Nigerian BEC Scammers Growing Smarter, More Dangerous
Nigerian business email compromise scams are growing more dangerous and sophisticated as cybercriminals add new tools and techniques to their arsenal such as remote access trojans (RATs) and advanced information stealers, researchers found.
Palo Alto Networks’ Unit 42 said in a report released Tuesday about Nigerian cybercrime that they found Nigerian business email compromise (BEC) linked incidents have shot up 45 percent in 2017 compared to the year prior, representing 17,600 attacks per month.
But even beyond soaring cybercriminal incidents, criminals are becoming less of a pesky threat, such as Nigerian Prince 419-style email scams, and more dangerous. Unit 42 said the same threat actors have now adopted damaging RATs such as NetWire and NanoCore, allowing them to strengthen their attacks and cast a wider net when it comes to targeting victims.
According to law enforcement organizations, losses to businesses globally from these threat actors are growing exponentially. “Since January 2015, there has been a 1,300 percent increase in identified exposed losses, now totaling over $3 billion,” according to an FBI statistic quoted by Unit 42 in its report.
“The overarching trend that we should continue to look out for is continued increasing sophistication,” Jen Miller-Osborn, deputy director of threat intelligence at Palo Alto Networks, told Threatpost. “Nigerian threat actors have been characterized as a threat to not take seriously for years. Our ongoing research shows that not taking the threat seriously would be a serious mistake in risk assessment.”
Palo Alto researchers, which have been tracking 15 commodity malware families employed by Nigerian actors over the years, have attributed more than 30,000 samples of malware to roughly 300 unique actors in 2017. Of these malware families, nine represented a more traditional method for Nigerian cybercriminals – information stealers.
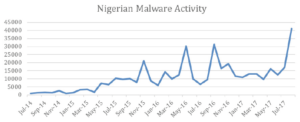 Nigerian actors, which Unit 42 identifies as SilverTerrier, are currently producing an average of 840 unique samples of information stealer malware per month, a 17 percent increase over the past year. The most popular information stealers include the well-known password stealer, Pony, which has existed in varying forms since 2012.
Nigerian actors, which Unit 42 identifies as SilverTerrier, are currently producing an average of 840 unique samples of information stealer malware per month, a 17 percent increase over the past year. The most popular information stealers include the well-known password stealer, Pony, which has existed in varying forms since 2012.
Two new information stealers, hybrid Android malware LokiBot and advanced keystroke logger Agent Tesla, have also emerged as more popular malware tools. “These two families have demonstrated steady growth over the past year, and we anticipate they will continue to climb in popularity and deployment over the next year,” said Palo Alto researchers.
These types of malware were used in a cyberattack discovered in June by Kaspersky Lab, where Nigerian cybercriminals targeted industrial firms to steal a slew of sensitive technical drawings, network diagrams, and project plans using BEC attacks. The bad actors used data sniffing tools from eight different malware families – including ZeuS, Pony, LokiBot, and a variety of RATs.
Beyond information stealers, Nigerian scammers are gaining remote access to compromised systems via a slew of RATs such as remote access trojans NetWire, NanoCore, and DarkComet, which can spy on the victims by taking screen captures or password stealing. Using these tools, hackers can capture keystrokes, monitor web cameras, access network resources and provide remote desktop connections.
Palo Alto said that the actors can now produce an average rate of 146 RAT samples per month – a 49 percent increase over previous years.
In one recently publicized case, a Nigerian scam group behind an array of BEC attacks targeting the shipping industry, called Gold Galleon, utilized these tools, gouging the maritime shipping industry millions of dollars since last year. The group used a range of commodity remote access tools that have keylogging and password-stealing functionality to steal email account credentials.
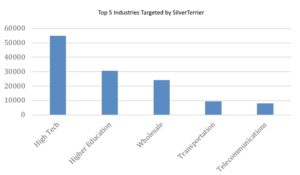 While the capabilities of RATs exceed those of information stealers, the tools require greater technical expertise to employ – indicating that hackers are not just becoming more sophisticated but also have a more substantial infrastructure.
While the capabilities of RATs exceed those of information stealers, the tools require greater technical expertise to employ – indicating that hackers are not just becoming more sophisticated but also have a more substantial infrastructure.
“Additionally, while information stealers transfer data periodically to command-and-control, or C2, servers that actors can check at a time of their choosing, RATs are more complex, requiring interaction with an adversary to be of value,” Palo Alto researchers said. “Given this requirement, [Nigerian] actors often rely on Dynamic DNS and virtual private servers to provide a layer of obfuscation to protect their identities.”
Looking ahead, Palo Alto researchers said it remains clear that Nigerian cyber actors will continue to expand their attacks in terms of size, scope and capabilities. The Nigerian bad actors themselves are mostly educated adults ranging in age from their 20s to 40s, researchers said. Many participate in cybercrime as a means to supplement legitimate employment, and most are currently also leveraging social media platforms as tools to promote organization and collaboration.
Researchers said they estimate 300 unique actors or groups they identify as code name SilverTerrier, or Nigerian-affiliated cybercriminals.
“We have observed that these actors continue to demonstrate increased organization,” researchers said. “The social connections between these actors have become more robust and complex through leveraging social media platforms to promote their networking efforts.”
READ MORE HERE



