It’s time you were T0RTT a lesson: Here’s how you could build a better Tor, say boffins
Academics in Germany say they’ve found a way to make Tor and similar onion networks more efficient and lower their latency.
The crew at Ruhr University Bochum, Universität Wuppertal, and Paderborn University described their technique in a paper [PDF] this week accepted into next year’s Proceedings on Privacy Enhancing Technologies Symposium: it describes an optimized and simplified approach to constructing circuits through which traffic is sent.
Anonymizing onion networks like Tor work by forming a circuit between a client and a destination via a number of relay nodes. The destination could be a so-called hidden service within the network, or an exit node that connects to a service on the public internet on behalf of the client. The connection between the client and destination is routed through these randomly picked nodes to obfuscate the public IP address of the client. The destination just sees the last hop in this chain, be it an exit or one of the relay nodes, and not the client.
The client wraps its traffic in nested layers of encryption, hence the name onion network, to protect it from eavesdropping and to ensure rogue nodes and snoops can’t walk through the circuit and unmask the client. This requires the client to perform secure Diffie-Hellman cryptographic key pair exchanges with relay nodes during the establishment of a circuit, carefully so to avoid unmasking the client, which takes time and bandwidth.
What the team suggests is a method they have dubbed T0RTT: Tor zero Round-Trip-Time key exchange. In this system, using a technique known as puncturable encryption, the number of steps to establish a circuit is drastically reduced. According to the paper, this will “allow a sender to transmit cryptographically protected data within the first message, without prior exchange of key establishment messages.”
This single-pass method also provides forward secrecy. If you want to know the mathematics behind it in detail, see the above links.
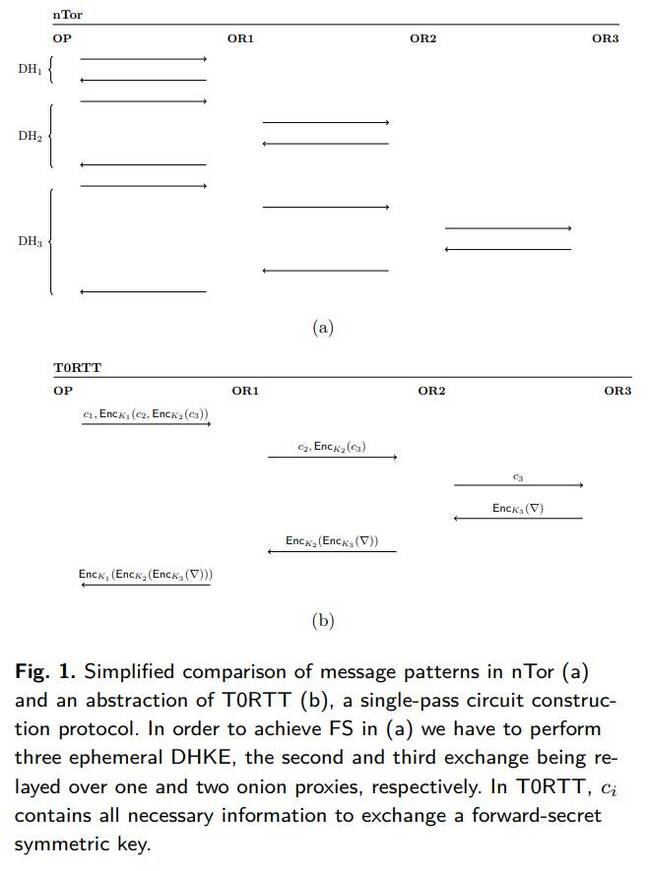
A diagram from the paper illustrating the differences between Tor’s current design and the proposed approach … Click to enlarge. Reproduced here with permission
Co-authors Sebastian Lauer and Kai Gellert told The Register on Wednesday this week that T0RTT would significantly decrease circuit establishment latency for netizens, as it would essentially halve the number of messages needed to set up a connection.
“This ensures that circuits are constructed faster and the number of messages in the network is reduced, which in turn reduces the load on the network infrastructure,” the boffins explained. “In Tor it is also recommended to change the circuit for each connection to prevent profiling attacks. A faster circuit construction thus increases not only efficiency but also security.”
Heads up, private penguins: Tails 4.0 is out. Security-conscious Linux gets updated apps, speed boost
They hope that, in the process, their approach would help ease one of the major complaints of Tor, the drag it adds to web browsing and internet access.
“In addition to usability, efficiency is usually more important to most users than privacy,” they said. “In our work, we would like to bring these two properties closer together and make the use of the Tor network more interesting.”
The technique is not without its faults, however. Because of the complexity of the data being transmitted to each node along the circuit, T0RTT would create a significant burden on RAM and CPUs that Tor nodes may struggle with. Before the protocol would be practical, this trade-off of latency for compute would need to be solved.
“The first solution would be to equip onion routers with better hardware. This would probably be the simplest solution and easy to realize with modern hardware,” said Lauer and Gellert. “The second and more interesting way would be to improve the construction of puncturable KEMs. Since this cryptographic primitive is still relatively young, we hope for further research results in this area in the next years.”
The paper, T0RTT: Non-Interactive Immediate Forward Secret Single-Pass Circuit Construction, was written by Sebastian Lauer (Ruhr University Bochum), Kai Gellert (Universität Wuppertal), Robert Merget (Ruhr University Bochum), Tobias Handirk (Paderborn University), and Jörg Schwenk (Ruhr University Bochum). It is due to be presented in July 2020 at the privacy symposium in Canada. ®
Sponsored: From CDO to CEO
READ MORE HERE
