFA capabilities for all users can’t be stressed enough. Some companies avoid it because users don’t like it or because it slows down productivity flow, yet it is the one outcome that should be deployed for every resource in an organization.
- Privileged access reviews. Accounts with privileged access are at the top of the food chain for cyberattackers. Staying on top of who has expanded access is critical to protecting an organization’s most sensitive assets.
- Revoke access. Revoke access immediately if there is high risk associated with an identity or if the identity is no longer affiliated with the organization. High-profile data breaches and cyber incidents like SolarWinds are believed to be caused, in part, due to an orphaned identity.
- Device characteristics for authentication. Information about the device being used to access resources can provide important clues as to whether the device or the identity has been compromised. One extra step in the authentication process because a device seems suspicious could prevent a breach.
- User behavior. All users have unique characteristics, whether that means the time of day they access accounts or their keystrokes when typing. Recognizing user behavior could help prevent many types of attacks that use a valid username and password.
Even with broad adoption of these security controls, we cannot rely on technology alone to prevent an incident. By establishing a security-oriented culture, users are likely to be more vigilant in protecting their corporate identities and think twice before clicking on a suspicious email or an unknown attachment. As new technologies are introduced into the organization, through IT or a business function, the common language and adopted controls will also allow stakeholders to ensure they are not exposing the organization to unnecessary risk.
Identity-related attacks continue to be the hacker’s favorite technique, as stolen or compromised valid credentials are an easier and stealthier way of gaining persistent access. The last 18 months have highlighted the need for improved identity security, yet research suggests that we are focusing our security efforts in the right places and should continue to prioritize strong identity-focused security controls.
Read More HERE
