Panda Banking Trojan Diversifies into Cryptocurrency, Porn, Other Targets
The Panda banking trojan, a spin-off from the infamous Zeus malware, is widening its net to attack more than just financial services targets, as seen in three ongoing campaigns discovered in May.
The Windows-focused Panda is far from the cuddly thing its name would suggest. It has a full arsenal of attack techniques, which include web injects, taking screenshots (up to 100 per mouse-click), keylogging, the ability to grab passwords from the clipboard and paste them into form fields and exploits for the Virtual Network Computing desktop-sharing system.
First seen in 2016 as one of the many variants that cropped up in the wake of the Zeus source code being leaked, Panda has more than adequately fulfilled its function as a banking trojan since then, looking to harvest and use credentials for online banking, payment and other financial portals.
Three New Active Campaigns
However, in three active campaigns spotted this month by F5 Labs, Panda has been observed attacking online cryptocurrency exchanges and brokerage services, social media and adult sites, among others. F5 researcher Doron Voolf postulated that the sheer size of these other industries translates to a siren song of potential revenue generation for fraudsters.
“Adult sites were also targeted by Panda… We have been seeing an expansion of banking trojan targets into other industries that collect payment information and other forms of personally identifiable information (PII), so this behavior is not surprising,” he said, in an analysis posted on Wednesday. “[T]his behavior is not surprising given the size of the adult industry and potential revenue generation for fraudsters.”
All three of the 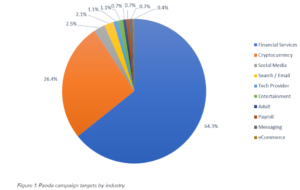 offensives (active in the U.S., Japan and Latin America) are propagating via Facebook and Twitter phishing attacks, and all three have added the same new targets to the mix, the researchers noted. However, there are different C2s for each campaign. Two of the attacks are acting from the same botnet version. Botnet 2.6.8 was found spreading Panda in both the U.S. and Japan.
offensives (active in the U.S., Japan and Latin America) are propagating via Facebook and Twitter phishing attacks, and all three have added the same new targets to the mix, the researchers noted. However, there are different C2s for each campaign. Two of the attacks are acting from the same botnet version. Botnet 2.6.8 was found spreading Panda in both the U.S. and Japan.
The U.S. campaign so far has targets in eight industries. While 76 percent of the attacked services are for U.S. financial organizations such as Citibank and Wells Fargo, the actors behind the campaign have also added half a dozen Canadian financial organizations as targets. That’s followed notably by cryptocurrency sites. Also targeted are global social-media providers Facebook and Instagram along with MSN and Bing.com, payroll companies, entertainment services (YouTube) and others, Voolf said.
“This campaign also targets the ecommerce giant Amazon; entertainment platform Youtube; Microsoft.com, Live.com, Yahoo.com, Google.com, likely targeting email accounts; the social media leaders Facebook and Twitter; as well as a Japanese adult site Dmm[.]co, and Pornhub,” researchers wrote.
In both of the initiatives, F5 said that the registrant is via a known threat actor network in Russia, and the domain for the email contact is bk.ru, which is owned by ASN 47764 – an entity that Voolf said continually comes up in F5’s threat research.
As for the Latin American campaign, it’s primarily focused on banks in Argentina, Columbia and Ecuador. That is followed by similar social media targets (Facebook, Twitter, Instagram and Flickr) as well as MSN, Bing.com, YouTube and Microsoft.
F5 said the botnet behind the Latin American campaign is called Cosmos3. Researchers note, while the domain is registered in China, the email registrant domain is GMZ.com and resolves to the German service provider 1&1.
Across all three campaigns, just 64 percent of targets were financial services targets. Cryptocurrency exchanges made up 26 percent. That’s a big change for this kind of malware, Voolf said.
“This is the first [Panda] campaign we have seen targeting cryptocurrency sites, but it’s a move that makes sense, given the popularity of cryptocurrency,” he concluded. “This act of simultaneous campaigns targeting several regions around the world and industries indicates these are highly active threat actors, and we expect their efforts to continue with multiple new campaigns coming out as their current efforts are discovered and taken down.”
Panda isn’t the first banking trojan to turn its interest to cryptocurrency; IBM X-Force noted in February that the TrickBot trojan has been diversifying its interests as well.
Read More HERE