Security Risks with Private 5G in Manufacturing Companies Part. 1 Security Evangelist

Exploits & Vulnerabilities
We can see signs of increased activity in areas of business that use 5G around the world. 5G technology will usher in new personal services through smartphones, and it will also play a large part in industry. The option of Private 5G lets private companies and local governments have their own telecom infrastructures. However, the “democratization of communications” entails its own risks that have not yet been made clear. To identify these risks, Trend Micro performed tests using an environment modeled after a steelworks with 5G equipment.
Installing mobile communication systems in the industrial sector
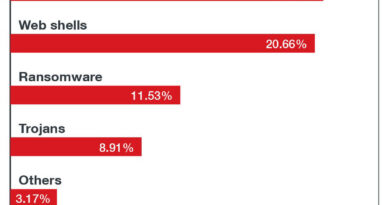
5G represents the fifth generation of mobile communication systems, and it is one of the leading-edge technologies in the modern day alongside AI (artificial intelligence) and IoT (Internet of Things). It serves a foundation to support next-gen society as it makes leaps and bounds in digital transformation. The biggest features of 5G are its large bandwidth, its extremely high capacity for simultaneously connected devices, and its ultra-low latency. Unlike the chiefly human-oriented services in 4G, these features allow 5G to be applied to a wide range of use cases for communication between machines.
In particular, 5G cuts latency so low that it meets the minimum latency requirement in industrial applications. This means that 5G can ignite the spread of mobile networks in the field of industry, such as in mission-critical use cases that conventional mobile network systems were not designed for (Fig. 1).
The installation of mobile communication systems in industry marks a significant transformation in corporate IT, all thanks to 5G. With a huge increase in the number of simultaneously connected devices in 5G, we are likely to see even more progress in the spread of IoT devices. As such, 5G does not just mean a fast network; it can be seen as the foundation for digital transformation at companies.
Mobile communication systems let users stay connected on the move
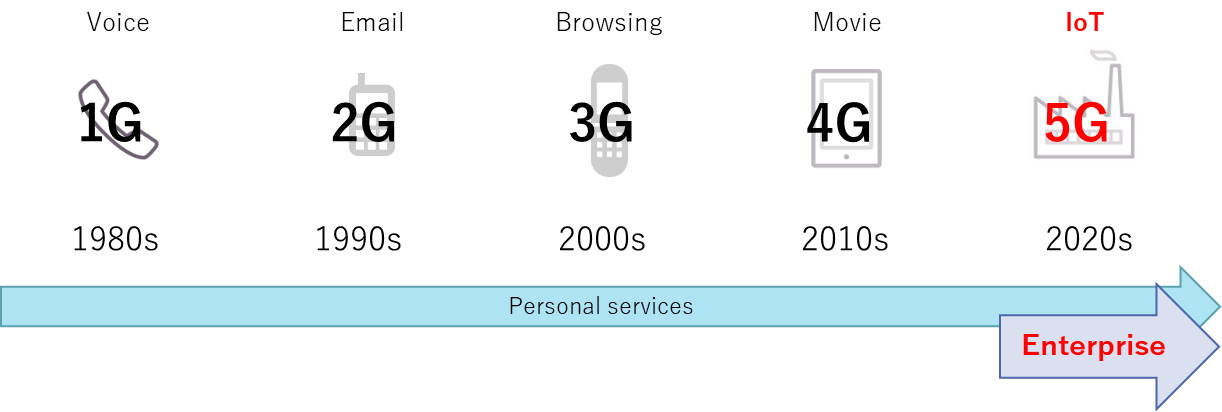
5G is the fifth generation of mobile communication systems. Mobile communication systems refer to technology that lets users stay connected on the move. The basic configuration of mobile communication systems has not changed since 1G, the first generation. There are three main elements, as shown below (Fig. 2).
The first element is user equipment (UE). This refers to smartphones and other devices with a SIM card in them. In the age of 5G, we can expect a wide range of user equipment to gain traction beside smartphones, such as factory equipment, automobiles, sensors, security cameras, and other IoT devices. These devices communicate wirelessly with nearby base stations. A base station contains antennas, and all these base stations together form the radio access network (RAN). The information gained through the RAN is passed to the core network (CN). The CN serves as the brain for the whole mobile network. This vital system manages user registration and movement, as well as data processing. These three elements work together organically so that users can communicate while they move around. This basic arrangement remains the same in the fifth generation of these systems, 5G. The basic system consists of the UE, RAN, and CN.
Smartphones have soared in popularity, but there is little awareness regarding the CN and RAN and how they work, compared to UE. This is because with mobile phones and other personal services in Public 5G, the CN and RAN are built and operated by telecom providers. This means that users can communicate without needing to think about the CN or other details. However, this is about to significantly change with the arrival of Private 5G.
What security risks are there with Private 5G?
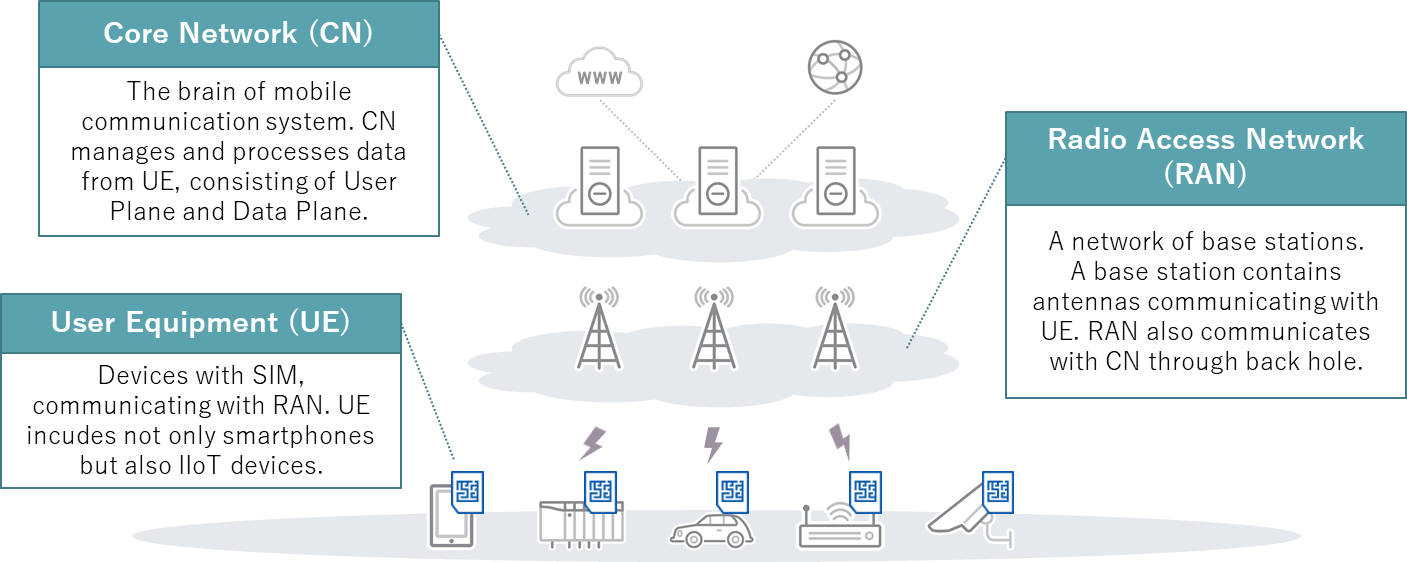
As the name suggests, Private 5G means an independent 5G network used for a specific purpose in a restricted area. The network can be designed and built in a flexible way to suit each use case, unlike public 5G networks from telecom providers. Private 5G networks are optimized at the microservice level, and this is why individual organizations are choosing to implement telecom infrastructure in their IT environments. Telecom providers conventionally did the work to build and operate core networks and wireless access networks, but with Private 5G configurations, private companies and local governments have to do this work on their own.
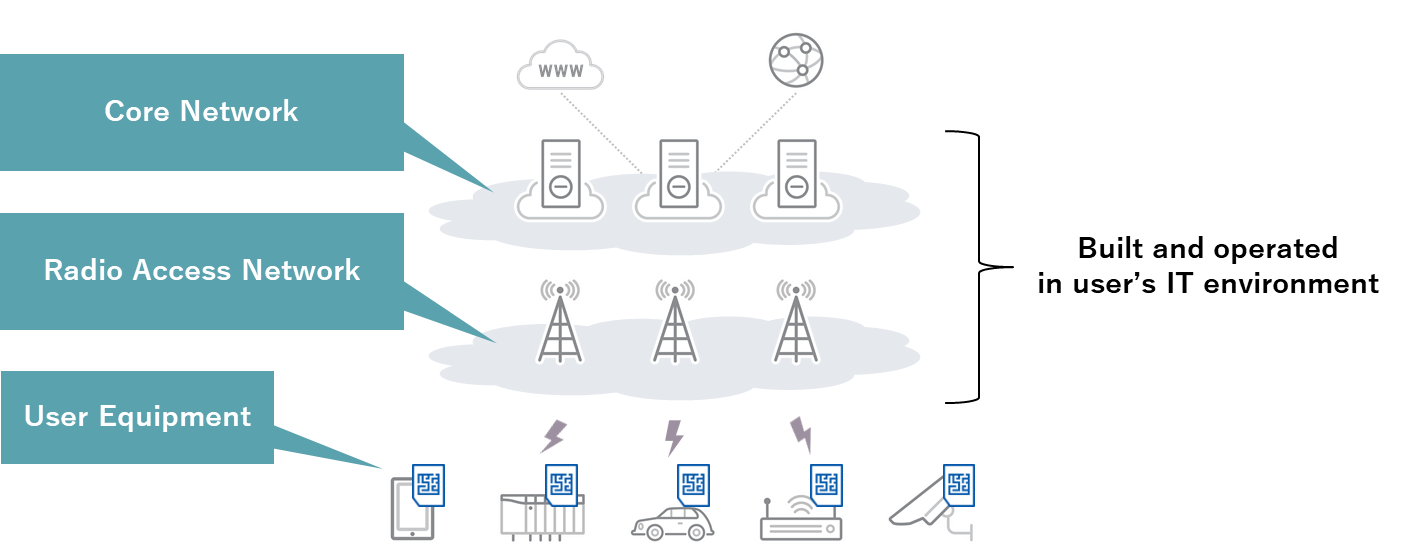
The democratization of communications helps build open technology and promotes market and business growth, but it also leads to more responsibilities for user organizations that use this technology. What’s more, typical corporate divisions that deal with systems will not be familiar with telecom infrastructure.
In light of these issues, Trend Micro conducted a field test to identify the cyber security risks that user organizations need to understand before utilizing Private 5G.
Next time, I will describe the Private 5G environment that we built for this research, the experimental method we used, and the results of our test.

YOHEI ISHIHARA
Security Evangelist,
Global IoT Marketing Office,
Trend Micro Incorporated
Graduated from the Department of Criminology, California State University, Fresno. Joined Trend Micro after experience with sales and marketing at a hardware manufacturer in Taiwan, and SIer in Japan. Collaborates with researchers worldwide to collect and provide threat information, with a focus on factory security, 5G, and connected cars. Works as a Security Evangelist to think about cyber risks in light of social conditions, and to raise awareness about security issues as a form of geopolitical risk.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE