Microsoft warns of widespread open redirection phishing attack – which Defender can block, coincidentally
Microsoft has warned that it has been tracking a widespread credential-phishing campaign that relies on open redirector links, while simultaneously suggesting it can defend against such schemes.
“Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking,” the company’s Microsoft 365 Defender Threat Intelligence Team said in a blog post on Thursday.
“Doing so leads to a series of redirections – including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems – before taking the user to a fake sign-in page.”
An open redirect is when a web application allows an HTTP parameter to contain a user-supplied URL that causes the HTTP request to be redirected to the referenced resource.
Microsoft says that open redirects have legitimate uses, pointing to the way sales and marketing campaigns rely on them to lead customers to specific landing pages and to gather web metrics. But open redirects are also commonly abused.
The messages in this particular campaign, according to the company, tend to follow a common pattern. They use a few generic subject lines formatted thus:
- [Recipient username] 1 New Notification
- Report Status for [Recipient Domain Name] at [Date and Time]
- Zoom Meeting for [Recipient Domain Name] at [Date and Time]
- Status for [Recipient Domain Name] at [Date and Time]
- Password Notification for [Recipient Domain Name] at [Date and Time]
- [Recipient username] eNotification
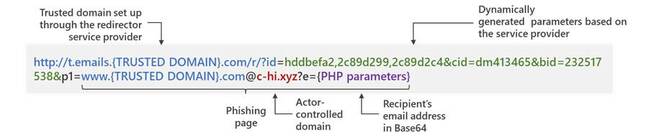
Once opened, the messages present a button to show the purported notification message. The button is linked to a trusted domain appended with redirection parameters in a way that’s intended to look convincing to a casual level of scrutiny, such as a brief glimpse of the full URL when a mouse pointer is hovering over the button.
Anyone who understands how URLs and appended parameters work probably wouldn’t be duped, but less savvy users might well see the initial trusted URL and assume all’s well, unconcerned about all the parameter data added to the request.
To further convey the illusion of safety and legitimacy, the redirection takes the victim to a Google reCAPTCHA page, which Microsoft theorizes also serves to frustrate dynamic scanning and content checking of the phishing page at the end of the redirection.
Those who successfully complete the CAPTCHA puzzle and demonstrate to the phishers that they’re legitimate marks get shown a website that pretends to be a known, legitimate service, like Microsoft Office 365. And the scam site loads with the target’s email address – passed to the phishing page as a parameter in the phishing URL – and often with corporate logos or other branding to make the login page look more like it’s implementing common single sign-on behavior.
If the victim enters a password, that’s not the end of it. The page then refreshes with an error message declaring that the session timed out and directing the visitor to enter the password again, a data validation practice not unlike the double opt-in ritual used by email marketing list services to ensure compliance with spam laws.
For being so kind as to confirm their passwords, phishing victims get redirected to a legitimate Sophos security website indicating, falsely, that the email message that they were notified to retrieve has been released.
Microsoft says it has detected at least 350 unique phishing domains involved in this campaign. The scheme appears to have the potential to go far beyond that – the redirection URLs come from a domain-generation algorithm that creates phishing domains on the fly, as needed.
Sophisticated as this scheme may sound, Microsoft insists its Defender for Office 365 software offers adequate protection because it includes a built-in sandbox that examines all redirection links. Defender allegedly does so “even in cases where the landing page requires CAPTCHA verification,” which doesn’t exactly inspire a lot of confidence in CAPTCHAs as a means for distinguishing between human and automated interaction.
That being the case, why is Microsoft bothering to sound the alarm? Well, 91 per cent of all cyberattacks originate with email, according to Redmond. Clearly, phishing still works, as does selling security by pointing that out. ®
READ MORE HERE