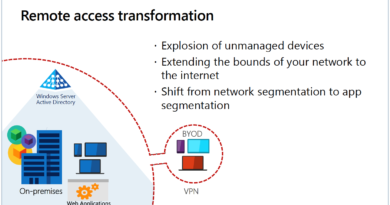
Protecting SAP applications with the new Azure Sentinel SAP threat monitoring solution
As one of the leading solution providers for applications that manage business processes, SAP is the custodian for massive amounts of sensitive data in many of the biggest organizations in the world.
Since these applications are business-critical, an SAP security breach can be catastrophic. Yet, protecting SAP applications is uniquely challenging. These systems are growing in complexity as organizations expand them beyond base capabilities. They are vulnerable not only to outside attacks, but also insider threats. What’s more, their complex nature means that threats can emerge across multiple modules, making cross-correlation especially important.
It has been traditionally very difficult for security operations (SecOps) teams to effectively monitor them due to the unique nature of the SAP ecosystems and the expertise they require. We set out to meet this challenge with the new SAP threat monitoring solution for Azure Sentinel. Now in public preview, the solution provides continuous threat detection and analytics for SAP systems deployed on Azure, in other clouds, or on-premises. Now, SecOps teams can use Azure Sentinel’s visibility, threat detection, and investigation tools to protect their SAP systems and cross-correlate across their entire organization.
Effective SAP threat monitoring
An effective approach to SAP threat monitoring has several key requirements:
- Multi-layered coverage: An SAP threat monitoring solution needs to cover both the infrastructure layer (virtual machine, storage, and network) as well as the business and applicative layers since threats traverse every layer of the SAP system.
- Rich insight into SAP applicative and transactional data: SAP systems produce viable security data in the form of change documents, audit logging, job execution, data transformation (table data), and more. For a complete picture of potential threats, you need visibility into all this activity.
- Correlation across enterprise data sources: SAP systems are complex, and indicators of compromise often aren’t straightforward. To reduce noise, it’s imperative to cross-correlate across additional data sources such as network, storage, or identity data, as well as across other entities, such as systems and users.
- Flexible deployment: SAP NetWeaver systems can be deployed on-premises, in the cloud, or hybrid deployments. Any effective SAP monitoring solution needs to offer deployment flexibility and provide visibility into any of these deployment configurations—especially since cloud transformation is often a long, multi-stage process, and organizations may find their SAP deployment method changing over time.
- Threat detections specific to SAP: SAP systems are unique environments facing unique threats. An effective monitoring approach needs to include threat detections and analytics tailored to SAP-specific use cases and threats.
- Customizability: On the flip side, SAP ABAP platforms inclusive of S/4HANA are also highly custom in nature, which means that you can’t rely solely on out-of-the-box detections. The SAP threat monitoring approach needs to be open to modification and include the ability to build or import your own security content, so you can tailor detection to your specific environment.
Our approach: The SAP threat monitoring solution for Azure Sentinel
We kept these requirements top of mind when developing our approach to SAP threat monitoring. The Azure Sentinel SAP threat monitoring solution can be deployed in one simple package that includes all components. The solution includes:
- A Rich NetWeaver data connector: The SAP collector is delivered as a Docker container image that can be deployed anywhere in the network and integrate into NetWeaver capable systems. The data connector collects over 10 different log files with SAP NetWeaver enabled systems that allows monitoring business and application layer-related risks within SAP systems. You can view the full list of available log sources in the documentation.
- SAP underlying Infrastructure data connectors: Existing Azure Sentinel data connectors, such as those for virtual machines, networking, and Azure Active Directory, monitor the underlying infrastructure.
- Built-in security content: Out-of-the-box detections catch important SAP threats like system configuration changes, execution of sensitive function modules, and suspicious activity by privileged users. Plus, a workbook helps SecOps teams visualize the security health of their SAP systems.

Figure 1: Out-of-the-box detections included in the Azure Sentinel SAP threat monitoring solution.

Figure 2: SAP workbook helps analyze different security audit log events by severity, in order to keep track of the different events on the SAP ABAP system.
![]()
Figure 3: Visualizing and tracking authentication events using a built-in workbook.
- A rich set of configurations is also included in the form of watchlists. These watchlists reduce noise by allowing you to describe your specific SAP environment and the risks you’re most concerned about. For example, specify whether a certain system is a production or test system, and identify any specific SAP transactions that should be especially carefully monitored.
Use case: Monitoring for abuse of privileges with Azure Sentinel
What does this look like in action? One of the most common SAP security risks is the potential misuse of privileges. With the right privileges, SAP users can execute functions and even debug ABAP code running on these systems, which—while necessary—also by nature opens the system up to significant risk. For example, an SAP user with developer privileges could exploit those privileges to view sensitive human resources or financial data by executing a function module to gain elevated access privileges.
Azure Sentinel gives you the ability to quickly detect these threats without drowning in noise. You can monitor function modules executed via SE37, while also targeting your detections by defining a granular set of your most sensitive modules. You can also specify that these detections should only apply to your production systems since these behaviors can be common and harmless in developer or sandbox systems.
The pre-configured functions and detections can monitor for these threats from day one, while still providing the flexibility you need to customize your implementation.
Another common scenario is the use of break-glass users such as DDIC/SAP. While those users are frequently enabled for valid reasons, the usage of these privileges still needs to be very carefully monitored due to the high privileges of the default “superman” users. In Azure Sentinel, you can monitor for these users and use automation to help you manage these risks. For example, monitor for system access from these users, and when it is detected, automatically call a playbook that will send a Teams message to confirm that SAP basis permissions were given to perform the operation.
Learn more
Azure Sentinel threat monitoring for SAP capabilities enables you to protect critical SAP systems more efficiently and effectively and extends Azure Sentinel’s cloud-native security analytics and AI capabilities to the world of SAP. Learn more about the SAP threat monitoring solution in documentation, or join us live on May 26, 2021, at 8 AM Pacific Time to learn more about the SAP threat monitoring solution live in our Azure Sentinel webinar.
In addition to threat monitoring for SAP, we announced several new Azure Sentinel innovations at the RSA Conference 2021. Learn more about these announcements, including new integrations, ML features, collaboration capabilities, and more, on the Azure Sentinel announcement blog.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE