New research shows IoT and OT innovation is critical to business but comes with significant risks
The need for much improved IoT and operational technology (OT) cybersecurity became clearer this year with recent attacks on network devices,1 surveillance systems,2 an oil pipeline,3 and a water treatment facility,4 to name a few examples.
To better understand the challenges customers are facing, Microsoft partnered with the Ponemon Institute to produce empirical data to help us better understand the state of IoT and OT security from a customer’s perspective. With this data, we hope to better target our cybersecurity investments and to improve the efficacy within Microsoft Defender for IoT, and our other IoT-related products. Ponemon conducted the research by surveying 615 IT, IT security, and OT security practitioners across the United States.
To get an overview of the key findings from the 2021 The State of IoT and OT Cybersecurity in the Enterprise, download the full report.
IoT adoption is critical despite significant security challenges
The research showed that a large majority of respondents believe that IoT and OT adoption is critical to future business success. As a result, they are advancing IoT and OT projects as a key priority.
- 68 percent of respondents say senior management believes IoT and OT are critical to supporting business innovation and other strategic goals.
- 65 percent of respondents say senior management has made it a priority for IT and OT security practitioners to plan, develop, or deploy IoT and OT projects to advance business interests.
Within this group, only a small minority of organizations slowed, limited, or stopped IoT and OT projects even though a majority believe that generally these types of devices are not built with security in mind and that they represent one of the least secured aspects of their IT and OT infrastructure.
- 31 percent of IT security practitioners have slowed, limited, or stopped the adoption of IoT and OT projects due to security concerns.
- 55 percent of respondents do not believe IoT and OT devices have been designed with security in mind.
- 60 percent of respondents say IoT and OT security is one of the least secured aspects of their IT and OT infrastructure.
Based on the data, it appears that business interests are currently taking priority over the increased security risks that organizations assume, as they advance their IoT and OT projects. This puts security and risk leaders in a difficult place and explains why IoT and cyber-physical systems security has become their top concern for the next three to five years.5
“We believe this unique research highlights the obstacles organizations face as they use IoT and OT to drive business innovation with technologies that are more easily compromised than traditional endpoints,” said Dr. Larry Ponemon, Chairman and Founder of Ponemon Institute. “On a positive note, a vast majority of security and risk leaders recognize the threat and have made shoring up their IoT and OT defenses a top priority for the next 12 to 24 months.”
Outdated IoT and OT assumptions are putting organizations at risk
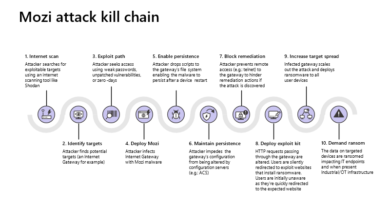
In the past, there was a common assumption about IoT and OT devices that is no longer true. It was assumed that IoT and OT devices were typically segmented from traditional endpoints (workstations, servers, and mobile) or that they were deployed within separate air-gapped networks. The research confirmed that devices on IT and OT networks are frequently connected directly or indirectly to the internet, making them targets that can be breached from outside of the organization. The latest evolution to the Mozi attack1 is a great example of how a business network can be breached through network gear running on the edge of business networks.
- 51 percent of OT networks are connected to corporate IT (business) networks, like SAP and remote access.
- 88 percent of respondents say their enterprise IoT devices are connected to the internet—for instance, for cloud printing services.
- 56 percent of respondents say devices on their OT network are connected to the internet for scenarios like remote access.
It’s critical that these dated assumptions are removed from organizational thinking so that proper mitigations can be put in place.
Key security challenges for IoT and OT devices
When it comes to securing IoT and OT devices, the top challenge is related to visibility. Per the research, only a small subset of respondents shared that they had a complete view of all their IoT and OT asset inventory.
- 29 percent of respondents mentioned that their organizations have a complete inventory of IoT and OT devices. Among them, they have an average of 9,685 devices.
But visibility isn’t just about building a complete asset inventory. It’s also about gaining visibility into the security posture of each IoT and OT device. Questions like “Is the device optimally configured for security,” “Are there any known vulnerabilities in the device’s firmware,” “Is the device communicating or connected directly to the internet,” and “Is the device patched with the latest firmware build?” are some of the questions that organizations need answers to but struggle with for their IoT and OT devices.
- 42 percent of respondents claimed they lack the ability to detect vulnerabilities on IoT and OT devices.
- 64 percent of respondents have low or average confidence that IoT devices are patched and up to date.
Another dimension of visibility that customers are seeking solutions for is related to the ability for organizations to become aware of IoT and OT devices that are involved in attacks. Most of the survey respondents have low to average confidence that the tools they have deployed will be successful in detecting compromised devices.
- 61 percent have low or average confidence in the ability to identify whether IoT devices are compromised.
Another important aspect of visibility worth mentioning is that customers struggle with the ability to efficiently determine how compromised IoT and OT devices are part of broader end-to-end incidents. To resolve attacks completely and decisively, organizations frequently use manual investigation processes to correlate and make sense of the end-to-end attack. Meanwhile, attackers use this time to broaden the attack and get closer to the end goal.
- 47 percent of respondents say their organizations are primarily using manual processes to identify and correlate impacted IoT and OT devices.
IoT and OT attacks are not hypothetical
The Ponemon research shows us that a good percentage of the surveyed respondents are encountering IoT and OT attacks. Nearly 40 percent of respondents told us that they’ve experienced attacks where the IoT and OT devices were either the actual target of the attack (for example, to halt production using human-operated ransomware) or were used to conduct broader attacks (such as lateral movement, evade detection, and persist). Most respondents felt these types of attacks will increase in the years to come.
- 39 percent of respondents experienced a cyber incident in the past two years where an IoT or OT device was the target of the attack.
- 35 percent of respondents say in the past two years their organizations experienced a cyber incident where an IoT device was used by an attacker to conduct a broader attack.
- 63 percent of respondents say the volume of attacks will significantly increase.
One thing to keep in mind with these last three statistics is that the study also showed that customers have low to average confidence in their ability to detect when IoT and OT devices have been compromised. Based on this, it’s likely that the real numbers are higher.
The new Microsoft Defender for IoT is available now for your feedback
Last month at Ignite, we announced that Microsoft Defender for IoT, formerly Azure Defender for IoT, is adding agentless monitoring capabilities to help secure enterprise IoT devices connected to IT networks such as Voice over Internet Protocol (VoIP), printers, and smart TVs. This complements the product’s existing support for industrial systems and critical infrastructure like ICS/SCADA. Additionally, we announced that Defender for IoT is part of the Microsoft SIEM and XDR offering bringing its AI, automation, and expertise to complex multistage attacks that involve IoT and OT devices.

Figure 1. Deep contextual telemetry (like asset and connection details) combined with threat intelligence (like analytics rules, SOAR playbooks, and dashboards) from Section 52 helps analysts perform high-efficiency incident responses.
Microsoft Security would now like to invite you to try out the new public preview of the integrated solution that addresses the challenges surfaced in the Ponemon research, such as complete asset inventory, vulnerability management, threat detection, and correlation. Try the public preview functionality within the Microsoft 365 Defender console or within the Microsoft Defender for IoT experiences. We look forward to hearing and integrating your feedback for the new Microsoft Defender for IoT.
More details on the public preview and roadmap can be viewed in our Ignite session.
Figure 2. Nir Krumer, Principal Program Manager, and Chris Hallum, Senior Product Marketing Manager, discuss securing your Enterprise IoT devices with Microsoft Defender for IoT.
Learn more
More information on the current release of Microsoft Defender for IoT, which offers OT security, can be found in the following resources:
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
1This is why the Mozi botnet will linger on, Charlie Osborne, ZDNet. 1 September 2021.
2‘Thousands’ of Verkada Cameras Affected by Hacking Breach, IFSEC Global Staff, Dark Reading. 10 March 2021.
3Hackers Breached Colonial Pipeline Using Compromised Password, William Turton, Kartikay Mehrotra, Bloomberg. 4 June 2021.
4‘Dangerous Stuff’: Hackers Tried to Poison Water Supply of Florida Town, Frances Robles, Nicole Perlroth, New York Times. 8 February 2021.
5Develop a Security Strategy for Cyber-Physical Systems, Susan Moore, Gartner. 13 April 2021.
READ MORE HERE