New Linux-Based Ransomware Cheerscrypt Targeting ESXi Devices Linked to Leaked Babuk Source Code

Ransomware
New findings showed that Cheerscrypt, a new Linux-based ransomware variant that compromises ESXi servers, was derived from the leaked Babuk source code. We discuss our analysis in this report.
We recently discovered that Cheerscrypt, the new Linux-based ransomware that we detected in multiple attacks targeting ESXi servers, was based on the leaked Babuk source code. Upon scrutiny, we found similarities between Cheerscrypt and the Linux version of the Babuk ransomware, specifically its ESXi version. The base code of Cheerscrypt appears to be derived from the Babuk source code, but modified and customized to suit the malicious actor’s ransomware goals.
This blog entry discusses our findings and provides an overview of Cheerscrypt’s infection routine based on the information we have gathered so far.
Brief background
Over the past few weeks, we observed several Linux-based ransomware detections that malicious actors launched to target VMware ESXi servers, a bare-metal hypervisor for creating and running several virtual machines (VMs) that share the same hard drive storage. We encountered Cheerscrypt, a new ransomware family that has been targeting a customer’s EXSi server used to manage VMware files, during this period.
In the past, ESXi servers were also attacked by other known ransomware families such as LockBit, Hive, and RansomEXX as an efficient way to infect many computers with ransomware.
This blog entry provides an overview of Cheerscrypt’s infection routine based on the information we have gathered so far.
Infection routine
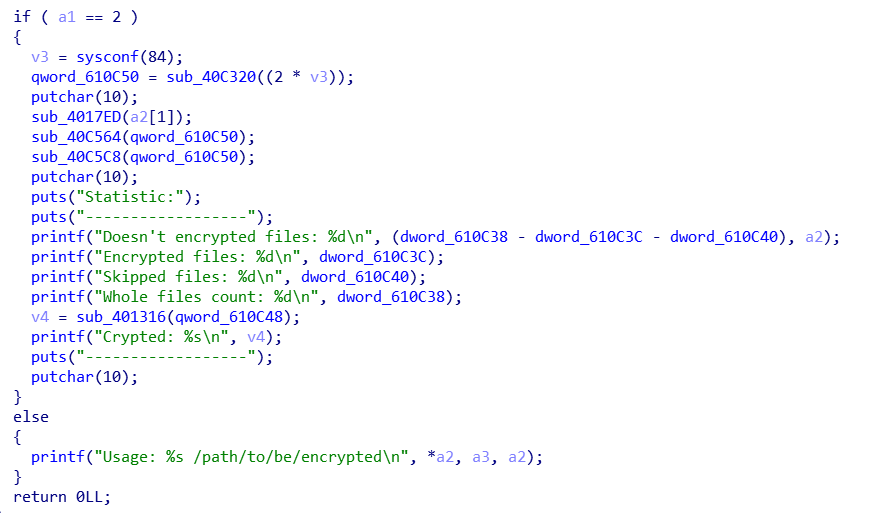
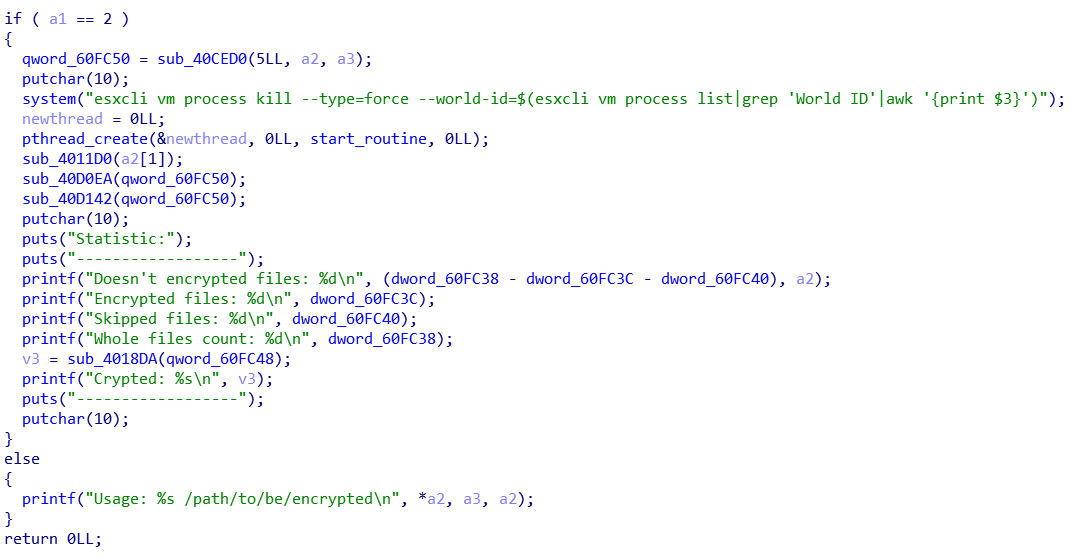
The ransomware requires an input parameter specifying the path to encrypt so that it can proceed to its Infection routine.
Upon execution, it implements the following command to terminate VM processes using ESXCLI:
“esxcli vm process kill –type=force –world-id=$(esxcli vm process list|grep ‘World ID’|awk ‘{print $3}’)”
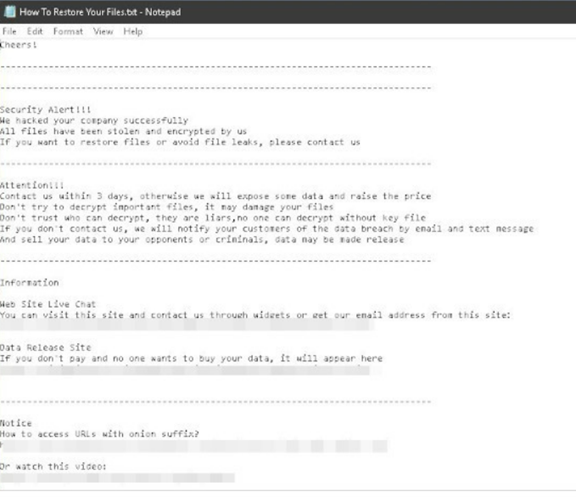
The termination of the VM processes ensures that the ransomware can successfully encrypt VMware-related files. Similar to other infamous ransomware families, Cheerscrypt employs the double extortion scheme to coerce its victim to pay the ransom, as shown on their ransom note in Figure 2.
Successfully encrypted files are renamed with the .Cheers extension. However, the ransomware first renames the files it will encrypt before encrypting the files. Thus, if the access permission for the file was not granted, it cannot proceed with the actual encryption.
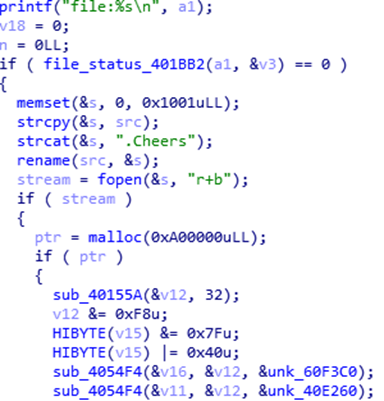
For each directory it encrypts, it will drop the ransom note named, “How to Restore Your Files.txt”. It seeks out log files and VMware-related files with the following extensions:
- · .log
- · .vmdk
- · .vmem
- · .vswp
- · .vmsn
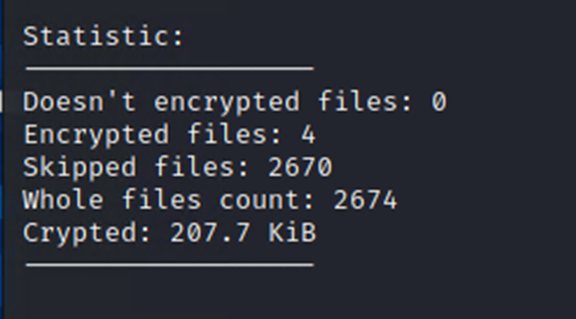
After successful encryption, it displays the following console that contains the data statistics of its routine:
Encryption algorithm
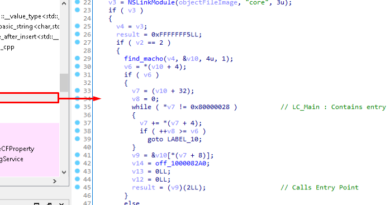
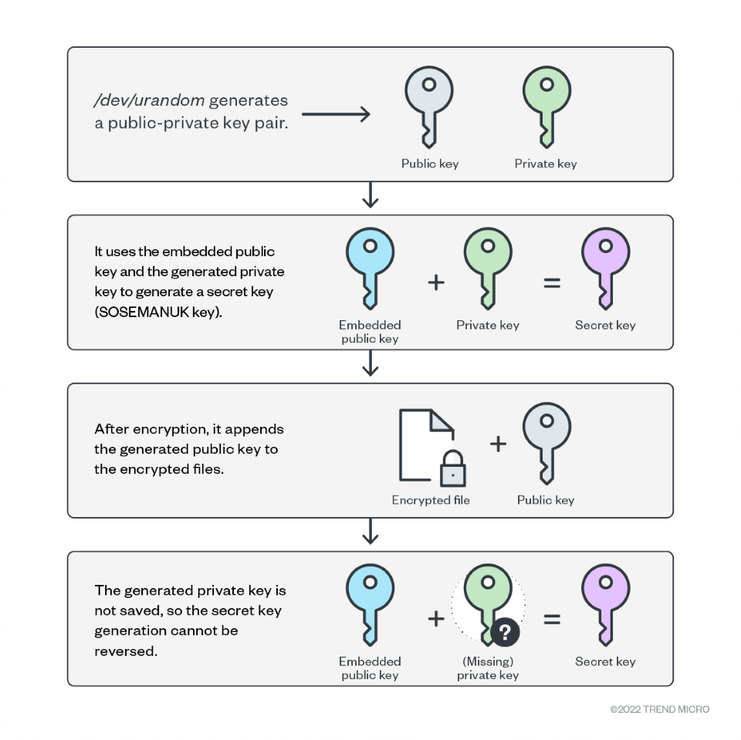
Cheerscrypt’s executable file contains the public key of a matching key pair with the private key being held by the malicious actor. The ransomware uses SOSEMANUK stream cipher to encrypt files and ECDH to generate the SOSEMANUK key. For each file to encrypt, it generates an ECDH public-private key pair on the machine through Linux’s /dev/urandom. It then uses its embedded public key and the generated private key to create a secret key that will be used as a SOSEMANUK key. After encrypting the file, it will append the generated public key to it. Since the generated private key is not saved, one cannot use the embedded public key with the generated private key to produce the secret key. Therefore, decryption is only possible if the malicious actor’s private key is known. The infection chain is shown on Figure 5.
New findings: Cheerscrypt linked to Babuk
Unlike Cheerscrypt, Babuk’s malware version used to compromise ESXi servers ensured that the files were encrypted before it renamed the target files. This goes to show that despite the Babuk ransomware operator’s announcement of their retirement — after claiming they already achieved their goals — their impact can still affect different organizations when other malicious actors build upon the source code they leaked. We provide Babuk’s source code for the malware variant specific to ESXi servers in Figure 6. In Figure 7, we can see that Cheerscrypt’s source code was based on Babuk’s source code that was leaked before.
Conclusion
ESXi is widely used in enterprise settings for server virtualization. It is therefore a popular target for ransomware attacks. As mentioned, compromising ESXi servers has been a scheme used by some notorious cybercriminal groups because it is a means to swiftly spread the ransomware to many devices. Organizations should thus expect malicious actors to upgrade their malware arsenal and breach as many systems and platforms as they can for monetary gain.
Recommendations
A proactive stance that ensures solid cybersecurity defenses against modern ransomware threats is crucial for organizations to thrive in an ever-changing threat landscape. To protect systems against similar attacks, organizations can establish security frameworks that systematically allocate resources based on an enterprise’s needs.
Organizations can benefit from following the security frameworks established by the Center of Internet Security and the National Institute of Standards and Technology when developing their own cybersecurity strategies. The frameworks they created help security teams to mitigate risks and minimize exposure to threats. Adopting the best practices discussed in their respective frameworks can save organizations the time and effort when they customize their own. Their frameworks guide organizations through the entire process of planning while providing suggestions on measures that need to be established first.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE