Secure your endpoints with Transparity and Microsoft
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA.
Endpoint protection platforms (EPPs) are dead and no longer sufficient to protect your organization, right? Wrong.
When it comes to cybersecurity, the ability to normalize and correlate disparate logs from different devices, appliances, and resources is key, as is the ability to react quickly when under attack. The faster you can react and remediate, the smaller the blast radius and impact on your organization. In this blog post, we explore the importance of EPP as an essential component in your security strategy, the importance of securing your endpoints, and the evolution of EPP into endpoint detection and response (EDR) and extended detection and response (XDR). We’ll also discuss managed detection and response (MDR), and the value that an experienced managed security service provider can bring. The Transparity Cyber Managed Security Service takes a holistic approach to cybersecurity, and it uses EPP, EDR, and XDR to protect our customers while providing all-day, everyday MDR to detect and remediate threats.
Learn what EPP, EDR, XDR, and MDR can mean to you, and how Microsoft Cloud Security services work together to support the delivery of a comprehensive security foundation.
EPP: Endpoint protection platform
Traditional EPPs, such as antivirus and antimalware, protected endpoints by identifying and blocking known, common, and easily detectable threats using signatures and passive heuristics (pattern or routine matching). This type of EPP is no longer sufficient to protect an endpoint and can easily be circumvented using even basic defense-evasion techniques.
Modern endpoint protection adds many layers of protection beyond what has historically been offered and is an essential part of the endpoint protection framework. This type of EPP detects malicious activity using pre-execution analysis, behavioral analysis, active heuristics, and sandboxing.
Many next-generation antivirus products include passive protection capabilities such as host-based firewalls and data encryption.
An important feature of an EPP to consider is the deprecation of a traditional management server in favor of the platform being cloud-managed. Cloud management enables the collection of telemetry data and provides continuous monitoring, along with the ability to manage the endpoint even if there is no line of sight to the organization.
Next-generation EPPs such as Microsoft Defender Antivirus add critical protection by utilizing machine learning, big-data analysis, in-depth threat resistance research, and the Microsoft Cloud infrastructure. Being cloud data-assisted means that the EPP no longer needs to maintain a local database of all known indicators of compromise (IoCs) but can query the cloud intelligence to validate artifacts that it cannot classify.
Endpoint protection should always be used in conjunction with an EDR, such as Microsoft Defender for Endpoint, as opposed to a standalone product. When used with Defender for Endpoint, Microsoft 365 Defender can be configured to provide passive scanning alongside an EPP from another vendor.
Elements of both EPP and EDR are required to ensure an all-encompassing endpoint protection platform. EPP and EDR should complement each other rather than replace.
EDR: Endpoint detection and response
Endpoint detection and response builds on the EPP but does not replace it. Both are required to correctly protect an endpoint.
EDR vastly extends the endpoint protection scope to detect and respond to threats across all endpoints holistically, thus eliminating blind spots. If a threat is detected on one endpoint, an automated response immediately protects, contains, and removes threats from the compromised device and begins investigations for similar behaviors across all devices onboarded.
Unlike EPP, EDR focuses on device and user behaviors to detect anomalous and nefarious activities. This means that EDR can detect sophisticated attacks designed to evade detection, a primary element of the cyberattack kill chain.
EDR surfaces significantly more telemetry data from the devices (more than 24 trillion signals analyzed every 24 hours) than EPP, allowing security engineers to perform threat hunting and forensic operations across all devices simultaneously while enriching the context of the data.
By analyzing the attack behavior rather than the specific payload or predefined attack pattern, EDR can detect advanced attacks such as fileless, living-off-the-land, polymorphic malware, and other advanced persistent threats (APTs). Any initially undetected attacks can also be automatically remediated post-compromise, looking back in time to identify the start of the attack before it became malicious by removing injected registry keys, services, or scheduled tasks, for example.
AI, machine learning, and threat intelligence play a key part in delivering this behavior-based protection and enabling immediate responses to active threats.
XDR: Extended detection and response
Where EDR builds on the capabilities of EPP, XDR builds on the protection and security posture management of EDR. XDR is designed to take signals, logs, and telemetry data from disparate feeds and connectors and provide security analysts with a further augmented view of the organization’s security posture and landscape.
By bringing in feeds from cloud and on-premises workloads, firewalls, proxies, cyber-AI, user and entity behavior analysis (UEBA), cloud access security broker (CASB), platform as a service (PaaS), software as a service (SaaS), secure access service edge (SASE), security events, Domain Name System (DNS), wireless controllers, active directory (AD), active directory domain services (ADDS) and Microsoft Azure Active Directory (Azure AD), applications, threat intelligence, security analytics, syslog, Common Event Format (CEF), threat and vulnerability management (TVM), and more, XDR can extend visibility beyond the individual security tools and platforms to provide correlation of attacks. For example, security analysts might be alerted to an attack through the EPP or EDR but could potentially identify the initial attack vector and track its lateral movement through the XDR.
This capability greatly reduces the time to identify the threat, contain it, and remediate it. The aforementioned threat hunting and forensics also now extend beyond the endpoints and can be performed across the entire estate.

In a study of our internal data, we found that 39 percent of incidents were detected by Microsoft Defender for Cloud, while 23 percent were detected by Microsoft Sentinel. On the other end of the spectrum, Microsoft 365 Defender detected 0.3 percent of incidents, and Defender for Cloud Apps detected 2.1 percent.

Many XDR platforms, such as Microsoft 365 Defender, Microsoft Defender for Cloud, and Microsoft Sentinel security information and event management (SIEM), add security orchestration automation and response (SOAR) capabilities to drive down the time to react and perform automated actions. Sentinel also uses the data it ingests to provide powerful insights into user and device behavior using its UEBA engine.
Cloud Security Posture Management (CSPM) platforms like Defender for Cloud can analyze the ingested data to derive hardening guidance tailored to the resources identified, along with a Secure Score to help engineers prioritize remediations.
XDR provides a single pane of glass and insight into the security posture of your environment.
MDR: Managed detection and response
As discussed in the previous sections, EPP, EDR, and XDR provide security analysts with the enriched data for threat hunting and forensics. The MDR service uses this data for these functions as well as incident response and management, and to reduce the mean time to detect (MTTD) and the mean time to respond (MTTR). The faster and more accurately the security team can respond, the smaller the blast radius and impact to the organization.
Threat actors are gaining in sophistication each day. Their aim is often to avoid detection for as long as possible, and they are likely to have performed a great deal of research about your organization before an attack. As such, they should be aware of your working times and potential gaps in security cover or blind spots. Having the ability to defend against threats continuously all day, every day is a must for MDR, as is the highly skilled team of security analysts.
MDR is not a product or technology—it’s a service. This service provides the best-of-breed threat detection and response along with highly skilled security experts working around the clock to protect your organization. The term “defense-in-depth” is commonly used, and having multiple layers of protection is the best way to mitigate various attack vectors, but not having a team of expert engineers to correlate this data means you are not getting the various tools’ true values.
Who is Transparity?
Transparity is a MISA member and Microsoft pureplay Gold Partner founded in 2015, made up of a family of specialized members including a dedicated security brand, Transparity Cyber. With our unique culture and commitment to outstanding service and expertise consistent throughout the family, we work together in coordination across disciplines to provide the best in Microsoft Cloud technologies.
Transparity is home to skilled cloud experts with decades of combined experience. We’re proud to hold 16 Microsoft Gold Partner accreditations, Azure Expert managed service provider (MSP) status, and 11 Advanced Specializations. Transparity Cyber upholds this standard of excellence every day. In addition to our Microsoft Gold Security accreditation, we adhere to several elite standards, giving you confidence that you are working with a security partner who strives to be the very best.
We’re proud to have been named finalists in the Microsoft Security Excellence Awards 2022.
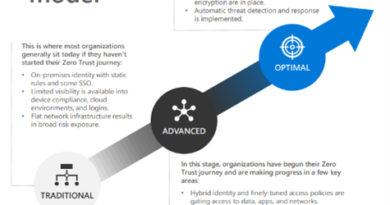
Our Managed Security Service offers constant end-to-end protection with a proactive approach to cybersecurity. Founded in the principles of Zero Trust, our experts lead with protection and prevention first, as well as performing detection, response, and recovery activities. With proactive threat hunting and vulnerability management, our clients’ environments are protected from day one while we strengthen and develop their security posture over time.

We manage and respond to thousands of incidents directly threatening our customers’ environments every month, preventing them from gaining access to your environment. From December 2021 to June 2022, we defended our customers against more than 1,000 threats every month that may have otherwise led to a breach.

The need for robust security infrastructure is growing more urgent as threats become more sophisticated and attacks become more frequent. Incidents appear to be on the rise, with 1,388 in April 2022, 1,396 in May 2022, and 1,357 in June 2022, respectively.

There were 1,212 medium priority incidents detected in May 2022, and 54 highest priority incidents in January 2022.

Learn more
Find Transparity on the Microsoft Commercial Marketplace.
To learn more about MISA, visit our MISA website where you can learn about the MISA program, product integrations, and find MISA members. Visit the video playlist to learn about the strength of member integrations with Microsoft products.
Learn more about Microsoft Cloud Security services.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE