Millions Of IPs Remain Infected By USB Worm Years After Its Creators Left It For Dead

A now-abandoned USB worm that backdoors connected devices has continued to self-replicate for years since its creators lost control of it and remains active on thousands, possibly millions, of machines, researchers said Thursday.
The worm—which first came to light in a 2023 post published by security firm Sophos—became active in 2019 when a variant of malware known as PlugX added functionality that allowed it to infect USB drives automatically. In turn, those drives would infect any new machine they connected to, a capability that allowed the malware to spread without requiring any end-user interaction. Researchers who have tracked PlugX since at least 2008 have said that the malware has origins in China and has been used by various groups tied to the country’s Ministry of State Security.
Still active after all these years
For reasons that aren’t clear, the worm creator abandoned the one and only IP address that was designated as its command-and-control channel. With no one controlling the infected machines anymore, the PlugX worm was effectively dead, or at least one might have presumed so. The worm, it turns out, has continued to live on in an undetermined number of machines that possibly reaches into the millions, researchers from security firm Sekoia reported.
The researchers purchased the IP address and connected their own server infrastructure to “sinkhole” traffic connecting to it, meaning intercepting the traffic to prevent it from being used maliciously. Since then, their server continues to receive PlugX traffic from 90,000 to 100,000 unique IP addresses every day. Over the span of six months, the researchers counted requests from nearly 2.5 million unique IPs. These sorts of requests are standard for virtually all forms of malware and typically happen at regular intervals that span from minutes to days. While the number of affected IPs doesn’t directly indicate the number of infected machines, the volume nonetheless suggests the worm remains active on thousands, possibly millions, of devices.
“We initially thought that we will have a few thousand victims connected to it, as what we can have on our regular sinkholes,” Sekoia researchers Felix Aimé and Charles M wrote. “However, by setting up a simple web server we saw a continuous flow of HTTP requests varying through the time of the day.”
They went on to say that other variants of the worm remain active through at least three other command-and-control channels known in security circles. There are indications that one of them may also have been sinkholed, however.
As the image below shows, the machines reporting to the sinkhole have broad geographic disbursement:
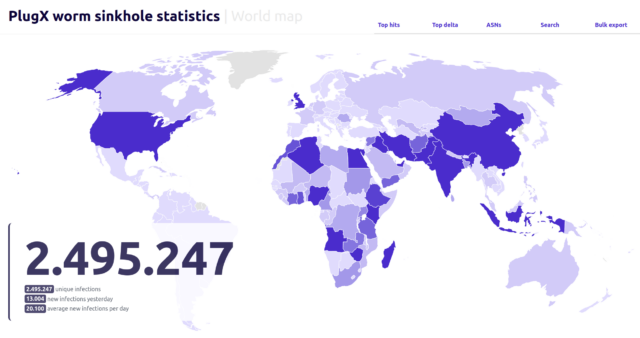
A sample of incoming traffic over a single day appeared to show that Nigeria hosted the largest concentration of infected machines, followed by India, Indonesia, and the UK.
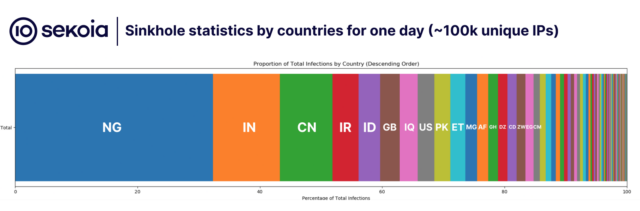
The researchers wrote:
Based on that data, it’s notable that around 15 countries account for over 80% of the total infections. It’s also intriguing to note that the leading infected countries don’t share many similarities, a pattern observed with previous USB worms such as RETADUP which has the highest infection rates in Spanish spelling countries. This suggests the possibility that this worm might have originated from multiple patient zeros in different countries.
One explanation is that most of the biggest concentrations are in countries that have coastlines where China’s government has significant investments in infrastructure. Additionally many of the most affected countries have strategic importance to Chinese military objectives. The researchers speculated that the purpose of the campaign was to collect intelligence the Chinese government could use to achieve those objectives.
The researchers noted that the zombie worm has remained susceptible to takeover by any threat actor who gains control of the IP address or manages to insert itself into the pathway between the server at that address and an infected device. That threat poses interesting dilemmas for the governments of affected countries. They could choose to preserve the status quo by taking no action, or they could activate a self-delete command built into the worm that would disinfect infected machines. Additionally, if they choose the latter option, they could elect to disinfect only the infected machine or add new functionality to disinfect any infected USB drives that happen to be connected.
Because of how the worm infects drives, disinfecting them risks deleting the legitimate data stored on them. On the other hand, allowing drives to remain infected makes it possible for the worm to start its proliferation all over again. Further complicating the decision-making process, the researchers noted that even if someone issues commands that disinfect any infected drives that happen to be plugged in, it’s inevitable that the worm will live on in drives that aren’t connected when a remote disinfect command is issued.
“Given the potential legal challenges that could arise from conducting a widespread disinfection campaign, which involves sending an arbitrary command to workstations we do not own, we have resolved to defer the decision on whether to disinfect workstations in their respective countries to the discretion of national Computer Emergency Response Teams (CERTs), Law Enforcement Agencies (LEAs), and cybersecurity authorities,” the researchers wrote. “Once in possession of the disinfection list, we can provide them an access to start the disinfection for a period of three months. During this time, any PlugX request from an Autonomous System marked for disinfection will be responded to with a removal command or a removal payload.”
READ MORE HERE