Protection from Malware and AWS Bucket Leaks Cloud Advocate

Cloud Native
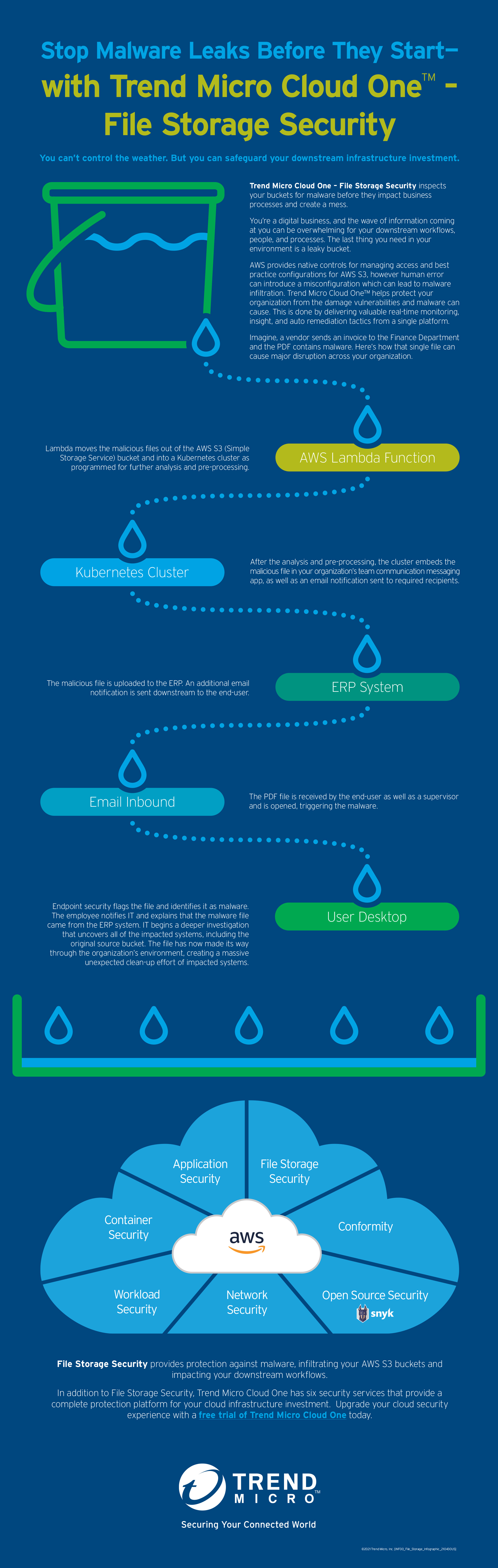
You can’t control the weather. But you can safeguard your downstream infrastructure investment.
Today’s organizations hinge on the rapid transfer of information to meet business requirements and customer needs. With the growth of cloud services and increased pace of application development, more business files are being sent and received by cloud storage infrastructure. This brings immense opportunity to businesses regarding the storage and retrieval of any amount of data, any time, from anywhere on the web, including log files, PDFs, media files, and images. Many applications integrate file and object storage into their architecture for file record requirements because of the ease of use, scalability, and cost.
Yet, while the storage infrastructure is secure, human error can impact the integrity of the file storage systems. Furthermore, the files themselves can pose a threat to the organization if they contain malicious content from unknown senders. This can lead to serious breaches which inflict harm to downstream workflows and business processes throughout your organization or customer and partner portals, ultimately eroding their trust.
Check out the infographic below to better understand how files can impact application and business processes as well as compliance. Learn more from Trend Micro Cloud One™ – File Storage Security to help ensure best practices are automatically baked into your software supply chain and malicious files are identified and remediated before they impact your downstream workflows.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE