In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks
Our experience in detecting and blocking threats on millions of endpoints tells us that attackers will stop at nothing to circumvent protections. Even one gap in security can be disastrous to an organization.
At Microsoft, we don’t stop finding new ways to fill in gaps in security. We go beyond strengthening existing defenses by introducing new and innovative layers of protection. While our industry-leading endpoint protection platform stops threats before they can even run, we continue improving protections for instances where sophisticated adversarial attacks manage to slip through.
Multiple layers of protection mean multiple hurdles that attackers need to overcome to perpetrate attacks. We continuously innovate threat and malware prevention engines on the client and in the cloud to add more protection layers that detect and block sophisticated and evasive threats before they can even run.
In recent months, we introduced two machine learning protection features within the behavioral blocking and containment capabilities in Microsoft Defender Advanced Threat Protection. In keeping with the defense in depth strategy, coupled with the “assume breach” mindset, these new protection engines specialize in detecting threats by analyzing behavior, and adding new layers of protection after an attack has successfully started running on a machine:
- Behavior-based machine learning identifies suspicious process behavior sequences and advanced attack techniques observed on the client, which are used as triggers to analyze the process tree behavior using real-time machine learning models in the cloud
- AMSI-paired machine learning uses pairs of client-side and cloud-side models that integrate with Antimalware Scan Interface (AMSI) to perform advanced analysis of scripting behavior pre- and post-execution to catch advanced threats like fileless and in-memory attacks
The figure below illustrates how the two behavior-based machine learning protections enrich post-breach detections:
Figure 1. Pre and post-execution detection engines in Microsoft Defender ATP’s antivirus capabilities
The pre-execution and post-execution detection engines make up two important components of comprehensive threat and malware prevention. They reflect the defense in depth principle, which entails multiple layers of protection for thorough, wide-range defense.
In detecting post-execution behavior, using machine learning is critical. Many attack techniques are also used by legitimate applications. For example, a very common, documented method used by both clean applications and malware is creating a service for persistence.
To distinguish between malicious and clean applications when an attack technique is observed, Windows Defender Antivirus monitors and sends suspicious behaviors and process trees to the cloud protection service for real-time classification by machine learning. Cloud-based post-execution detection engines isolate known good behaviors from malicious intent to stop attacks in real time.
Within milliseconds of an attack technique or suspicious script execution being observed, machine learning classifiers return a verdict and the client blocks the threat. The pre-execution models then learn from these malicious blocks afterwards to protect Microsoft Defender ATP customers before attacks can begin executing new cycles of infection.
How behavioral blocking and containment protected 100 organizations from credential theft
In early July, attackers launched a highly targeted credential theft attack against 100 organizations around the world, primarily in the United Arab Emirates, Germany, and Portugal. The goal of the attack was to install the notorious info-stealing backdoor Lokibot and to exfiltrate sensitive data.
Behavioral blocking and containment capabilities in Microsoft Defender ATP detected and foiled the attack in its early stages, protecting customers from damage.
Spear-phishing emails carrying lure documents were sent to the target organizations; in one instance, three distinct highly targeted emails with the same lure document were delivered to a single pharmaceutical ingredient supplier. The attacker used pharmaceutical industry jargon to improve the credibility of the email and in one case requested a quote on an ingredient that the target company was likely to produce.

Figure 2. Multiple spear-phishing emails attempted to deliver the same lure document to the same target
The lure document itself didn’t host any exploit code but used an external relationship to a document hosted on a compromised WordPress website. If recipients opened the attachment, the related remote document, which contained the exploit, was also automatically loaded. This allowed the remote document to take advantage of the previously fixed CVE-2017-11882 vulnerability in Equation Editor and execute code on the computer.

Figure 3. The lure document contains an external reference to the exploit document is hosted on a compromised WordPress website.
Upon successful exploitation, the attack downloaded and loaded the Lokibot malware, which stole credentials, exfiltrated stolen data, and waited for further instructions from a command-and-control (C&C) server.
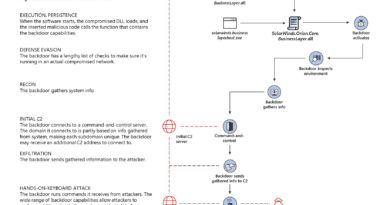
The behavior-based machine learning models built into Microsoft Defender ATP caught attacker techniques at two points in the attack chain. The first detection layer spotted the exploit behavior. Machine learning classifiers in the cloud correctly identified the threat and immediately instructed the client to block the attack. In cases where the attack had proceeded past this layer of defense to the next stage of the attack, process hollowing would have been attempted. This, too, was detected by behavior-based machine learning models, which instructed the clients to block the attack, marking the second detection layer. As the attacks are blocked, the malicious processes and corresponding files are remediated, protecting targets from credential theft and further backdoor activities.
Figure 4. Credential theft attack chain showing multiple behavior-based protection layers that disrupted the attack
The behavior-based blocking raised an “Initial Access” alert in Microsoft Defender Security Center, the console for SecOps teams that gives complete visibility into their environments and across the suite of Microsoft Defender ATP tools that protect their endpoints:


Figure 5. Alert and process tree on Microsoft Defender Security Center for this targeted attack
This attack demonstrates how behavior-based machine learning models in the cloud add new layers of protection against attacks even after they have started running.
In the next sections, we will describe in detail the two machine learning protection features in behavioral blocking and containment capabilities in Microsoft Defender ATP.
Behavior-based machine learning protection
The behavior engine in the Windows Defender Antivirus client monitors more than 500 attack techniques as triggers for analyzing new and unknown threats. Each time one of the monitored attack techniques is observed, the process tree and behavior sequences are constructed and sent to the cloud, where behavior-based machine learning models classify possible threats. Figure 4 below illustrates a more detailed view of our process tree classification path:

Figure 6. Process tree classification path
Behavior-based detections are named according to the MITRE ATT&CK matrix to help identify the attack stage where the malicious behavior was observed:
| Tactic | Detection threat name |
|---|---|
| Initial Access | Behavior:Win32/InitialAccess.*!ml |
| Execution | Behavior:Win32/Execution.*!ml |
| Persistence | Behavior:Win32/Persistence.*!ml |
| Privilege Escalation | Behavior:Win32/PrivilegeEscalation.*!ml |
| Defense Evasion | Behavior:Win32/DefenseEvasion.*!ml |
| Credential Access | Behavior:Win32/CredentialAccess.*!ml |
| Discovery | Behavior:Win32/Discovery.*!ml |
| Lateral Movement | Behavior:Win32/LateralMovement.*!ml |
| Collection | Behavior:Win32/Collection.*!ml |
| Command and Control | Behavior:Win32/CommandAndControl.*!ml |
| Exfiltration | Behavior:Win32/Exfiltration.*!ml |
| Impact | Behavior:Win32/Impact.*!ml |
| Uncategorized | Behavior:Win32/Generic.*!ml |
Since deployment, the behavior-based machine learning models have blocked attacker techniques like the following used by attacks in the wild:
- Credential dumping from LSASS
- Cross-process injection
- Process hollowing
- UAC bypass
- Tampering with antivirus (such as disabling it or adding the malware as exclusion)
- Contacting C&C to download payloads
- Coin mining
- Boot record modification
- Pass-the-hash attacks
- Installation of root certificate
- Exploitation attempt for various vulnerabilities
These blocked behaviors show up as alerts in Microsoft Defender Security Center.

Figure 7. Alert for malicious behavior in Microsoft Defender Security Center
Machine learning protection for scripting engines with AMSI
Through the AMSI integration with scripting engines on Windows 10 and Office 365, Windows Defender Antivirus gains rich insight into the execution of PowerShell, VBScript, JavaScript and Office Macro VBA scripts to cut through obfuscation, protect against fileless attacks, and provide robust defenses against malicious script behavior.
To assist with fileless and evasive script attacks, scripting engines are instrumented to provide both behavior calls and dynamic content calls to the antivirus product. The type of integrations available varies based on the scripting engine. Table 1 below illustrates the current support with the Windows 10 and Office 365, and Figure 5 illustrates an example of the scripting engine dynamic script content and behavior calls for malicious scripts.
| Microsoft AMSI integration point | Dynamic script content calls | Behavior calls |
|---|---|---|
| PowerShell | Y | |
| VBScript | Y | Y |
| JavaScript | Y | Y |
| Office VBA macros | Y | |
| WMI | Y | |
| MSIL .NET | Y |

Figure 8. Example dynamic script content and behavior calls for malicious scripts monitored by AMSI
Our scripting machine learning protection design can be seen in Figure 6 below. We deployed paired machine learning models for various scripting scenarios. Each pair of classifiers is made up of (1) a performance-optimized lightweight classifier that runs on the Windows Defender Antivirus client, and (2) a heavy classifier in the cloud. The role of the client-based classifier is to inspect the script content or behavior log to predict whether a script is suspicious. For scripts that are classified as suspicious, metadata describing the behavior or content is featurized and sent up to the cloud for real-time classification; the metadata that describes the content includes expert features, features selected by machine learning, and fuzzy hashes.

Figure 9. AMSI-paired models classification path
The paired machine learning model in the cloud then analyzes the metadata to decide whether the script should be blocked or not. If machine learning decides to block the file, the running script is aborted. This paired model architecture is used to offload the overhead of running intensive machine learning models to the cloud, and to make use of the global information available about the content through the Microsoft Intelligent Security Graph.
Malicious scripts blocked by AMSI-paired machine models are reported in Microsoft Defender Security Center using threat names like the following:
- Trojan:JS/Mountsi.A!ml
- Trojan:Script/Mountsi.A!ml
- Trojan:O97M/Mountsi.A!ml
- Trojan:VBS/Mountsi.A!ml
- Trojan:PowerShell/Mountsi.A!ml
Behavioral blocking and containment for disrupting advanced attacks
The two new cloud-based post-execution detection engines we described in this blog are part of the behavioral blocking and containment capabilities that enabled Microsoft Defender ATP to protect the 100 organizations targeted in the credential theft attack we discussed earlier. Recently, we also documented how behavior-based protections are important components of the dynamic protection against the multi-stage, fileless Nodersok campaign.
These engines add to the many layers of machine learning-driven protections in the cloud and add protection against threats after they have begun running. To further illustrate how these behavior-based protections work, here’s a diagram that shows the multiple protection layers against an Emotet attack chain:

Figure 10. Multiple layers of behavior-based protection in Windows Defender Antivirus while executing an Emotet attack (SHA-256: ee2bbe2398be8a1732c0afc318b797f192ce898982bff1b109005615588facb0)
As part of our defense in depth strategy, these new layers of antivirus protection not only expand detection and blocking capabilities; they also provide even richer visibility into malicious behavior sequences, giving security operations more signals to use in investigating and responding to attacks through Microsoft Defender ATP capabilities like endpoint detection and response, threat and vulnerability management, and automated investigation and remediation.
Within milliseconds of an attack technique or suspicious script execution being observed, machine learning classifiers return a verdict and the client blocks the threat. Our pre-execution models then learn from these malicious blocks afterwards to protect Microsoft Defender ATP customers before the threats even begin executing.

Figure 11. Multiple layers of malware and threat prevention engines on the client and in the cloud
The impact of the continuous improvements in antivirus capabilities further show up in Microsoft Threat Protection, Microsoft’s comprehensive security solution for identities, endpoints, email and data, apps, and infrastructure. Through signal-sharing across Microsoft services, the richer machine learning-driven protection in Microsoft Defender ATP is amplified throughout protections for various attack surfaces.
Geoff McDonald
with Saad Khan
Microsoft Defender ATP Research
READ MORE HERE