Proofpoint phishing palaver plagues millions with ‘perfectly spoofed’ emails from IBM, Nike, Disney, others
A huge phishing campaign exploited a security blind-spot in Proofpoint’s email filtering systems to send an average of three million “perfectly spoofed” messages a day purporting to be from Disney, IBM, Nike, Best Buy, and Coca-Cola – all of which are Proofpoint customers.
As far as victims were concerned, they were getting real emails from big corporations, with properly authenticated Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) signatures – indicating to users and their email apps that the missives were legit and trustworthy.
The fake emails would, for example, attempt to convince marks to click through to malicious sites that would try to phish their credit card details by telling them they could renew an online subscription for a special low, low price. Folks who typed in their card info would in fact be billed more than 100 times as much a month, for nothing in return.
The spam campaign ran from January to June, and at peak times reached 14 million dodgy emails within a 24-hour period, according to Guardio Security, which notified security tool maker Proofpoint in May about the exploitable weakness and assisted with subsequent mitigation efforts.
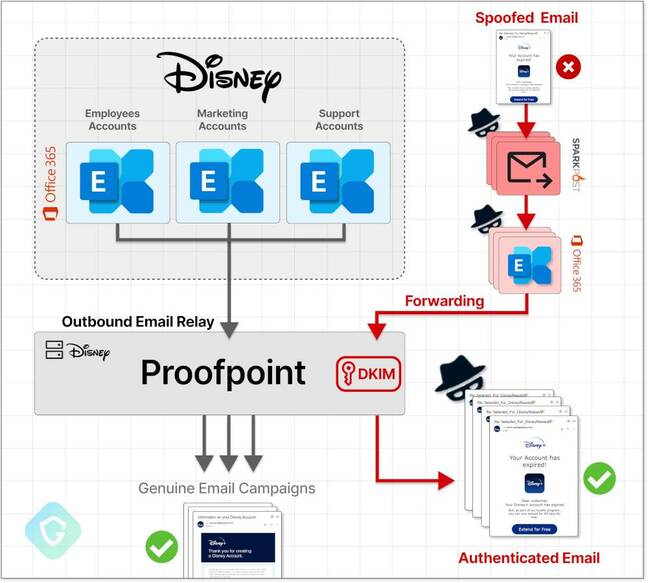
Guardio dubbed the campaign EchoSpoofing – because the spam was “echoed” from email relay servers owned and operated by Proofpoint itself.
Proofpoint, which said it spotted the spam campaign in late March, conceded that miscreants abused “a small number” of its customers’ Microsoft 365 accounts, and added: “This issue did not expose any Proofpoint customer data, and no customer experienced any data loss as a result.”
The spammers abused an insecure-by-default Proofpoint email routing feature to send messages with valid SPF and DKIM signatures of top corporations via Proofpoint’s email relays. Large organizations such as Disney use Microsoft 365 to handle their mail, but route incoming and outgoing messages through Proofpoint’s systems that act as a security filter.
Crucially, Disney’s setup, with its Proofpoint filtering, ensured that its outgoing mail via Proofpoint appeared to recipients as if it was coming officially from Disney with all the correct SPF and DKIM signatures added. It’s this level of trust that was abused by spammers to send out all those legit-looking messages.
Simply put, the miscreants just needed to spam out mail from one or more rogue SMTP servers and have it forward relayed via their own Microsoft 365 tenant accounts to Proofpoint.
All that mail at that point would be crudely and unconvincingly spoofed to appear to come from, say, Disney. It did not matter that these bogus messages were obviously fake and originated from non-Disney servers: Proofpoint would see them arrive from Microsoft 365, think the messages truly came from Disney, and then echo the emails with all the correct security signatures added to the spam recipients.
Why would Proofpoint allow such a thing to happen? Because its affected customers had each enabled Microsoft 365 integration with Proofpoint’s filtering service but not locked down who exactly could send email via that product as them. As Proofpoint put it:
Or as Guardio explained, the routing feature was not secure by default, needed some fiddling with settings to shore it up, and Proofpoint’s customers didn’t realize this. “There are ways to add specific rules to [your] Proofpoint account to prevent this and other kinds of spoofing by manually filtering emails from unknown sources and other specific headers and properties.
“However, this process is entirely manual and requires custom rules, scripts, and maintenance … Most customers were not aware of this in the first place, and the default option was not secure at all.”
To address this, Proofpoint said it revised its configuration system:
Millions of spam messages were sent to users of Yahoo, Gmail, GMX.com, and others. And according to Guardio, they originated from virtual private servers mostly hosted on French cloud OVH and managed with the PowerMTA email delivery software.
Proofpoint, in its analysis of the campaign, published a list of Microsoft tenants used by the spammers to forward relay messages.
“As of the publication of this blog, many are still active,” the email security vendor warned, noting that it has taken steps to automatically block attempts by those accounts to relay through its servers. ®
READ MORE HERE