Over A Million Neighbourhood Watch Members Exposed
Neighbourhood Watch (NW) groups across the UK can now rest easy knowing the developers behind a communications platform fixed a web app bug that leaked their data en masse.
Nottingham-based VISAV is the company behind Neighbourhood Alert, a platform that, among other things, claims to offer a secure messaging system between registered NW community members and authorized administrators.
Neighbourhood Alert is accessible through web and mobile apps that are endorsed by national and regional local authorities across the UK. It has more than half a million users, according to its website.
In late March, one user reported a security issue to El Reg that allowed anyone to register as a NW coordinator on the platform and create what’s known as a scheme. This can be a sub-region such as a block of 15 streets within a wider NW area, such as a city. After selecting a scheme – done by drawing an area within the platform’s digital map integration as large as they wished – those who created the scheme could see all NW members in that area.
The problem was that these coordinators crucially didn’t have to pass an approval or verification process. The data was accessible immediately after signing up with throwaway credentials.
An investigation by The Register revealed that anyone could sign up using a fake name, email address, and postal code to gain access to a range of personal data on UK citizens within minutes.
After drawing a scheme, unverified users could select an option to view the details of every registered NW member in that area, which included full names, home and email addresses, phone numbers (where supplied), and small profile images in the rare cases users uploaded one.
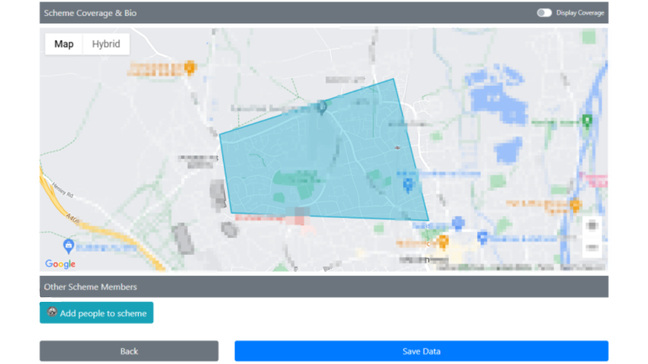
Neighbourhood Alert’s map-based geographical catchment selector
The only limit on the size of the map a potential data harvester could draw was that of the region with which they registered. Neighbourhood Alert has bespoke platforms for each region of the UK that adopted the platform, such as Manchester, Cambridgeshire, etc.
Those who registered for Greater Manchester’s deployment of the platform could create a scheme that captured thousands of individuals’ data in one fell swoop. The same was true in other regions, according to tests.
Like the accounts used to create them, these schemes didn’t need to be approved by any existing users or admins in the region before the data residing within them could be accessed.
In some cases, searches revealed members who had registered using official email addresses, including police officers and MPs, potentially allowing criminals to locate their homes. Other high-profile individuals, or those with a reasonably elevated expectation of privacy, were also discoverable.
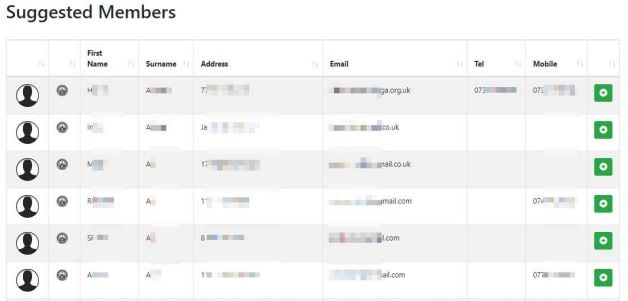
Neighbourhood Alert member data displayed to an unvetted user after creating a scheme
Mike Douglas, product director and also the person responsible for data protection at VISAV, disclosed the issue to users on April 15 in an email seen by The Register, calling the flaw a “security anomaly.”
In a statement issued to us directly, he said: “Since we were first made aware that our system had been used in an attempt to access member’s data we have been open and transparent to resolve this issue.
“We are sincerely sorry for any distress caused to all our registered members due to this unusual risk of a leak taking place. As a trusted British business, integrity and public safety is of utmost importance to us. Threats to cybersecurity are now a daily part of our lives and at VISAV and we take our data protection obligations very seriously.
“The anomaly was fixed immediately, and we have voluntarily notified every member to inform them and provide guidance, even the vast majority of members who were not potentially affected by it. We have also reported ourselves to the regulator to support our own intensive investigation and help prevent future risks.”
UK data protection watchdog the Information Commissioner’s Office confirmed VISAV reported itself and that the information provided is now being assessed. ®
READ MORE HERE



