Inside the 2022 Email Cyber Threat Landscape

Cyber Threats
Key trends and predictions you should know about
Trend Micro research each year has been publishing our Cloud App Security (CAS) data in the review of the previous year’s email threat landscape. In 2022, we scanned 79B+ emails (a 14% increase from 2021) that our customers received, and CAS would examine to determine if the email was good or malicious. Of this number, 39M+ were classified as high-risk emails and blocked for our customers. Let’s look a bit deeper into these results to give you an understanding of what types of malicious emails attackers are sending these days. In total, Trend Micro blocked over 146B threats targeting our customers in 2022, and email represented 55% of those threats. So, email is still the largest attack vector we see across our customer base.
One very interesting data point was the use of known versus unknown malware attachments. Known malware is easy to detect, so we saw a 32% decrease in the use of this type of attachment. Unknown malware is newly created, zero-hour malware, and as such, it can be harder to detect and defend against. We saw a 46% increase in the use of unknown malware attachments. Luckily, we have technology that can analyze a file and determine if it is malicious or not, so we were able to block these as well. Trend Micro Cloud App Security detected and blocked 4,263,650 malware files in 2022, for a 29% increase from 2021’s numbers. The number of unknown malware files also surged to 3,757,812, for a 46% increase.
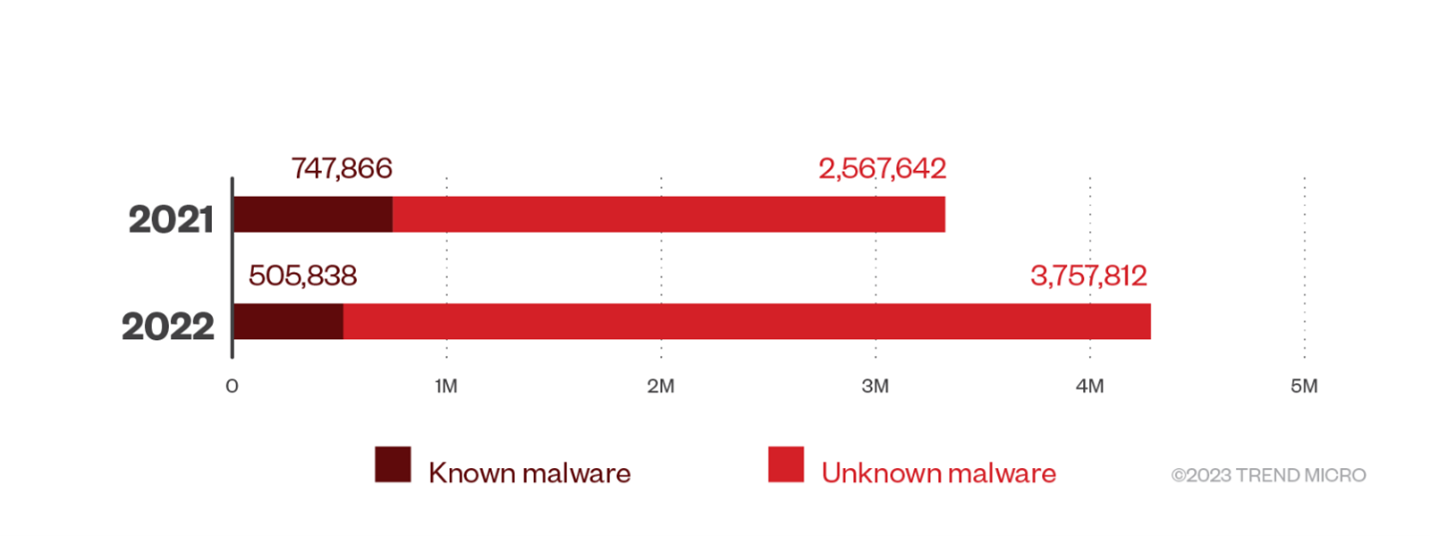
This is a trend we’re seeing in all attacks, where the malicious actors will customize their attack and develop brand-new components that have not been seen before. So, the first time you see the threat is the first time anyone has seen this threat, and likely it won’t be used again. The old security paradigm were using multiple vendor solutions to hedge that one may detect it is out the door now. You need a solution that can detect unknown threats or, at a minimum, quickly identify that something is wrong.
We also saw a marked decrease in ransomware attachments which makes sense as mostly now the ransomware component of an attack is the last stage due to it being so noisy. You know if you have a ransomware infection due to the pop-up ransom screen on affected computers. We saw a 42% decrease in these attachments in 2022 from 2021.
Business Email Compromise (BEC) is a threat that the U.S. FBI has considered more of a threat than ransomware. Losses in the billions from BEC far outweigh the losses from ransomware. In our data, we’re also seeing a BEC increase in use by malicious actors. We saw a 35% YoY increase in BEC emails targeting customers. What is unique about BEC emails is the fact that they do not contain any links or attachments to identify them easily. These are simply socially engineered messages that try to get an employee to conduct a wire or bank transfer, which these targeted employees typically do daily as part of their job function. As such, detecting a BEC email can be difficult, but it isn’t impossible, as seen in the chart below.
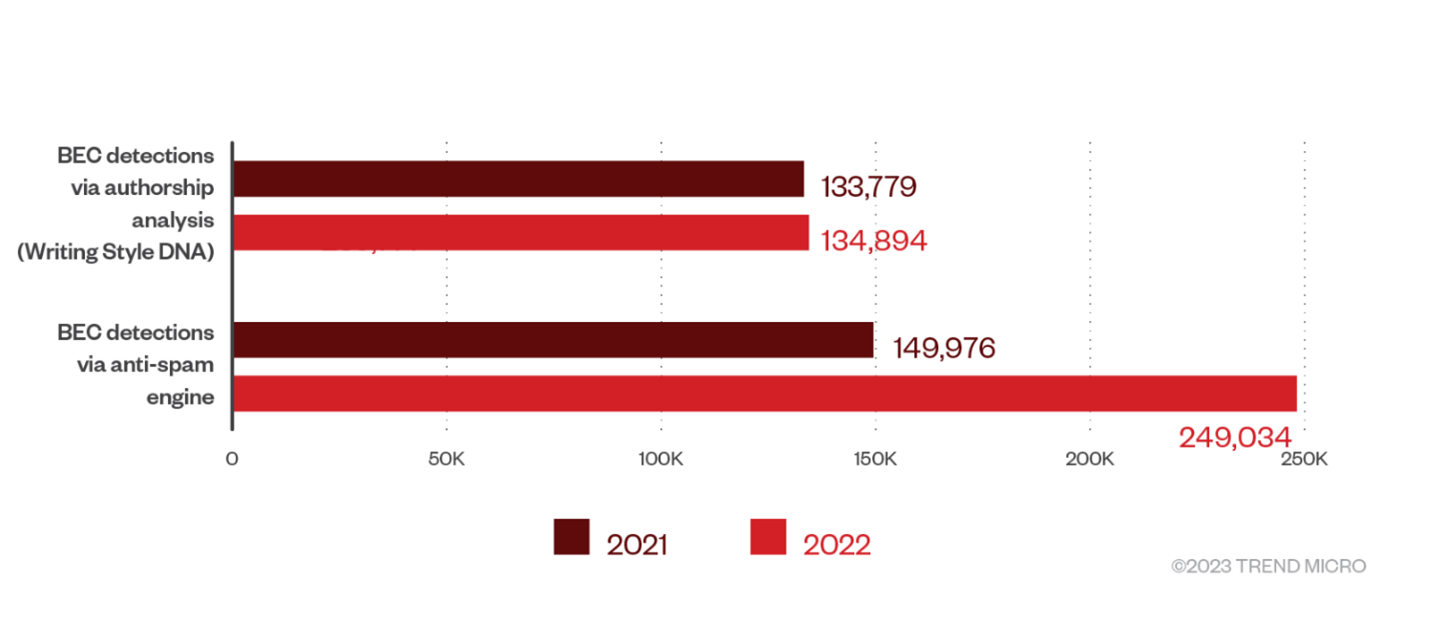
You’ll see above that Trend Micro developed a new AI-based technology called Writing Style DNA, which analyzes how employees write within their emails. After analyzing hundreds of their emails, we could identify if a malicious actor crafted a fraudulent BEC-type email, alert the sender and recipient of the suspicious email, and allow them to take action.
Another area we’re seeing a lot of unknown threats is credential phishing attacks. While we did not see a similar increase in unknown phishing, it still represents the majority of overall phishing attacks.
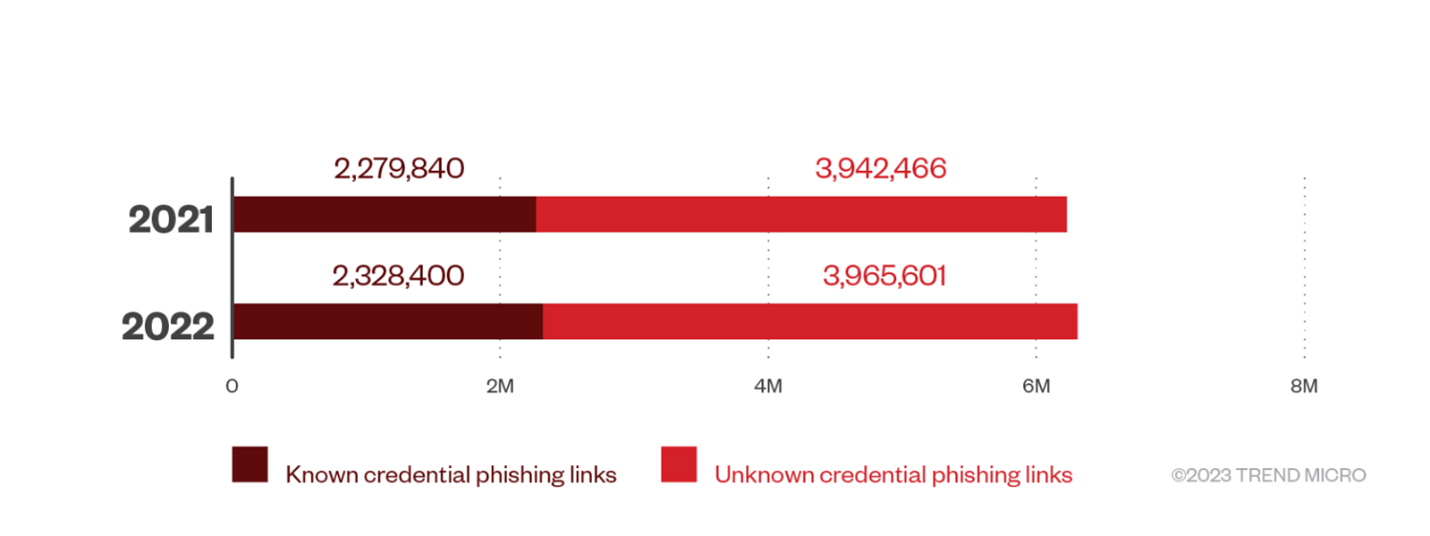
Credential theft is a tactic that malicious actors utilize more and more. BEC attacks today are coming more from stolen email accounts that are stolen by credential theft. We’re seeing this threat continue to be used by these actors in many of their attacks. These fake login requests continue to be used through malicious links within emails to try and obtain the Office 365 account credentials of the victim. Many of these victims today are targeted executives and financial and human resources employees.
The good news is that Trend Micro developed Computer Vision, a technology combining image analysis and machine learning (ML) to check branded elements, login forms, and other site content to detect credential phishing emails and URLs embedded within emails.
Standard phishing emails continue to be a popular attack vector targeting employees in order to gain access to their computers and the network in general. In 2022, we blocked over 22M phishing emails, representing a 29% increase from 2021.
A few other areas we saw were a decrease in the use of Covid-19 as a lure within emails as well as the use of email targeting cryptocurrency and NFTs.
I recommend you review your messaging security solutions and audit your vendor to ensure they fully protect your email. This includes emails from outside in, inside, and out, as well as internal to internal, since all of these are attack surfaces utilized by malicious actors. The use of advanced detection technologies like Writing Style DNA and Computer Vision should be part of your solution as well as multiple layered technologies that all come into play when analyzing messages.
To read Trend Micro Annual Cloud App Security Threat Report, please visit: https://www.trendmicro.com/vinfo/us/security/research-and-analysis/threat-reports/roundup/annual-trend-micro-cloud-app-security-threat-report
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



