Microsoft Looks to Enable Practical Zero-Trust Security With Windows 11
Organizations aiming to boost their security with zero-trust initiatives got some help from Microsoft this week, when the computing giant announced that a slew of zero-trust features are now available in its Windows 11 operating system.
The zero-trust approach to security aims to secure workers’ access to sensitive systems, network, and data by using additional context, analysis, and security controls. The goal is to give “the right people the right access at the right time,” Microsoft stated in the Windows 11 Security Book, a 74-page report on Windows 11’s security architecture.
The model checks a user’s identity and location, as well as their device’s security status, and only allows access to the appropriate resources, according to the Windows 11 Security Book. In addition, zero-trust capabilities include continuous visibility and analysis to catch threats and improve defenses.
The latest version of the operating system and software platform adds a variety of features, from support for the Pluton security processor and trusted platform modules (TPMs) to comprehensive features around Trusted Boot, cryptography, and code-signing certificates, says David Weston, vice president of enterprise and OS security at Microsoft.
“Organizations worldwide are adopting a zero-trust security model based on the premise that no person or device anywhere can have access until safety and integrity is proven,” he says. “We know that our customers need modern security solutions with tightly integrated hardware and software that protects from entire classes of attack.”
The Zero-Trust Buzz Gets a Boost
The zero-trust concept has been knocking around for years, with technologists and government agencies first discussing it for security with the dawning realization that network perimeters were rapidly disappearing. Then, the work-from-home surge caused by the coronavirus pandemic injected more urgency into the movement. Now, three-quarters of security decision-makers (75%) believe that the increase in hybrid work creates vulnerabilities at their organization, leaving them more open to attacks.
“When employees are given the freedom to choose their work location, device, tools, and/or software, it becomes a challenge to establish trust based on static attributes,” says Ben Herzberg, chief scientist at Satori. “As the competitive pressure pushes companies to democratize data and release new customer value faster, employees will be provided more flexibility, and zero trust will be the go-to approach for enabling that flexibility while ensuring security.”
That said, implementing zero trust is a complex endeavor, as evidenced by the list of aspects that Microsoft has now built in:
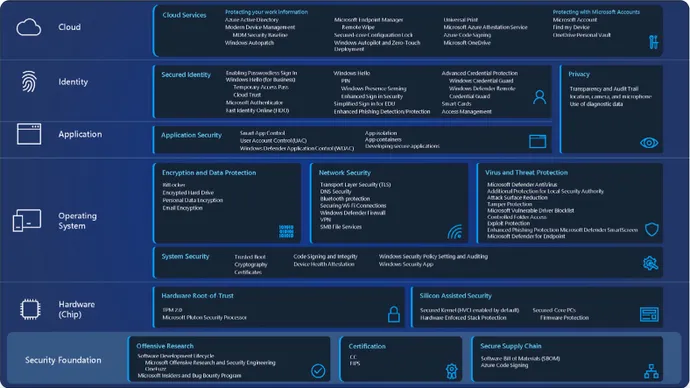
The new Windows 11 features include Smart App Control, which uses machine learning, AI modeling, and Microsoft’s vast telemetry network of 43 trillion daily signals to determine if an application is safe. Other features also determine whether driver code and virtual-machine code have signs of maliciousness. Additional improvements include credential checks in Windows Defender, password-less support with Windows Hello for Business, and protection against credential-harvesting websites, the company stated.
Complexity has hampered zero-trust rollouts, but adding these feature directly into Windows 11 makes it more likely that companies can easily deploy zero-trust capabilities, says Microsoft’s Weston.
“Building in instead of bolting on makes deployment and management of zero-trust capabilities much simpler and efficient,” he says. “In addition, having these [features] directly integrated in the OS enables Windows to provide key measurements in hardware increasing the trust and validity of measurements.”
He adds, “The minute zero-trust capabilities are embedded into enterprise infrastructure, it becomes accessible for many companies that would otherwise have a hard time getting access to this technology. … An integrated client environment for zero trust will make the transition for employees much smoother and internal change management simpler.”
Microsoft throwing its considerable weight behind zero trust should indeed move the needle on adoption and overall security: Microsoft sees 2.5 billion endpoint queries and 80 million password attacks on a daily basis, the firm stated in a blog post published this week.
Zero Trust Is Still Hard
Even with the Windows 11 updates, companies should expect implementing zero trust to be a process. Building a zero-trust framework requires deep technical integrations, and the organizations that do that best are the ones most likely to be successful in their implementation, says Satori’s Herzberg.
To start off, companies should identify a group of users, devices, applications, and workflows that could benefit from zero trust; create a zero-trust architecture to protect those components; and then choose and implement the proper technologies, he says.
An incremental rollout works, given that zero trust is more of a journey than a destination, says Jason Floyd, chief technology officer at Ascent Solutions.
“Zero trust was never about solving a technology problem — it’s a strategic tool directing how to use the technology already in place,” he says. “Building additional zero-trust features into Windows does encourage enterprises to adopt a healthy security mindset, but not for the one-size-fits all solution some executives might be expecting.”
Overall, Windows 11 adds “chip-to-cloud security,” establishing trusted processes starting with firmware and reaching out to workloads running in the cloud, Microsoft’s publication stated. This support aids zero-trust architectures by minimizing the work required to prove a user’s identity and check system health, says Microsoft’s Weston.
“This inverts the previous paradigm of systems security where a user or device was assumed healthy until proven guilty,” he says. “Microsoft’s view is that the zero-trust philosophy and architecture addresses many of the current and future security challenges for customers and thus Microsoft and most of our customers believe this will be the dominant approach to security.”
Read More HERE
