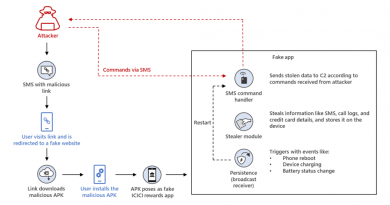
Microsoft Threat Protection stops attack sprawl and auto-heals enterprise assets with built-in intelligence and automation
Attackers will cross multiple domains like email, identity, endpoints, and applications to find the point of least resistance. Today’s defense solutions have been designed to protect, detect, and block threats for each domain separately, allowing attackers to exploit the seams and threshold differences between solutions—leaving the business vulnerable to attack. While one facet of an attack may be caught and blocked in email, the same threat actor may have also compromised identities by exploiting weak passwords or leaked credentials, or by fooling people into providing their passwords or authorization tokens. It’s also possible for point solutions to overlook critical signals entirely because, in isolation, they failed to register as significant.
The industry as a whole has struggled to win this battle, but we can turn the tide. The current class of security solutions can do a better job of stopping or even preventing the spread of attacks by looking at the entire security stack as a living organism. We have to force a shift in the protection paradigm by moving from a model of reactive detection and response based on siloed security solutions to proactive protection. We cannot leave security teams to manually coordinate signals across domains to fully understand the breadth of the attack and how to stop it. Threat protection that changes our approach to attacks requires built-in intelligence that can understand how an attack got in, prevent its spread across domains, and automatically heal compromised assets.
Microsoft Threat Protection coordinates defenses to stop attacks from spreading and auto-heal impacted assets
Generally available Microsoft Threat Protection (MTP) provides the built-in intelligence, automation, and integration to coordinate protection, detection, response, and prevention by combining and orchestrating into a single solution the capabilities of Microsoft Defender Advanced Threat Protection (ATP) (endpoints), Office 365 ATP (email), Azure ATP (identity), and Microsoft Cloud App Security (apps).
With MTP, security teams can:
- Automatically block attacks and eliminate their persistence to keep them from starting again. MTP looks across domains to understand the entire chain of events, identify affected assets, and protect your most sensitive resources. When, for example, a compromised user or an at-risk device tries to access confidential information, MTP applies conditional access and blocks the attack, delivering on the Zero Trust model.
- Prioritize incidents for investigation and response. MTP lets you focus on what matters the most by correlating alerts and low-level signals into incidents to determine the full scope of the threat across Microsoft 365 services. Incidents provide a complete picture of the threat in real time and in a single, cohesive console.
- Auto-heal assets. MTP identifies affected assets like users, endpoints, mailboxes, and applications, and returns them to a safe state. Automated healing includes actions like identifying and terminating malicious processes on endpoints and removing mail forwarding rules attackers put in place and marking users as compromised in the directory.
- Focus unique expertise on cross-domain hunting. MTP empowers the security team to be proactive, giving them back the time they need to learn from our insights, harden defenses, and keep out more threats. It also lets them use their unique organizational knowledge like proprietary indicators of compromise, org-specific behavioral patterns, and free-form research to actively hunt for threats across domains with custom queries over raw data.
Microsoft’s protection, detection, and response solutions have consistently achieved leadership placement, including in Gartner’s Endpoint Protection Platform Magic Quadrant, Gartner’s Cloud Access Security Broker (CASB) Magic Quadrant and Forrester’s Endpoint Security Suites Wave. Our world-class security research teams study attacker behaviors within each of these solution domains and, more importantly, how attackers traverse these domains in pursuit of their ultimate objective.
Not only have we embraced the MITRE ATT&CK framework for endpoints, we joined the MITRE Center for Threat Informed Defense as a Founding Research Sponsor to share and grow our understanding of the full scope of cross-domain attacker behaviors. The deep knowledge we have about each of these pillars of protection, combined with the more than 100 members in the Microsoft Intelligent Security Association (MISA), provides our customers with the holistic protection prevention they need to finally get ahead of attacks.
Coordinated defenses to uncover the full attack kill chain can help block nation-state level attacks
Cloud services significantly expand the traditional perimeter that defenders have to monitor and protect, introducing novel attack scenarios. HOLMIUM, a well-known adversary focused on victims mostly in the energy and aerospace sectors where the payouts are massive, has been one of the first to use cloud attack vectors.
In 2019, the Microsoft Threat Intelligence Center notified nearly 10,000 customers targeted by a few nation-state actors, citing HOLMIUM as one of the most active. Sophisticated attacks like this are why MTP was created. A recent HOLMIUM attack pattern demonstrates this: HOLMIUM targets identities in the cloud as a first step. After compromising an identity, the adversary leverages cloud APIs to persist, using a cloud email configuration to run malicious PowerShell on the endpoint every time Outlook is opened by the user. A conventional approach to containing this threat may start with the endpoint; when the PowerShell activity is detected, the SOC remediates the endpoint. However, in this case the attacker is persistent in the cloud and so the endpoint could be immediately compromised again.
MTP looks at the bigger picture and goes beyond simple blocking on the endpoint, putting a compromised organization in a better position to fight the threat. Signs of the attack are detected across the affected domains, including password spraying activity against Azure Active Directory (AD), sign-ins to Office 365 with potentially compromised credentials, and malicious PowerShell executions on endpoints. These detections are correlated into a coherent incident that catalogs the end-to-end attack and all affected assets. MTP intervenes to block the attack, not only stopping the PowerShell activity on the endpoints but also containing the impacted user accounts by marking them as compromised in Azure AD. The Threat Analytics report in MTP provides an exposure view and recommends the customer apply the appropriate Outlook security patch that will prevent this attack from recurring.
MTP extends coordinated protection across platforms with Microsoft Defender ATP for Linux and across domains with Azure Sentinel
Today, we’re announcing another step in our journey to offer security from Microsoft with the public preview of Microsoft Defender ATP for Linux. Extending endpoint threat protection to Linux has been a long-time ask from our customers and we’re excited to be able to deliver on that. We know our customers’ environments are complex and heterogenous. Providing comprehensive protection across multiple platforms through a single solution and streamlined view is more important than ever. Next week at the RSA Conference, we’ll provide a preview of our investments in mobile threat defense with the work we’re doing to bring our solutions to Android and iOS.
Azure Sentinel, Microsoft’s cloud-native security information and event manager (SIEM), further extends the capabilities of MTP by incorporating alerts, threat intelligence, and signals from third-party solutions. MTP shares alerts and threat intelligence with Azure Sentinel so security teams can view and manage threats across Microsoft and third-party security solutions in a single SIEM console.

To learn more about how Microsoft Threat Protection can help you deliver proactive protection and prevention against the spread of attacks, see Microsoft Threat Protection and stop by our booth at the RSA Conference!
Stay tuned for more information on our cross-platform journey from our Tech Community blogs next week!
READ MORE HERE