ParaSiteSnatcher: How Malicious Chrome Extensions Target Brazil

Our investigations on potential security threats uncovered a malicious Google Chrome extension that we named “ParaSiteSnatcher.” The ParaSiteSnatcher framework allows threat actors to monitor, manipulate, and exfiltrate highly sensitive information from multiple sources. ParaSiteSnatcher also utilizes the powerful Chrome Browser API to intercept and exfiltrate all POST requests containing sensitive account and financial information before the HTTP request initiates a transmission control protocol (TCP) connection.
Our research shows that the malicious extension is specifically designed to target users in Latin America, particularly Brazil; it exfiltrates data from Banco do Brasil- and Caixa Econômica Federal (Caixa)-related URLs. It can also initiate and manipulate transactions in PIX, a Brazilian instant payment ecosystem, and payments made through Boleto Bancario, another payment method regulated by the Bank of Brazil. We also observed that it can exfiltrate Brazilian Tax ID numbers for both individuals and businesses, as well as cookies, including those used for Microsoft accounts.
Once installed, the extension manifests with the help of extensive permissions enabled through the Chrome extension, allowing it to manipulate web sessions, web requests, and track user interactions across multiple tabs using the Chrome tabs API. The malware includes various components that facilitate its operation, content scripts that enable malicious code injection into web pages, monitor Chrome tabs, and intercept user input and web browser communication.
It is worth noting that while ParaSiteSnatcher specifically targets Google Chrome browsers, the malicious extension will also work on browsers that support Chrome extension API and runtime, such as Chromium-based browsers like newer versions of Microsoft Edge, Brave, and Opera. These extensions could potentially be compatible with Firefox and Safari as well, but changes such as the browser namespace are necessary.
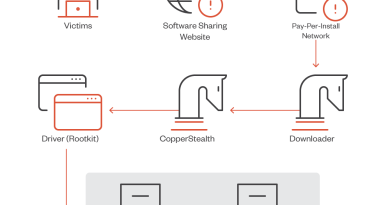
The ParaSiteSnatcher downloader
ParaSiteSnatcher is downloaded through a VBScript downloader hosted on Dropbox and Google Cloud and installed onto an infected system.
Our analysis has identified three distinct variants of the VBScript downloader, which are characterized by differing levels of obfuscation and complexity:
- Variant 1. This variant presents a straightforward approach where the payload is not obfuscated, making it relatively easier to analyze and understand.
- Variant 2. In this iteration, critical strings within the payload are obfuscated using a Reverse String technique. This adds a layer of complexity to the code, requiring a reverse operation to decipher the original content.
- Variant 3. This variant incorporates additional obfuscation techniques. It includes junk code that serves to confuse the analysis process, anti-debug and anti-tamper protections, alongside the use of randomly generated names for variables and functions to prevent easy pattern detection. It also utilizes Reverse String obfuscation to further conceal the payload, presenting a more challenging structure for analysts to decipher.
Upon execution, the downloader performs an initial check for the presence of the %ProgramFiles%\Google\Chrome\Application\chrome.exe file, and the %APPDATA%\%USERNAME% folder. If found not present, the script will terminate its process.
Read More HERE