Microservice Security: How to Proactively Protect Apps
Serverless Security
Microservices are growing in popularity—how can development teams embed seamless security into the entire pipeline? Fernando Cardoso, solutions architect at Trend Micro, breaks it down for you.
Microservices Overview
As many organizations moved to serverless functions to maximize agility and performance in the cloud, microservices became the new go-to design architecture for modern web applications. According to IBM, 88% of microservices users and 77% of non-users agree that microservices benefit development teams.
This cloud-native architectural approach allows developers to use their preferred stacks and programming languages for different components, increasing build and deployment time. Code can also be updated more easily—no need to restructure the entire application to add a new feature.
Security for Microservices
Since microservices mean more services built by more teams deployed in more places, management can be quite complex. This can lead to several security challenges for serverless microservice apps, including:
- Data injection
- Insufficient monitoring and logging capabilities
- Overly permissive permissions applied to cloud services running the application
- Cloud services misconfigurations
- Lack of input sanitization
- Unsecure code from third-party packages
App security is crucial—Tech Republic reported that 70% of web apps are vulnerable to data breaches and 60% of developers are focused on building web apps. To get the most out of microservices and severless functions, let’s look at how to embed seamless security.
Embedding Microservices Security Overview
Below is a high-level example of how to incorporate security into your app. By deploying a security tool at the start of your build process, you can automate open source code and library scanning as well as dependency tracking in your Git repository. This allows developers to validate and sanitize their open source code before committing it to your CI/CD pipeline, allowing you to put your most secure foot (code) forward.
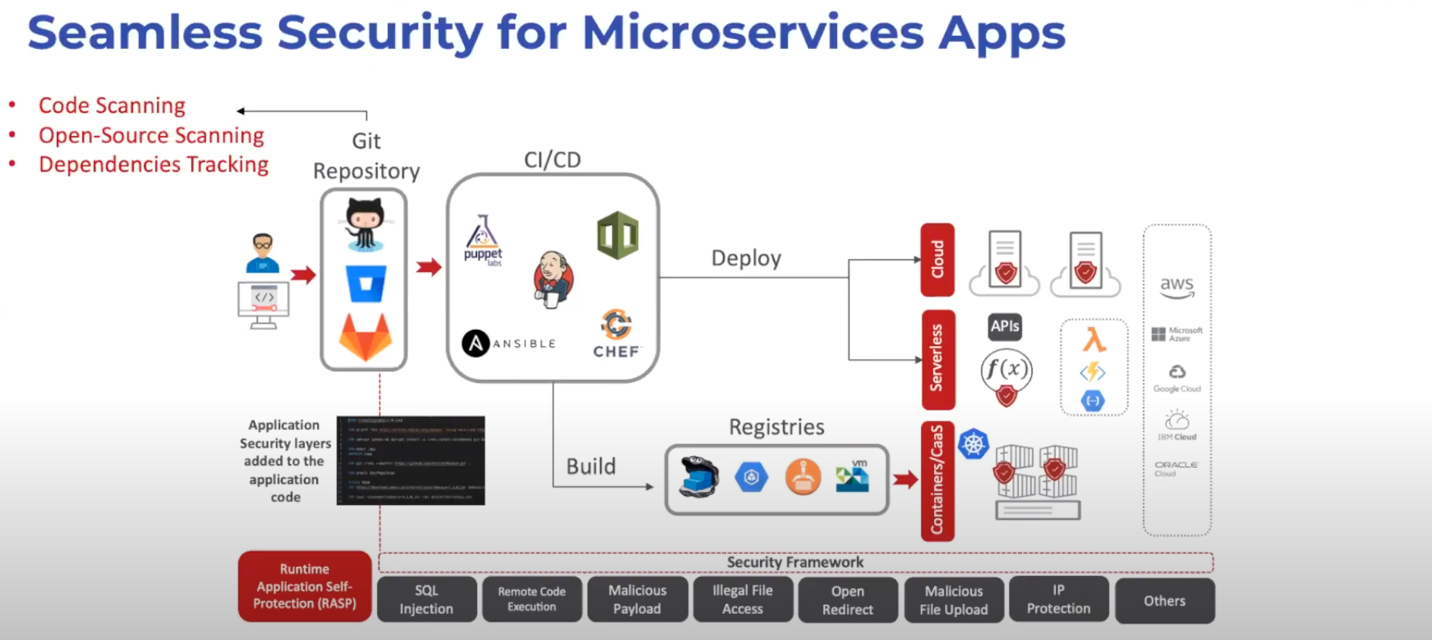
As you can see above, we’ve deployed Trend Micro Cloud One™ – Application Security within your application code for runtime application security to protect against common attacks like SQL injection and remote code execution.
Application Security is one of 7 services that make up Trend Micro Cloud One™, our cloud-native platform. By leveraging Trend Micro Cloud One™ – Conformity and Application Security (all within the same dashboard), you can run 24/7 configuration checks, which is critical considering how diversified teams can create other services and change configurations whenever, wherever. All configuration checks are validated against the AWS/Azure Well-Architected Frameworks, PCI DSS, and many more. Bonus: you can customize your checks according to your specific use cases.
By enabling monitoring and logging capabilities, Application Security provides enhanced visibility into suspicious behaviours, even at “report” mode. You can see the number of requests sent, time of process, source IP trust level, and more.
Those security issues we mentioned earlier? Taken care of. You may be thinking: ok, great, now how can I do it? Let’s get into it.
DEMO: Microservices Security
Here is the architecture we will be using to demonstrate how to protect AWS Lambda functions:
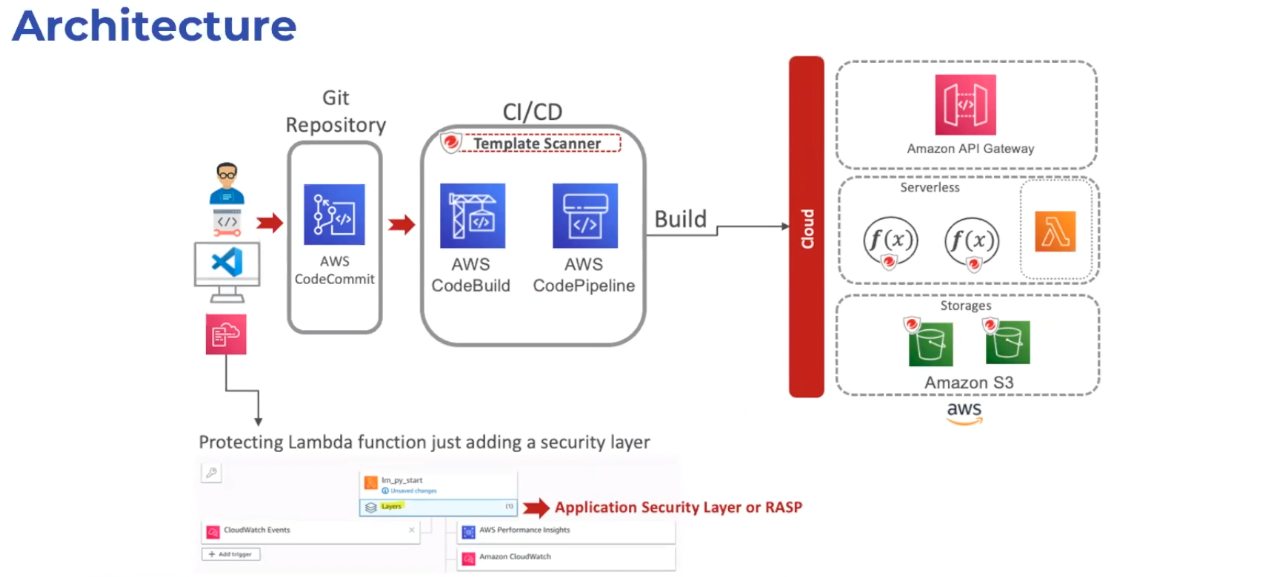
Start by defining the APIs you need and the regions activating the security library.
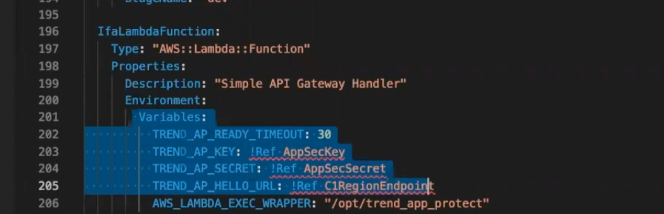
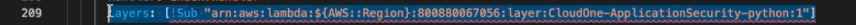
Next, embed the security layer to protect the Lambda functions (Amazon API Gateway, Amazon S3, etc.) that you will be deploying through your pipeline. Now, whenever a change is made in your environment, it will automatically enable RASP.
At the same time RASP is enabled, Conformity will validate the template with the CloudFormation template scanner.
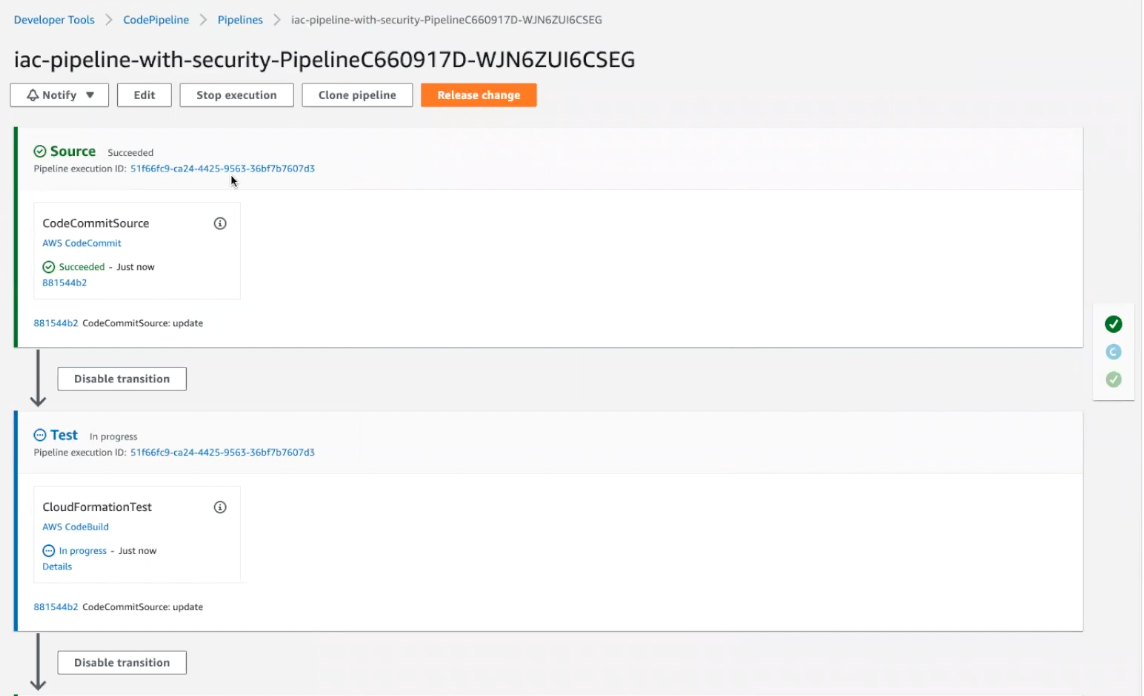
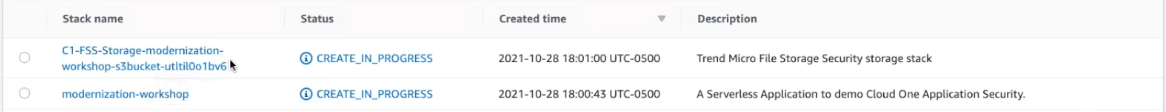
In our AWS CloudFormation stack, you can see the demo stacks, modernization-workshop and C1-FSS-Storage-modernization-workshop-s3bucket-utltil0o1bv6, will be running in tandem to provide, you guessed it, runtime app security.
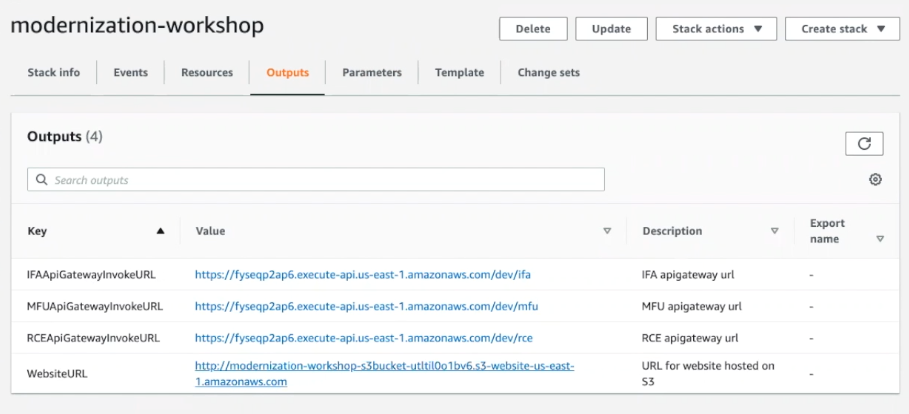
Now, let’s test it out. Click on Outputs for the modernization-workshop stack. Copy and paste the WebsiteURL into your browser.
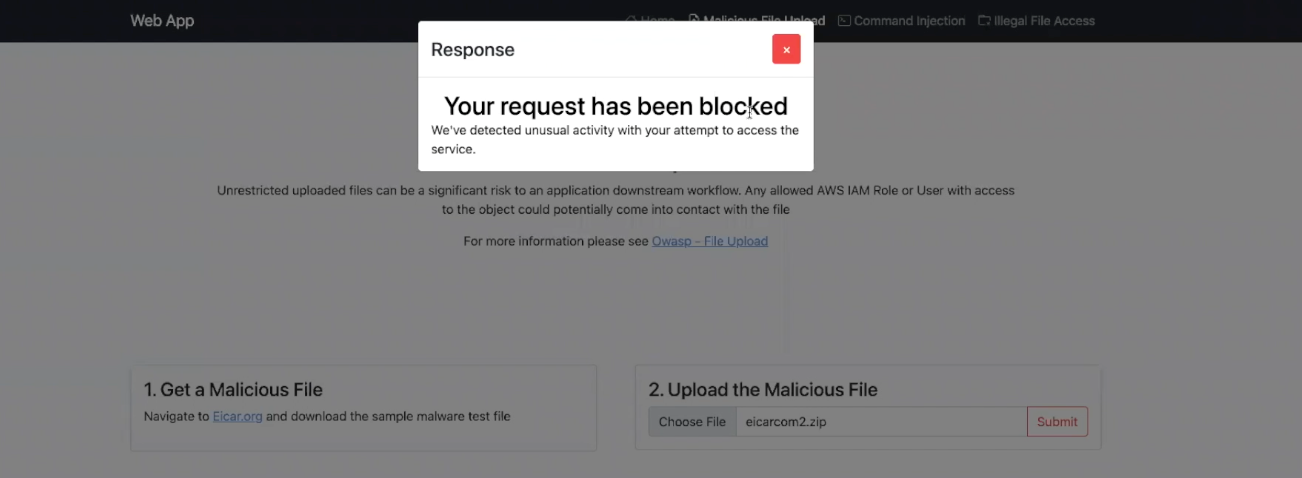
You should see our demo web app where you can attempt a malicious file upload, command injection, or illegal file access. Click on Malicious File Upload. Next download and upload the provided Eicar.org file. Click submit. Immediately, you should be notified your request is blocked. Awesome! (By the way, Application Security allows you to customize your response messages)
Navigate back to the Application Security console and select Microservices Web App event to view more. Here you can see a malicious file upload was blocked.
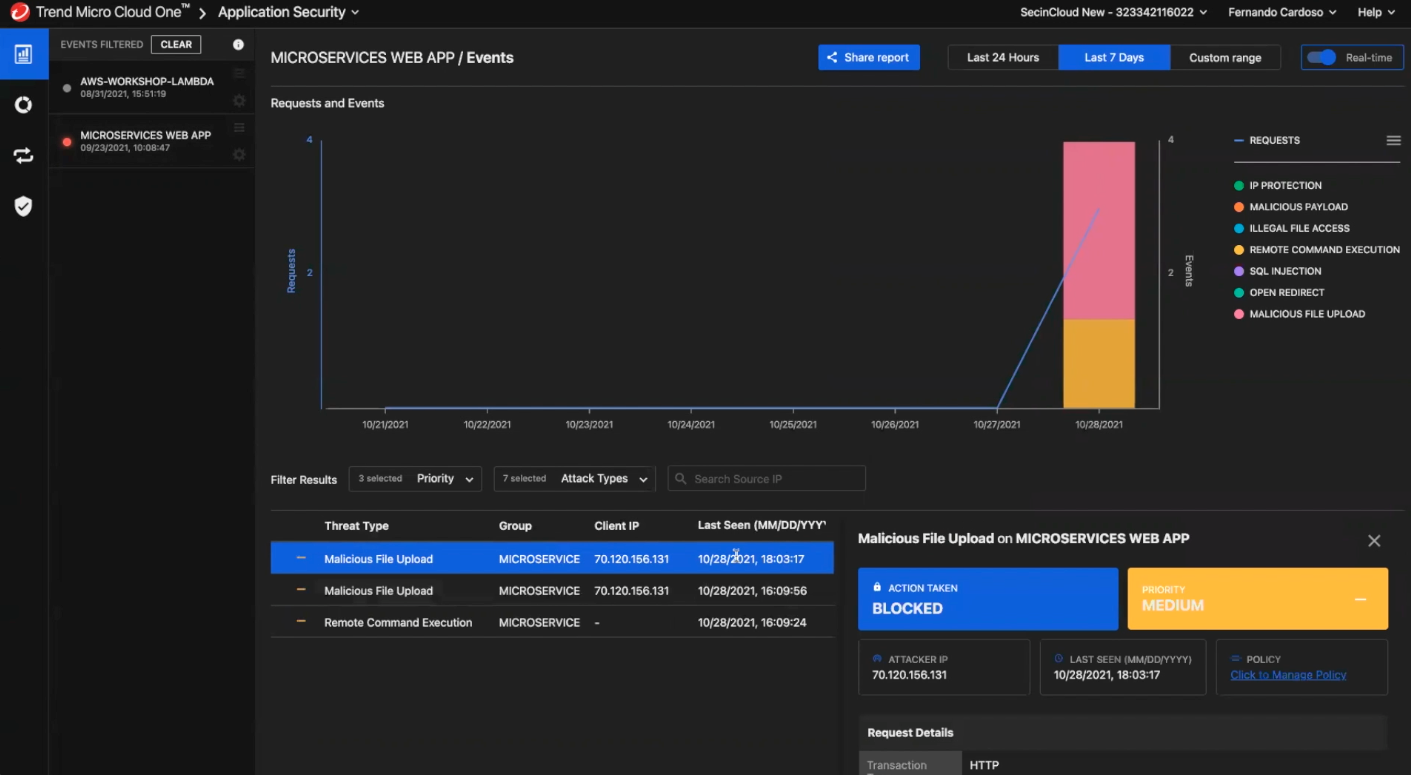
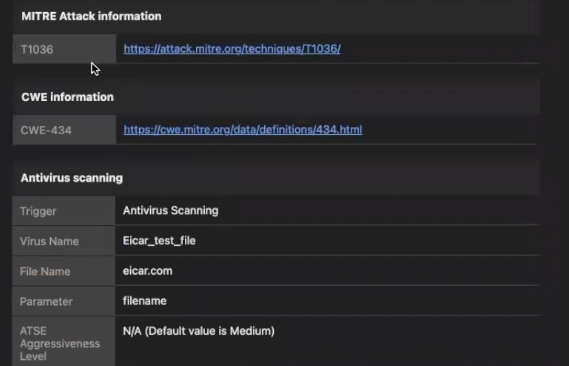
On your right-hand side, scroll down to see all the Request Details. This section provides pertinent information for development and security teams alike, such as the deployment attacked, source IP, type of malware detected, etc. Notably, security teams can map the attack with the MITRE ATT&CK framework for further investigation and analysis.
Ok, back on our web app, try to execute a command injection attack by copying and pasting the commands. Click Submit and a pop-up saying your request has been blocked will appear. Back in the Application Security console, you can see that a RCE was blocked and view additional threat information as you did with the malicious file attack. Et voila, the simplicity and magic of Application Security!
Next steps
Using the right security tools can allow you to embed seamless security into your microservices architecture, freeing you from building web apps the slower, more tedious “old way” (aka monolith). Application Security installs in two minutes and doesn’t require any source code or changes to your development code. It simply bootstraps to your application at runtime. To explore other Application Security capabilities, check out our comprehensive documentation. Or try the self-guided workshop built for customers to understand how Application Security works and can be deployed on AWS Fargate and AWS Lambda functions.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE