Investigating identity threats in hybrid cloud environments
As the modern workplace transforms, the identity attack surface area is growing exponentially, across on-premises and cloud, spanning a multitude of endpoints and applications. Security Operations (SecOps) teams are challenged to monitor user activities, suspicious or otherwise, across all dimensions of the identity attack surface, using multiple security solutions that often are not connected. Because identity protection is paramount for the modern workplace, investigating identity threats requires a single experience to monitor all user activities and hunt for suspicious behaviors in order to triage users quickly.
Today, Microsoft is announcing the new identity threat investigation experience, which correlates identity alerts and activities from Azure Advanced Threat Protection (Azure ATP), Azure Active Directory (Azure AD) Identity Protection, and Microsoft Cloud App Security into a single investigation experience for security analysts and hunters alike.
Modern identity attacks leverage hybrid cloud environments as a single attack surface
The identity threat investigation experience combines user identity signals from your on-premises and cloud services to close the gap between disparate signals in your environment and leverages state-of-the-art User and Entity Behavior Analytics (UEBA) capabilities to provide a risk score and rich contextual information for each user. It empowers security analysts to prioritize their investigations and reduce investigation times, ending the need to toggle between identity security solutions. This gives your SecOps teams more time and the right information to make better decisions and actively remediate identity threats and risks.
Azure ATP provides on-premises detections and activities with abnormal behavior analytics to assist in investigating the most at-risk users. Microsoft Cloud App Security detects and alerts security analysts to the potential of sensitive data exfiltration for first- and third-party cloud apps. And Azure AD Identity Protection detects unusual sign-in information, implementing conditional access on the compromised user until the issue is resolved. Combined, these services analyze the activities and alerts, using UEBA, to determine risky behaviors and provide you with an investigation priority score to streamline incident response for compromised identities.
To further simplify your SecOps workflows, we embedded the new experience into the Cloud App Security portal, regardless of whether you’re using Microsoft Cloud App Security today. While it enriches each alert with additional information, it also allows you to easily pivot from the correlated alert timeline directly into a deeper dive investigation and hunting experience.
User investigation priority
We’re adding a new dimension to the current investigation model that is based on the number of total alerts with a new user investigation priority, which is determined by all user activities and alerts that could indicate an active advanced attack or insider threat.
To calculate the user investigation priority, each abnormal event is scored based on the user’s profile history, their peers, and the organization. Additionally, the potential business and asset impact of any given user is analyzed to determine the investigation priority score.
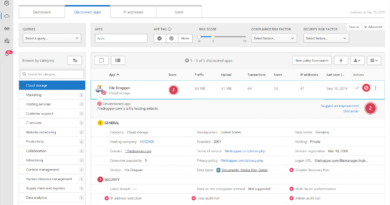
The new concept is included on the updated user page, which provides relevant information about who the user is, the investigation priority score, how it compares across all users within the organization, and abnormal alerts and activities of the user.
In the image below, the user’s investigation priority score of 155 puts them in the top percentile within the organization, making them a top user for a security analyst to investigate.
Identity threat investigation user page.
The score is surfaced on the main dashboard to help you get an immediate idea of which users currently represent the highest risk within your organization and should be prioritized for further investigation.
Top users by investigation priority on the main dashboard.
Improved investigation and hunting experience
Beyond signal correlation and a redesigned user page, the new identity threat investigation experience also adds new and advanced investigation capabilities specifically for Azure ATP customers, regardless of whether you choose to use Azure AD Identity Protection and or Microsoft Cloud App Security.
These capabilities include the:
- Ability for security analysts to perform threat hunting with greater context over both cloud and on-premises resources by leveraging advanced filtering capabilities and enriched alert information.
- Visibility and management of Azure AD user risk levels with the ability to confirm compromised user status, which changes the Azure AD user risk level to High.
- Creation of activity policies to determine governance actions and leverage built-in automation capabilities via the native integration with Microsoft Flow to more easily triage alerts.
New threat hunting experience to analyze alerts and activities.
Get started with the public preview today
If you’re one of the many enterprise customers already using Azure ATP, Microsoft Cloud App Security, and/or Azure AD Identity Protection and want to test the new identity threat investigation experience, get started by checking out our comprehensive technical documentation.
If you’re just starting your journey, begin a trial of Microsoft Threat Protection to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace.
We would love your feedback! Find us on the Azure ATP Tech Community and send us your questions or feedback on the new experience.
READ MORE HERE