MITRE Engenuity™ ATT&CK Evaluations & Framework
Detection and Response
With the MITRE ATT&CK Framework, you can simplify security communications across your organization while providing visibility to your security teams.

Just like you wouldn’t buy a car without doing some research, it just makes sense to look for independent validation that the security solution you are considering delivers what you need. To help CISOs with this complicated task, Trend Micro participated in one of this year’s MITRE Engenuity™ ATT&CK evaluations, which simulated techniques associated with notorious threat groups, Carbanak and FIN7, and how detection and response solutions performed.
See more. Respond faster.
This year’s MITRE Engenuity ATT&CK evaluation included two simulated breaches, one at a bank and one at a hotel, using typical advanced persistent threat (APT) tactics such as elevation of privileges, credential theft, lateral movement, and data exfiltration.
Similar to 2020, Trend Micro garnered impressive results. Here’s how Trend Micro performed against 28 other vendors across 174 simulated attack steps.
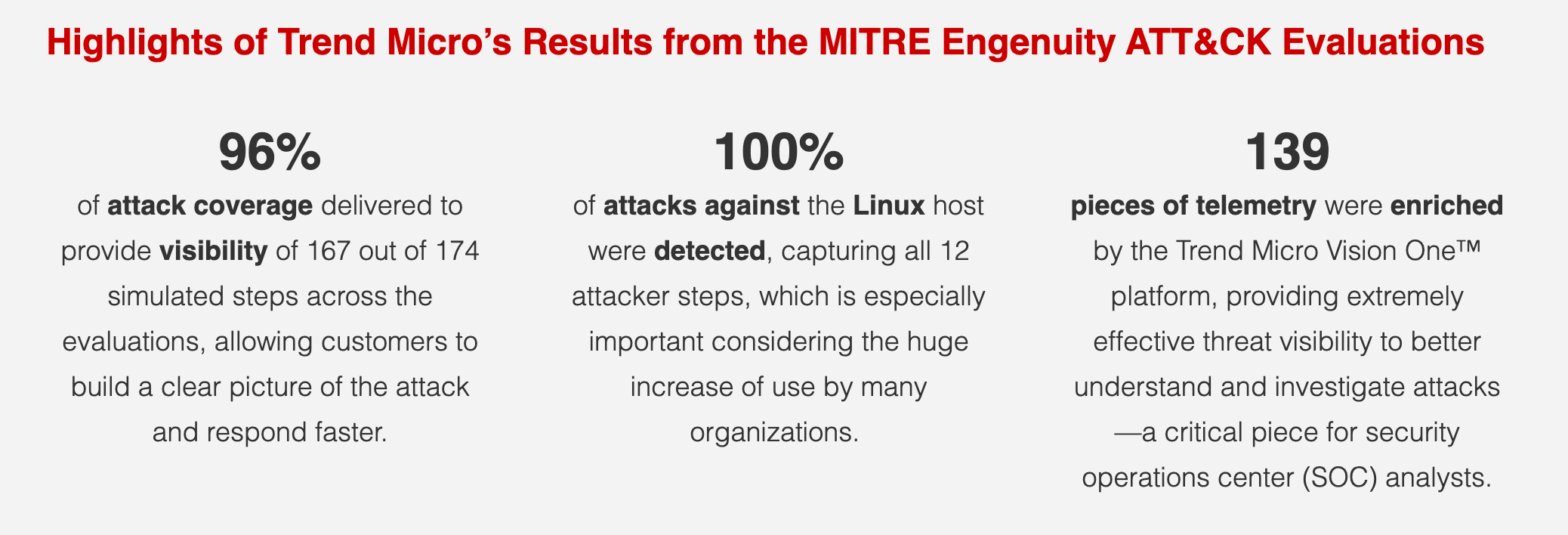
Beyond the numbers
These numbers are great, but how can you use them to make decisions? By aligning the results to the MITRE ATT&CK Framework, the evaluations provide a complete story of the attack. With the MITRE ATT&CK Framework, you can:
- Simplify security communication across your organization
- Provide security teams increased coverage visibility
- Audit for coverage gaps to discover vulnerabilities
After you’ve identified any security gaps, you can then use the evaluations to compare vendors and determine which solutions are best suited for your needs. Thanks to more visibility, you can better identify coverage overlaps, allowing you to optimize costs.
Telling the entire cybersecurity story
At the center of the Trend Micro cybersecurity platform, Trend Micro Vision One™ is a security operations hub that includes extended detection and response (XDR) capabilities that go beyond other XDR solutions. It eliminates siloed information by correlating threat data from multiple security layers, giving you better context of the attack and a centralized view of the chain of events. By connecting the dots, security teams will avoid alert fatigue and be able to focus on critical attacks.
Learn more about the evaluation and attack techniques used on our MITRE Engenuity ATT&CK resource page.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



