odix and Microsoft: Protecting users against malware attacks with free FileWall license
This blog post is part of the Microsoft Intelligent Security Association (MISA) guest blog series. Learn more about MISA.
The fight against malware has become the epic battle of our generation, placing businesses of all sizes against a never-ending stream of hackers and zero-day attacks bent on compromising security perimeters. The recent SolarWinds breach¹ illustrates how much is currently at stake.
According to the Verizon 2020 Data Breach Investigations Report2, an estimated 94 percent of malware is delivered via email with 90 percent of malware hidden in common file types such as PDF, Word, Excel, and Zip.
What is Content Disarm and Reconstruction (CDR)?
CDR describes the process of creating a safe copy of an original file by including only the safe elements from the original file. The process offers a detection-less and streamlined solution that is notably different from common sandbox-based antimalware tools in the market.
On a granular level, CDR focuses on verifying the validity of the file structure on the binary level and disarms both known and unknown threats.
With CDR, most malware forms–including zero-days, which are maliciously embedded in transit files–are sanitized and purged of malicious content. This ensures the end-user can access only malware-free content, while still maintaining maximum file functionality.
odix, an Israel-based cybersecurity company leading the way in content disarm and reconstruction technology, has developed a range of solutions to fully complement and strengthen existing Microsoft security systems. Through the addition of FileWall, a Microsoft certified Cloud Solution Provider (CSP) can easily improve email security within a few clicks.
FileWall’s granular type filter optimizes administrator’s malware protection capabilities, allowing them to easily ensure only necessary file types can get through to the end-user, according to their varying file access permissions. The FileWall type filter ideally leverages CDR technology to purge embedded and nested files. By adding the CDR process to Microsoft’s existing sandbox-based protections, users are better prepared to defend against the threats of unknown malware.
How FileWall integrates with Microsoft security technology
odix’s FileWall solution was created from square one to fully integrate with the Microsoft Graph Security API, Microsoft Azure Sentinel, and Exchange Online. As a result of odix’s native level integration with many of Microsoft’s core security mechanisms, FileWall’s deep file inspection capabilities don’t impact latency or compromise Microsoft’s native security protection. FileWall’s integration enables simultaneous reporting of malicious events and embedded suspicious content discovered within files to Microsoft Azure Sentinel.
For the user in complex file scenarios, such as nested files, password-protected attachments where traditional sandbox methods could miss or result in lengthy-time delays, and disruption of business processes, FileWall relies upon a detection-less process to remove unknown malware and block malicious elements embedded in files. FileWall provides near-instant sanitization and reconstruction of files with simple click deployment.
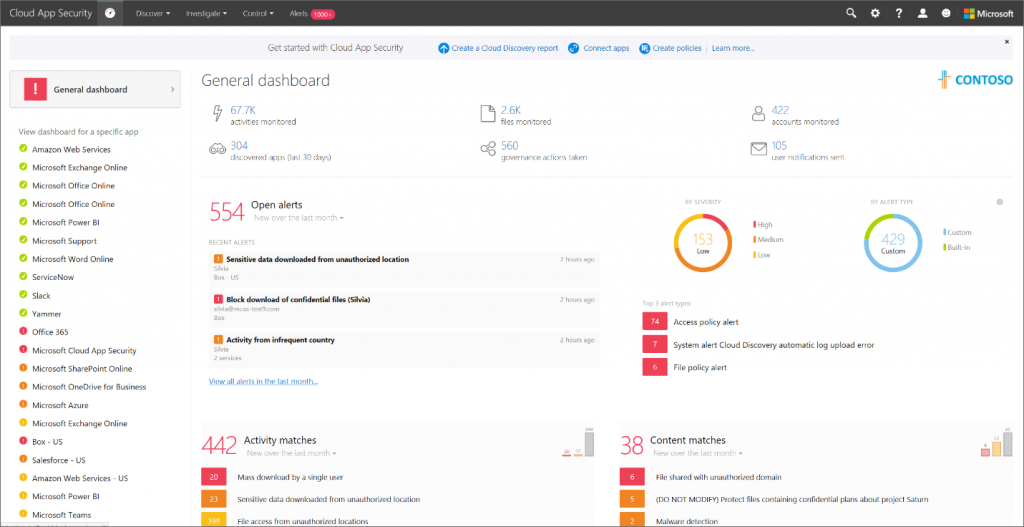
FileWall provides maximum security cooperation and allows for greater visibility of incoming files and triggers an automated response from Microsoft Exchange Online to mitigate the impact of malware accordingly.
Microsoft 365 and Exchange Online administrators can get a free license of FileWall here.

Protecting emails: FileWall’s granular type filter
The FileWall file type filter allows the Microsoft 365 system admin to define which file types are permitted to enter the organization and which should be blocked. This minimizes the attack surface the organization is exposing via email by eliminating the threat vectors available in certain file types.

The type filter has three main controls:
- On/Off: Enabling or disabling the filter functionality on all file types.
- Work mode (Whitelist/Blacklist): The ability to create pre-set lists of permitted and non-permitted file types for specific users within the organization.
- Default settings: Suggested default policy by FileWall which includes 204 file types categorized as dangerous [including executable files (exe)], windows batch files (bat), windows links (lnk), and others.
The sandbox can manage executables and active content. This allows the sandbox to work only on files that were not treated by FileWall. As most organizational traffic consists of non-executable documents, this method can reduce sandbox load by 90 to 95 percent, lowering the total costs and improving the average latency.

FileWall complements Exchange Online security capabilities
As a native-level security add-on within Microsoft Exchange Online, with no SMTP relay required, FileWall doesn’t harm productivity. Consequently, all FileWall’s settings have been configured to complement existing security protocols. FileWall’s speed in processing files is near-instantaneous for common file types.

Learn more
odix is an industry leader in developing and optimizing CDR technology for the enterprise and small and medium business markets. odix’s flagship CDR add-on, FileWall, is available for direct purchase in the Microsoft marketplaces.
FileWall has already proven its worth in the field, providing best-in-class email protection in a broad range of IT and industrial settings. Clariter, a global clean-tech company, was seeking an additional security layer to enhance its email security systems and found FileWall the ideal solution. Read the full case study here.
To learn more about FileWall, visit our listing in the Azure Marketplace.
To learn more about the Microsoft Intelligent Security Association (MISA), visit our website, where you can learn about the MISA program, product integrations and find MISA members. Visit the video playlist to learn about the strength of member integrations with Microsoft products.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
¹SolarWinds hack was ‘largest and most sophisticated attack’ ever: Microsoft president, The Associated Press, February 14, 2021.
22020 Data Breach Investigations Report, Verizon Business, May 19, 2020.
READ MORE HERE