Industry 4.0: CNC Machine Security Risks Part 3

Cyber Threats
This three-part blog series explores the risks associated with CNC machines
In this final installation of our three-part blog series, we lay out countermeasures that enterprises can do to protect their machines. We’ll also discuss our responsible disclosure as well as the feedback we got from the vendors we evaluated.
Countermeasures
We found that only two of the four vendors analyzed support authentication. Neither of them has authentication enabled by default, which leaves the machines vulnerable to attacks by malicious users. Enabling authentication is essential for protecting Industry 4.0 features from abuse.
Resource access control systems are important for reducing the impact of attacks. Many technologies allow access to all a controller’s resources, which can be dangerous. A correct approach is to adopt resource access control systems that grant limited access. This will help to ensure that only authorized users have access to the controller’s resources and that these resources are protected from unauthorized access.
When it comes to integrators and end users, we suggest these countermeasures:
- Context-aware industrial intrusion prevention and detection systems (IPS/IDSs): These devices, which have recently seen a surge in popularity in the catalogues of security vendors, are equipped with network engines that can capture real-time traffic associated with industrial protocols to detect attacks.
- Network segmentation: Correct network architecting is of great importance. As our research has revealed, all the tested machines expose interfaces that could be abused by miscreants.
- Correct patching: Modern CNC machines are equipped with full-fledged operating systems and complex software, which might inevitably contain security vulnerabilities. This was indeed the case with the machines that we tested.
Responsible Disclosure
We contacted the affected vendors while tackling controllers sequentially, with our first contact in November 2021 and the last one in March 2022. The Industrial Control Systems Cyber Emergency Response Team (ICS CERT) at Cybersecurity & Infrastructure Security Agency extended invaluable help during the discussion which we are grateful for.
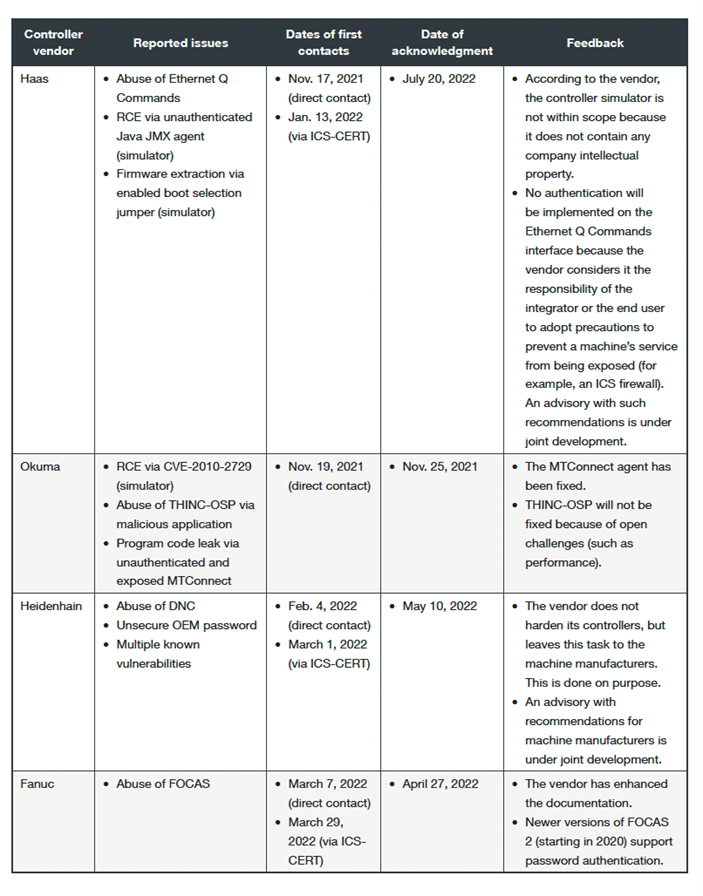
As of this writing, all four vendors have replied to our concerns and most of them have addressed, to varying degrees, our findings in a reasonable time frame. More importantly, all of them have expressed interest in our research and have decided to improve either their documentation or their communication efforts with their machine manufacturers, with the final effort of offering end users more secure solutions.
To learn more about the security risks faced by CNC machines, download our comprehensive report here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE