LockBit extorted billions of dollars from victims, fresh leaks suggest
Authorities digging into LockBit’s finances believe the group may have generated more than $1 billion in ransom fees over its four-year lifespan.
That’s according to the latest leak published today on LockBit’s blog, now under the control of Operation Cronos, who analyzed 30,000 cryptocurrency addresses obtained after accessing and shuttering the ransomware group’s systems this week.
The analysis showed addresses held around £100 million ($126.6 million), £90 million ($114 million) of which was unspent, comprised largely of the payments made to LockBit by affiliates who were paid by victims.
Although the cut taken by LockBit typically varies, around 20 percent of the total ransom fee is paid to the LockBit organization, while the affiliate who actually carried out the attack keeps the remainder.
It means the actual total sum of money extorted from victims stands to be considerably higher, deep into the hundreds of millions of dollars, according to the analysts at the South West Regional Organised Crime Unit and Chainalysis.
The data available to analysts was only taken from an 18-month period, July 2022 to February 2024. Considering LockBit was operating for around four and a half years before authorities shut it down this week, the likelihood that the sum extorted from victims over this time was in the real of multi-billions of dollars – a staggering feat of cybercrime.
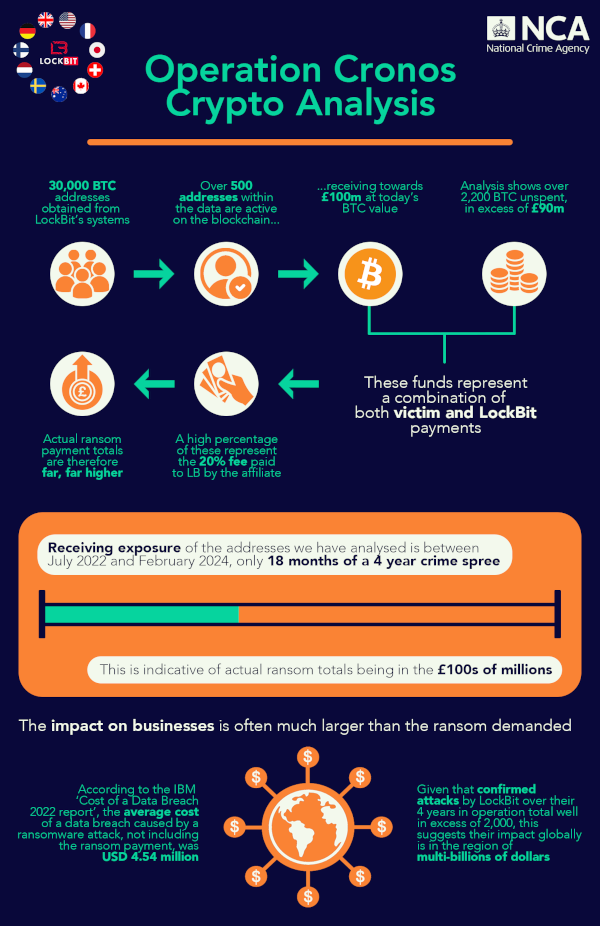
Infographic provided by the NCA illustrates LockBit’s finances over the most recent 18-month period – Click to enlarge
This idea is further supported by external data, such as the current estimated average ransom demand being set at around $1.5 million.
Taking this into account, along with the number of victims LockBit has claimed over its lifespan (in excess of 2,000), accounting for those that paid and those that didn’t, LockBit could indeed have extorted billions of dollars from victims.
It’s worth noting that the percentage of ransomware victims that actually pay their ransom demands is widely contested, with different reports suggesting wildly different figures.
Regardless, the findings blow the previous estimates of LockBit’s riches out of the water. As of June 2023, authorities told The Reg that US LockBit victims had paid “more than $90 million” in ransoms since the ransomware op started in 2020 – a figure we can now assume to be severely underestimated.
“LockBit have carried out thousands of confirmed attacks over their four-year lifespan, meaning their impact can be measured in the multi-billions of dollars globally,” reads LockBit’s website today, which is being controlled by the UK’s National Crime Agency (NCA).
“A key partner in the broader UK investigation, the South West Regional Organised Crime Unit, supported by Chainalysis, has led in the tracking and monitoring of thousands of cryptocurrency addresses linked to LockBit.
“LockBit exposed exchange accounts are also being targeted, with hundreds of thousands of USD worth of crypto assets across more than 85 accounts currently restricted by Binance. We continue to progress this work and more details will come to light as we progress the investigation.”
The exposure of LockBit’s finances comes on the final day of the week-long leaks scheduled by Operation Cronos, maximizing the publicity of its takedown of what is possibly the most prolific ransomware gang ever.
To the delight of the cybersecurity community on Tuesday, February 20, authorities took control of LockBit’s leak site, removing all mention of the victims it claimed over the years and transforming it into an exposé hub, revealing the once secretive operation’s inner workings.
It’s due to be shut down for good at midnight on Sunday, February 25.
The gang’s leader has previously offered a $1 million reward for anyone who could unearth their real identity, a reward the US recently upped to $15 million this week. ®
READ MORE HERE
