Mac Malware MacStealer Spreads as Fake P2E Apps


Conclusion
While not new, P2E games are enjoying a renewed interest and rise in popularity, and so will the efforts of threat actors aiming to take advantage of this growing trend. MacStealer malware is just one of many to take advantage of P2Es’ traction. P2E gamers, in particular, are lucrative targets because the economic model of these games requires them to adopt cryptocurrencies and wallets.
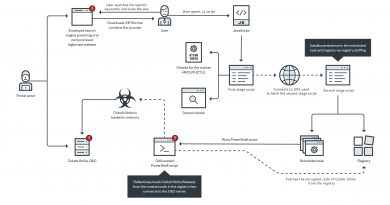
Security researchers can find investigating the delivery of the malware sample a challenge considering the threat actors used uncommon means to deliver their malware with the use of Discord and Telegram to directly communicate with their victims. Although this requires more effort, the victim’s profile (i.e., the user owns a crypto wallet) makes it worthwhile.
The malware doesn’t appear to be highly sophisticated, with a routine that requires a low skillset since the original code is a Python script. The main sample itself is not intricate, given the original code is a Python script compiled to a Mach-O binary using Nuitka, though it makes it difficult to decompile. This can be challenging for analysts to reverse engineer because, despite its simplicity, the compilation to a Mach-O binary using Nuitka shows how a well-placed attack on a good target could reap big rewards. In this case, they targeted P2E gamers who regularly use crypto wallets. Most of the profits collected by the cybercriminals are due to stolen cryptocurrencies siphoned off via social engineering techniques to deliver the malware to users’ devices (i.e., websites, Twitter accounts, and other related channels).
Discord enables channels for various purposes, among them P2E games and users. As a platform that evolved to become a gamer’s haven to exchange information, downloading a link in Discord for access to a game — either as a user or tester — might not have immediately raised red flags among the victims. This also increases the likelihood of why the cybercriminals chose the platform to spread the malware. One victim noted, however, that there was a significant lack of interactions in the cybercriminals’ channel and flagged those details as a warning to others. Other users warned that as soon as they requested for screenshots or posted cautionary tweets, they were immediately banned from the channels.
Moreover, due to the recent disruptions in the Twitter’s ownership and changes in policies for account verification, it appears the cybercriminals abused it to easily get a verified account. This provides an illusion of legitimacy to improve fake apps’ and accounts’ social engineering capabilities. Using this technique can also easily be advertised using other platforms such as TikTok, YouTube, and Facebook. We may expect more of these trends in code/script compiling and malware delivery in the future.
To avoid and defend against threats like MacStealer, we strongly advise being wary of installing apps from unofficial sources and app platforms. Enabling the latest security solutions for devices can also help detect, block, and mitigate the risks of these kinds of threats.
Indicators of Compromise (IOCs)
You can download the full list of IOCs here.
MITRE TTPs
Read More HERE