Improve cyber supply chain risk management with Microsoft Azure
For years, Microsoft has tracked threat actors exploiting federal cyber supply chain vulnerabilities. Supply chain attacks target software developers, systems integrators, and technology companies. Tactics often include obtaining source code, build processes, or update mechanisms to compromise legitimate applications. This is a key concern for government cybersecurity in the cloud, as the expanding digital estate requires movement towards a Zero Trust security model.
There are several techniques to attack cyber supply chains in Information Communications and Technology (ICT) products and services. Supply chain attacks are most concerning because they target vulnerabilities in your infrastructure before you even deploy your assets and software.
Attackers can:
- Compromise software building tools to ensure that their malware is imprinted into all software generated from the building tools.
- Replace software update repositories with malicious replicas that distribute malware across entire software ecosystems.
- Steal code-signing certificates to make malicious software appear as legitimate code.
- Intercept hardware shipments to inject malicious code into hardware, firmware, and field-programmable gate arrays (FPGAs).
- Pre-install malware onto IoT devices before they arrive to target organizations.
Managing Supply Chain Risk Management (SCRM) to defend against supply chain attacks
Defending against supply chain attacks requires a comprehensive approach to managing Supply Chain Risk Management (SCRM). Federal risk managers must deploy strong code integrity policies and technical screening controls to ensure their software complies with organizational directives such as applying NIST SP 800-53A security controls for Federal Information Security Management Act (FISMA) compliance. Code integrity requires full non-repudiation of software to validate information producer associations, identity, and chain of custody for systems and components (NIST SP 800-161, 2015). One critical opportunity for addressing code integrity in your supply chain is to implement and adhere to a secure software development lifecycle for applications that you develop in-house and that you acquire from third-party supply chain partners.
Microsoft continues to use the Security Development Lifecycle, a fundamental process of continuous learning and improvement in the security, integrity, and resiliency of our enterprise applications. We require supply chain providers to adhere to these practices as well.
Organizations should employ asset monitoring and tracking systems such as radio-frequency identification (RFID) and digital signatures to track hardware and software from producers to consumers to ensure system and component integrity. FIPS 200 specifies that federal organizations “must identify, report, and correct information and information system flaws in a timely manner while providing protection from malicious code at appropriate locations within organizational information systems” (FIPS 200, 2006).
How Microsoft fights against malware
Microsoft understands how to fight malware and have worked hard for many years to offer our customers leading endpoint protection to defend against increasingly sophisticated attacks across a variety of devices. These efforts have been recognized, for example, in this year’s 2019 Gartner Endpoint Protection Platforms Magic Quadrant. In addition, Microsoft Defender Advanced Threat Protection (ATP) integrates directly with Microsoft Azure Security Center to alert your security teams of threat actors exploiting your vulnerabilities.
Magic Quadrant for Endpoint Protection Platforms.*
Endpoint Protection Platforms can support software development and fight malware, but government organizations must follow recommendations for software vendors and developers by applying patches for operating systems and software, implementing mandatory integrity controls, and requiring Multi-Factor Authentication (MFA) for administrators.
Azure Security Center Recommendations help government organizations eliminate security vulnerabilities before an attack occurs by facilitating actions to secure resources, including OS vulnerability detection, mandatory controls, and enforcing authentication with MFA and secure access with just-in-time (JIT) virtual machine access.
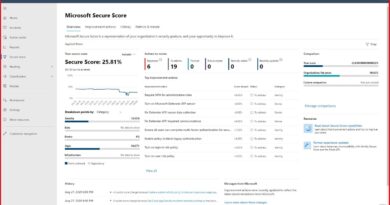
When you remediate recommendations, your Secure Score and your workloads’ security postures improve. Azure Security Center automatically discovers new resources you deploy, assesses them against your security policy, and provides new recommendations for securing them.
Azure Security Center also facilitates cyber learning through gamification. Secure Score allows your SecOps and Security Governance Risk & Compliance (SGRC) teams to remediate vulnerabilities through a points-based system. This capability can enhance system configurations and reinforce supply chain risk management in a single pane of glass for your infrastructure security posture, and even includes a regulatory and compliance dashboard to facilitate federal compliance requirements and can be tailored to your organization.
Security of federal information systems requires compliance with stringent standards such as NIST SP 800-53, FISMA, CIS Benchmarks, and FedRAMP Moderate. Azure Blueprints facilitates compliance with these standards ensuring a secure-by-design approach to federal information security. Azure Blueprints enable cloud architects and information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization’s standards, patterns, and requirements.
Azure Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such as role assignments, policy assignments, and Azure Resource Manager templates. Azure Blueprints also provide recommendations and a framework to directly apply compliance requirements to your environment while monitoring configurations through Continuous Monitoring (CM).
Employing a comprehensive monitoring program
Protecting your supply chain also requires a comprehensive monitoring program with cyber incident response and security operations capabilities. Azure Sentinel is a cloud-native security information and event manager (SIEM) platform that uses built-in artificial intelligence (AI) to help analyze large volumes of data across an enterprise—fast. Azure Sentinel aggregates data from all sources, including users, applications, servers, and devices running on-premises or in any cloud, letting you reason over millions of records in a few seconds.
Azure Sentinel leverages the Microsoft Graph, which detects threats, reduces false positives, and puts your responders on target. Azure Sentinel Workbooks optimize productivity with dozens of built in dashboards to enhance security monitoring.
Azure Sentinel Analytics allow your cyber defenders to employ proactive alerting to detect threats impacting your supply chain security. Azure Sentinel Playbooks includes over 200 connectors to leverage full automation through Azure Logic Apps. This powerful capability allows federal agencies to compensate for the cyber talent gap with Security Automation & Orchestration Response (SOAR) capabilities while leveraging machine learning and AI capabilities. Azure Sentinel deep investigation allows your incident response teams to dig into incidents and identify the root cause of attacks.
Azure Sentinel’s powerful hunting search-and-query tools are based in the MITRE ATT&K Framework, allowing your responders to proactively hunt threats across the network before alerts are triggered. The Azure Sentinel community is growing on GitHub and allows your team to collaborate with the information security community for best practices, efficiencies, and security innovation.

Cyber Supply Chain Risk Management (SCRM) is a growing concern within the federal sector. Microsoft is committed to bolstering government cybersecurity in the cloud. Microsoft Azure goes the distance to protect your network against supply chain attacks through Microsoft Defender ATP’s industry leading Endpoint Protection Platform, Azure Security Center’s comprehensive continuous monitoring platform, Azure Blueprints approach to rapidly deploying a compliant cloud, and Azure Sentinel’s cloud-native SIEM that harnesses the limitless power of the cloud through threat intelligence, machine learning, AI, and automation.
Learn more about government cybersecurity in the cloud with Microsoft
Here are some of the best resource to learn more about government cybersecurity in the cloud with Microsoft:
Also, join us for the Microsoft Ignite Government Tour in Washington, D.C., February 6, 2020.
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and updates on cybersecurity.
Are you a federal government agency that needs help with cybersecurity? Reach out to TJ Banasik or Mark McIntyre for additional details on the content above, or if you have any other questions about Microsoft’s cybersecurity investments for the federal government.
*This graphic was published by Gartner, Inc. as part of larger research documents and should be evaluated in the context of the entire document. The Gartner documents are available upon request from Microsoft. Gartner does not endorse any vendor, product, or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
READ MORE HERE