Post-Quantum Cryptography Set to Replace RSA, AES, ECC
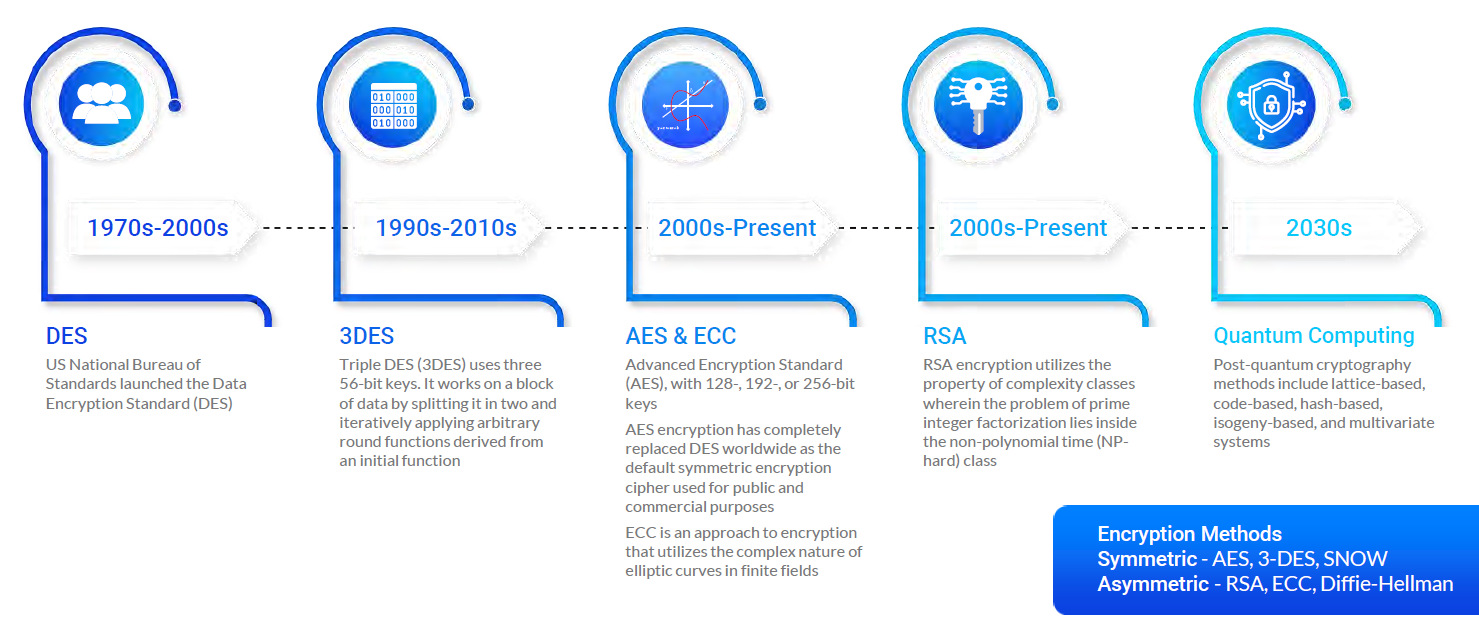
Within a decade, the growth of powerful quantum computers will lead to a new era in security, in which once-impenetrable public-key techniques like RSA, AES, and ECC will fall to higher levels of brute force. Such techniques need to be replaced by post-quantum cryptography that can stand up to the new challenges.
That’s according to an intelligence brief from research company PreScouter. The brief, titled “Quantum Computing and Cybersecurity: Preparing for Post-Quantum Cryptography,” says the global quantum computing market will grow from $472 million in 2021 to $1.765 billion by 2026. As the technology spreads from research labs to the cloud, the likelihood of it getting used to defeat current encryption methods rises to near certainty. Indeed, the Biden administration just issued two directives to prepare US government and businesses against future quantum cyberattacks.
“Hackers are currently unlikely to have the resources to develop quantum computing systems,” the PreScouter brief states. “However, the emergence of general-purpose quantum computing will be available in the cloud as an infrastructure platform like a service, making it affordable for a wide range of users with current technological capabilities.” IBM added its Quantum Cloud service back in 2017, and today users can rent time on a quantum computer from more than a dozen vendors, including Azure and AWS.
Numerous groups have been working on post-quantum cryptography for years, including European Telecommunication Standards Institute (ETSI), the European Union Agency for Cybersecurity (ENISA), and the International Organization for Standardization (ISO). In the US, NIST initiated its post-quantum work back in 2016. This foresight is necessary, PreScouter says, because replacing encryption algorithms requires many steps, so the sooner we get started, the better.
The brief notes that while hackers might not be breaking into OT systems and medical devices by 2030, we need to have post-quantum cryptography implemented by then to stave off such attacks. Algorithmic approaches to post-quantum cryptography include lattice-based, hash-based, isogeny-based, multivariate, and code-based systems.
Download the brief in full from PreScouter.
Read More HERE
