Prioritize Security Controls for Critical AWS Assets Cloud Advocate


Leveraging this matrix helps you check if all your bases are covered and if you need to fill any gaps. The functions of the cyber defense matrix—identify, protect, detect, respond, and recover—embody the five operational functions of the NIST Cybersecurity Framework (CSF). The assets—devices, applications, networks, data, and users—refers to what needs to be secured.
We’re focusing primarily on the left side of the matrix, or rather before the “boom,” which refers to the point between protect and detect where some event occurs. Ideally, you want to avoid a boom. You can do so by shifting security left (get it?) and prioritizing the identify and protect functions.
When you prioritize security by shifting it to the forefront, it ensures your application is in tip top shape from inception to creation, instead of having to scramble to remediate issues after the boom.
The identify function means understanding what the organization needs to be secure and getting everyone on the same page. Security isn’t one-size-fits-all, so it’s important that the business context is considered.
The protect function is essentially creating a game plan to make sure everything goes smoothly. This is where using the DIE model to build cattle is essential. Since DIE encourages security by design, you can limit the impact of a cybersecurity issue.
As we mentioned earlier, using the cloud-native capabilities of AWS services like Lambda and CloudFormation serve as great building blocks for a strong application. But integrating another layer of security provides a powerful one-two punch to keep the bad guys away.
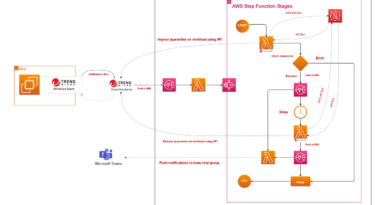
How Trend Micro Cloud One™ helps
Purpose built for cloud builders, Trend Micro Cloud One™ is a platform of seven security services that provide protection throughout the development process. AWS customers can leverage this innovative platform thanks to powerful APIs for an extra layer of defense that enhances your security posture.
Using our handy cyber defense matrix, let’s look at how the seven services stack up:
Read More HERE