Info Stealer Targets Facebook Business Accounts
Malicious hackers have been using an advanced information stealer to target Facebook business accounts by using Google ads and fake Facebook profiles that promote games, adult content, and cracked software to lure victims into downloading malicious files.
In a March 7 blog post, researchers at Morphisec said the attackers aim to steal sensitive information, including log-in data, cookies, and Facebook ad and business account information. The info stealer has been used in attacks against critical government infrastructure employees, manufacturing companies and other industries.
The attackers lure a victim to click on a URL from a fake Facebook profile or advertisement to download a Zip file that purports to have an application, game or movie, but in reality executes PHP scripts responsible for stealing and exfiltrating information. The scripts are encoded using different techniques, which makes their analysis and detection harder.
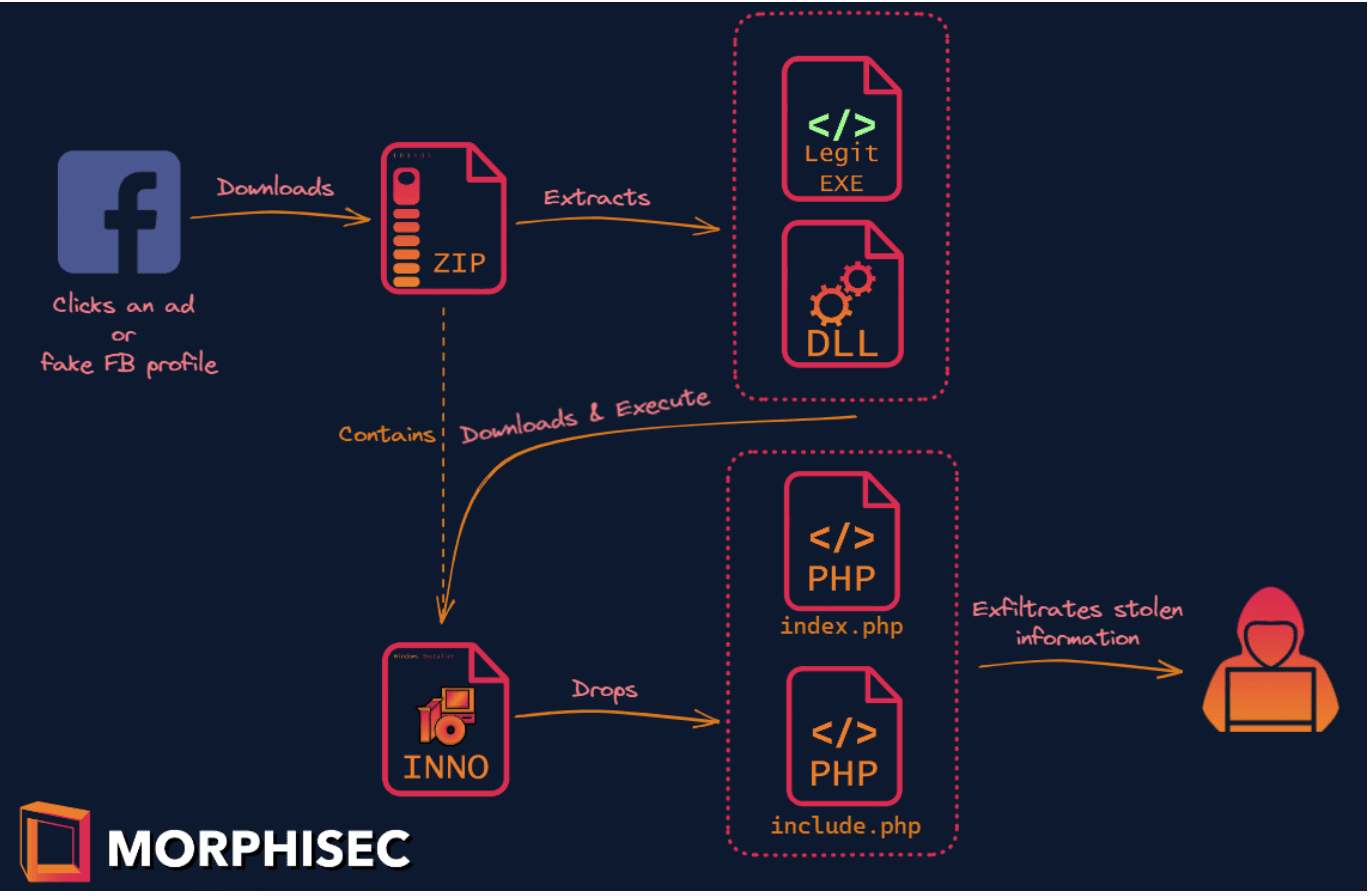
The research highlights how DLL side-loading attacks continue to serve as an effective pathway to trick Windows systems into loading malicious code. The problem could be alleviated if Microsoft enforced search orders for DLL by default, or if developers did it themselves. Often that is not the case.
“Microsoft doesn’t enforce search order for a range of reasons, such as enabling things like portability and backwards compatibility — for example, portable browser applications that use older Microsoft libraries. Security-minded developers may enforce search order within their code. But most developers aren’t security minded,” wrote Morphisec researcher Arnold Osipov. “This enables threat actors to position a malicious payload alongside a legitimate application. Then when an application loads in memory and search order is not enforced, the application loads the malicious file instead of the legitimate one, allowing threat actors to hijack legitimate, trusted, and even signed applications to load and execute malicious payloads.”
The infostealer malware is usually delivered in two parts. First through a legitimate application that is executed when users click on a malicious link but which houses a malicious Dynamic Link Library that can be used to conduct side-loading attacks. That application in turn automatically runs an installer that decompresses a PHP application filled with scripts for stealing and exfiltrating data. Researchers have also seen the loader delivered through other methods, such as Rust and Python-coded commands.
Osipov wrote that security teams can protect against the SYS01 stealer by limiting a user’s rights to download and install programs, implementing other zero trust policies and training staff to avoid clicking on suspicious links.
Simon Kenin, threat lab researcher at Deep Instinct, told SC Media the malware persists on infected computers and communicates with a command-and-control server that could deploy additional malware payloads or even ransomware. He noted that because malware continually evolves over time, this information stealer might add other capabilities that could pose a threat to additional enterprises over time.
Morphisec researchers first began tracking the campaign in November 2022 and have named it “SYS01 stealer.” Another cybersecurity company, Zscaler, spotted the info stealer being used five months earlier in May 2022 in a similar campaign, stealing browser cookies and hijacking authenticated Facebook business accounts to pilfer user information. While that activity was initially attributed to a financially-motivated threat group named Ducktails, researchers at WithSecure later disputed those findings, saying there are no technical indicators and other intelligence indicating overlap between the two campaigns.
John Anthony Smith, chief executive officer of the Conversant Group, added that threat actors are increasingly using ad content to lure users into clicking malicious links. He argued that security teams should view ad links the way they view users opening personal email services like Gmail or Hotmail on a corporate networks and develop similar security policies to compensate.
“Ads, social network platforms, chat applications/services, and any and all platforms that allow communication outside of the corporately sanctioned methods should be blocked,” Smith said.
Mike Parkin, senior technical engineer at Vulcan Cyber, pointed out the original research identified this malware surfacing originally in 2021, and attributed it to a threat group in Vietnam – which was later corrected. This new research from Morphisec picks up that initial campaign from 2021 in May of 2022 and later November of the same year, showing that the threat actor is still active and development of their malware is ongoing.
“Taken as a whole, this highlights how threat actors evolve their tools and focus on specific targets over time. And how challenging it can be to firmly attribute specific malware strains to specific groups, when both the malware and groups that use it are constantly in flux,” Parkin told SC Media.
READ MORE HERE

