Key Takeaways from the Linux Threat Report VP, Cloud Security

Cyber Threats
As the popularity of Linux continues to increase, so does its attack surface. This brings to light a pressing question for organizations: who is responsible for the security of all the Linux instances running your cloud environment?
The vast majority of the cloud environments are built using Linux as their foundation, and most of the major cloud providers founded their services on Linux. The public cloud is migrating to become an open-source operating environment, and Linux is proving to be the dominating force.
Linux’s strength originates in its open-source design and network of supporters. Linux is modular, scales, and therefore can support many use cases. The value of Linux is it’s the most available and reliable solution for critical workloads in data centers and cloud computing environments. Many variants of Linux exist, and according to our research, a single enterprise could have multiple instances of Linux (Ubuntu, Redhat, Amazon…). Its ubiquity in use is a natural consequence of its development process and the result was something stable and configurable enough for everyone.
All of this begs the question: who at your organization specializes in Linux? And who is responsible for the security of all the Linux instances running your cloud environment?
I took a look at job postings at the top 10 (publicly known) enterprise cloud adopters. Only a few of them had Linux admins listed on their job boards, so I used Discover.org to dig deeper (this is a third-party tool to find technologies used at companies). What I found was only 4 of the top 10 listed Linux as being in their environment or had job postings open (during a search in early August 2021). None of them were for cloud security of the Linux environment – all were on prem. Some of this could be bias in data, as well as job openings at the time of the search. So, I talked to a few of our customers and the trend was the same: the internal expertise does not exist or isn’t as strong as it needs to be.
The Linux threat landscape
Today, we released a research report on the state of the Linux threat landscape in H1’ 2021 highlighting the most critical security issues. Some of the key findings of the report include:
- Over 100,000 unique Linux hosts reported security events, showcasing a concerning amount of criminal activity targeting Linux hosts.
- In 2020 there were approximately 20k vulnerabilities reported, however only 200 (1%) have publicly known exploits. This gives a clear path forward for security teams of which vulnerabilities should be the patching priority.
- Detections were found from end-of-life versions of Linux. These unsupported systems are no longer receiving critical security patches leaving them significantly more vulnerable to future exploits and attacks.
- In July 2021 there were almost 14 million exposed Linux servers detected by Censys.io, and Shodan detected almost 19 million Linux servers with port 22 exposed, leaving plenty of openings for attackers to target. These misconfigurations are a prime example of why having strong internal expertise is important to ensure the proper security set-up is in place.
Over 13 million malware events were detected, with the following breakdown of malware type:
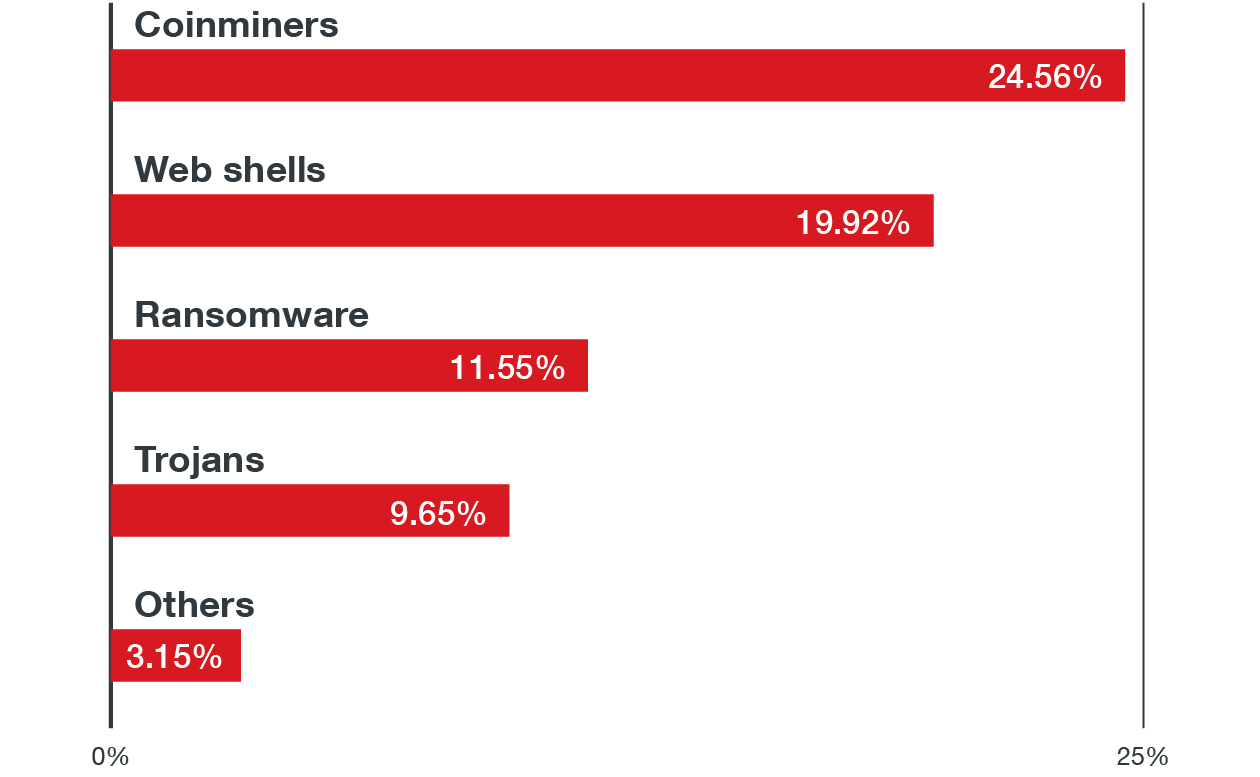
What does this mean?
In one way or another 62%+ of the malware families we found exist in and run on Linux. So, let’s add it up: Many enterprises run on Linux, as do their clouds. Few organizations have the expertise in house to understand, govern and have control over their cloud implementations. These are broad brush strokes, yes, but ask yourself as you’re reading this: do you know what your cloud security is related to Linux? Do you know how much is even in your cloud environment? When that time comes, will you and your company have meaningful knowledge of the cloud footprint at your organization?
If not, take time now to begin to implement the foundation. Work with your cloud providers, cloud architects, and technology partners to first gain understanding of your cloud environment, and then create a plan to assess and secure it. Some security best practices to follow are using the security by design approach, deploying multilayered virtual patching or vulnerability shielding, employing the principle of least privilege, and adhering to the shared responsibility model.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



