Privacy compliance for smart meter infrastructure with Microsoft Information Protection and Azure Purview
Smart meters and smart grid infrastructure have been deployed in many of the world’s electric distribution grids. They promise energy conservation, better grid management for utilities, electricity theft reduction, and a host of value-added services for consumers. To deliver on this promise, they need to collect granular electric usage data and make this available to the stakeholders who need it. This has created consumer privacy concerns which are being addressed with security and governance programs, like Microsoft Information Protection and Azure Purview, and with regulation by the government. The ability to protect and govern smart meter data is critical to addressing consumer privacy. It’s also critical to making the data available to realize the return on investment in terms of environment, safety, savings, and enhanced services to consumers.
Smart grid data contains private information
Smart meter data is personally identifiable information (PII). Information potentially available through the smart grid includes:

Figure 1: Information potentially available through the smart grid.1
This gives rise to a range of privacy concerns from personal data exposure for embarrassment or extortion, determination of behavior patterns for unwanted marketing, by criminals who might be casing a premises or seeking to exploit children, or inappropriate uses by government.
Depending on the granularity and character of data collected, smart meter data can be disaggregated to reveal private information:

Figure 2: Using hidden Markov models to produce an appliance disaggregation.2
Electric meter data was generally not a focus of privacy concern prior to smart meters. With smart meters, there is the potential for the data to be near real-time and with a frequency and granularity not previously available. The potential value of smart meter data for demand management programs, time of use pricing, outage management, grid optimization, energy theft reduction, unlocking the value of smart cities, and other uses increases as does the frequency and granularity of the data.
Utilities and other stakeholders need to do a privacy impact assessment (PIA) for the use of this data. Part of this process is to set out the controls that will be used to govern the data.
Many of the same regulations and standards that cover PII in general apply to smart meter information. These include General Data Protection Regulation (GDPR), California Consumer Privacy Act, Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA), Brazil’s General Data Protection Act (LGPD), and many other established and emerging privacy regimes. A geographic summary of privacy regulations is provided by the global law firm DLA Piper.
Where is PII from smart meters located?
Smart meter data is in the meters themselves and the backhaul infrastructure, potentially passing through range extenders, connected grid routers on its way to the head end. From here it is made available to the utility departments and other organizations as permitted in databases and data reservoirs to derive value from the data.

Figure 3: Conceptual reference diagram for smart grid information networks.3
With the range of stakeholders that need access to the data, there will be a variety of technologies and architectures that must be governed. Broadly, there will be PII in structured resources like SQL or SAP S/4HANA databases, and unstructured like desktop application files and email or data repositories like Azure Blob, Data Lake Storage, or Amazon S3.
The data should be governed during its full lifecycle from collection through to secure auditable disposal—both inside the utility’s environment and outside as third parties access the data for permitted uses.
Protect and governing PII from smart meters
The Microsoft Information Protection and Governance framework protects and governs Microsoft 365 data, including desktop applications, email, on-premises repositories, and with Microsoft Cloud App Security, both in our own- and third-party clouds and on Windows 10 endpoints like laptops.
Most impactful for smart meter data, we now have Azure Purview (now in preview) for structured and unstructured data outside of Microsoft 365, such as in databases, data lakes, SAP, and a range of other environments where smart meter data is stored and used to extract value.

Figure 4: Microsoft Information Protection and Governance.
To properly protect and govern PII in smart grid data, we need to identify and inventory this data across our cloud and on-premises environment. We need to protect this data with durable security policies that stay with the data throughout its lifecycle. We need to implement Data Loss Prevention (DLP) to keep the information from traveling to places it should not go and we need to dispose of data when it’s no longer needed for business purposes. The deletion should be permanent and auditable.
Microsoft Information Protection as part of Microsoft 365 provides the tools to know your data, protect your data, and prevent data loss. It provides users with a native experience in their documents and emails, providing automation to recognize PII and either recommend the user apply a sensitivity label with the option to override this suggestion with auditable justification to enforce the application of the label.

Figure 5: Microsoft Information Protection provides real-time assistance to users with a native experience while they work.
The sensitivity label can enforce encryption, scoping the document to be consumed only by the intended organization, teams, or individuals. It can enforce watermarking, disable cut and paste, and a range of other security policies for the life of the document, even when it leaves the sender’s environment.
PII such as credit card numbers can be recognized as out-of-box sensitive information types and then be tuned to reduce false positives. Custom sensitive information types can be informed by keywords, keyword dictionaries, or regular expressions which are particularly useful for recognizing utility account numbers or smart meter numbers. Machine learning can be used to recognize documents by using trainable classifiers to reason over a sample of relevant documents to recognize documents that are like these.
Sensitive data can be identified, inventoried, and protected as it is created, in the cloud with Microsoft Cloud App Security (MCAS) or with on-premises resources using the Azure Information Protection (AIP) scanner.
These sensitivity labels and sensitive information types can trigger DLP policies across email, desktop applications, SharePoint sites, OneDrive, Windows 10 devices, Teams, and third-party clouds. The policies are managed with a unified experience across Office 365, cloud, on-premises, and endpoint locations.

Figure 6: Selections of locations to apply policy.
Files and emails can be tagged with retention labels as well as sensitivity labels. Like sensitivity labels in Microsoft Information Protection, they can be applied manually or in an automated way based on out-of-box, custom information types, or machine learning with trainable classifiers.

Figure 7: Records management.
Retention labels can enforce auditable retention, deletion, and disposition review of documents and emails in the Microsoft 365 tenant.
This can facilitate compliance with privacy regulations, but also regulations that require retention for discovery purposes such as utility commissions or Freedom of Information (FOI) requests.
Visualization and reporting for sensitive data, including smart meter PII as well as the retention labels and policies applied, are available from the compliance portal so that sensitive data can be inventoried, managed, and reported on.
Azure Purview
Azure Purview is a unified data governance service that helps you manage and govern your on-premises, multi-cloud, and software as a service (SaaS) data. We’ll focus on PII data discovery in this post.
Azure Purview Data Map captures metadata across a wide range of data sources and file types with automated data discovery and sensitive data classification. Azure Purview extends our information protection and governance capabilities beyond Microsoft 365.
Among the broad list of data sources, you’ll be able to scan SQL databases, Azure Blob Storage, Azure Data Lake Storage, Azure Cosmos DB, AWS S3 buckets, Oracle databases, SAP ECC, and SAP S/4HANA.

Figure 8: Metadata map.
The data in these sources can be classified and labeled by out-of-box and custom sensitive information types, including those defined for smart grid PII.

Figure 9: Microsoft Azure Purview classification rules.
The sensitive information types and sensitivity labels are made available to Azure Purview from the Microsoft 365 Compliance Center, the same place the Microsoft Information Protection rules are managed, creating a unified experience for the administrators.

Figure 10: How to edit label sensitivity.
Custom classifications and rules to identify custom sensitive data types or keywords can be created in the Azure Purview solution.
Azure Purview provides reporting that shows where sensitive data such as PII is located across an organization’s data estate. Sensitivity labels with security policy can be applied to this data. The repositories where sensitive data is located can have additional security added or the data can be removed from locations where it does not belong.

Figure 11: Azure Purview showing locations where sensitive data exists.
Azure Purview can validate that the Data Privacy Impact Assessment (DPIA) and controls undertaken by an organization around sensitive smart grid data are being enforced. This reporting can provide evidence to a regulator that an organization’s commitments to security and privacy that enabled the use of customer’s private data have been upheld.
Azure Purview does not move or store customer data outside of the geographic region in which it is deployed so data residency requirements can be met.
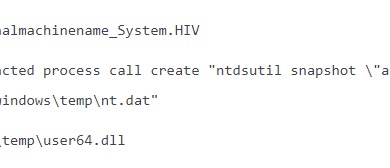
In addition to helping protect sensitive data, Microsoft also offers agentless, security monitoring for industrial control system (ICS) and operational technology (OT) networks to rapidly detect and respond to anomalous or unauthorized activities in control networks. Azure Defender for IoT integrates with existing security operations center (SOC) tools (like Azure Sentinel, Splunk, IBM QRadar, and ServiceNow), is broadly deployed in production across power distribution and generation sites worldwide, and is available for both on-premises and cloud-connected environments.
Microsoft 365 Information Protection and Governance and Azure Purview together provide tools to protect and govern smart meter data and other sensitive data for utilities. The more effectively we can implement protection and governance of this data, the more we can make use of it and derive value for the ratepayers who have invested in the smart grid.
Learn more
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
1NISTIR 7628, Guidelines for Smart Grid Cybersecurity volume 2, Table 5-1.
2NISTIR 7628, Guidelines for Smart Grid Cybersecurity volume 2.
3NIST Special Publication 1108R2.
READ MORE HERE