Security Risks with Private 5G in Manufacturing Companies Part. 2 Security Evangelist

Exploits & Vulnerabilities
We can see signs of increased activity in areas of business that use 5G around the world. 5G technology will usher in new personal services through smartphones, and it will also play a large part in industry. The option of Private 5G lets private companies and local governments have their own telecom infrastructures. However, the “democratization of communications” entails its own risks that have not yet been made clear. To identify these risks, Trend Micro performed tests using an environment modeled after a steelworks with 5G equipment.
The steel industry is a prime area for installing Private 5G
Private 5G is said to bring about the “democratization of communications.” This technology allows private companies and local governments to take the driving seat in operating the latest information communication systems. However, not all organizations have the knowledge and ability to deal with telecom technology, and this can result in a security risk. We carried out this field test to identify the potential for this risk in detail. For this test, we used an environment based on the steel industry.
The nature of the steel industry makes it a truly ideal field for implementing 5G, and it also requires data integrity.
The steel industry is one of the fastest industrial fields to incorporate IT, and it has three characteristics as outlined below (Fig. 1).
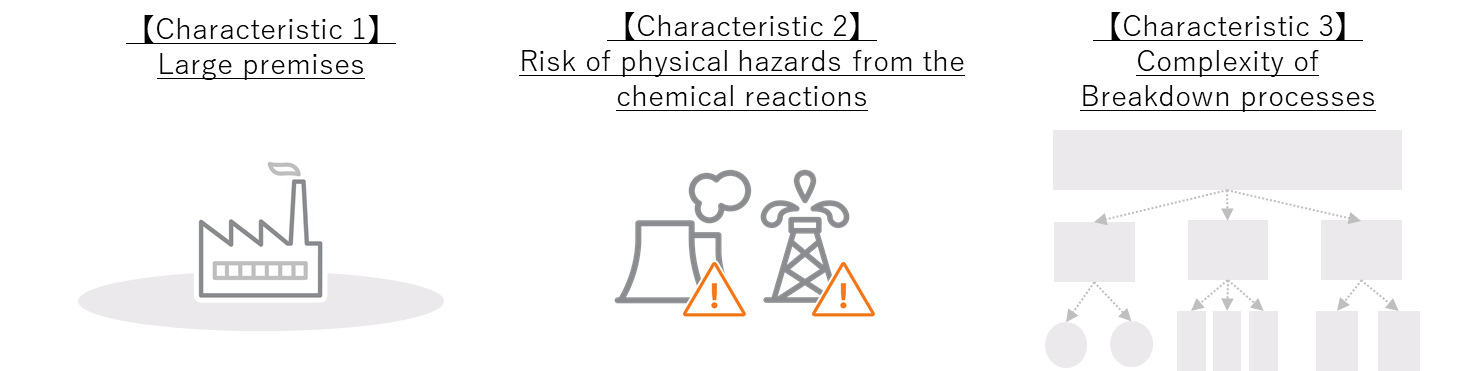
Firstly, steel production requires large premises. The steel industry is a typical hardware-based industry and requires a large area to house the necessary equipment. Private 5G has better coverage for large premises than Wi-Fi, and so there are high expectations for it to realize power savings through the remote control of related equipment, remote monitoring using 4K video from high-definition industrial TV (ITV) cameras, and remote assistance for workers on site. Secondly, steel production bears physical hazards from the chemical reactions involved. As it works with iron as a material, the industry needs to engage in processing at high temperatures to make products. This means that people cannot directly check the state of the materials, so they need to resort to sensors and computers to do so. As such, data integrity and system availability are crucial. Thirdly, the steel industry has a complex breakdown structure. Unlike the automobile industry that involves assembling a product from many components, the steel industry involves producing many different products using a single material: iron. Processing this material requires minute adjustments to temperature, air pressure, and blended components. Larger steelworks can receive up to one million orders every year, so an IT system is essential to accurately process large volumes of information.
Private 5G is expected to serve as a strong force for meeting the requirements of the industry while also boosting productivity.
Field test environment: A steelworks with Private 5G
For this research, we built an environment modeled after a steelworks with 5G equipment. We focused on three key concepts when building the environment.
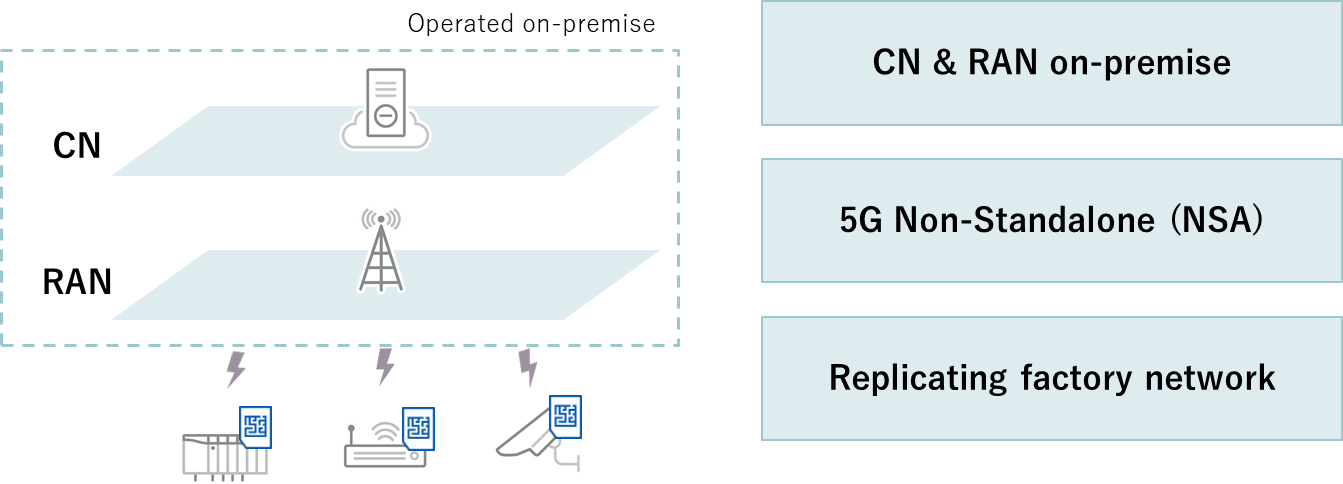
Firstly, we built the core network and radio access network all on-premise. While there are multiple different approaches in building Private 5G configurations, for this research we envisioned a scenario where the Private 5G user builds and operates the system on its own, whereby it owns a completely separate network of its own. Secondly, we implemented a non-standalone configuration. Non-standalone means a 5G network architecture that makes maximal use of currently operational 4G network equipment. In contrast to this, an architecture that only supports 5G is called standalone. This requires switching all communication equipment to a standalone format, and so the non-standalone is likely to be chiefly employed for the time being. Thirdly, we focused on replicating the factory network by using PLCs, HMIs, and other equipment. This helped us check for physical damage.
The network configuration for our test is shown in Fig. 3. You can see that the network includes IT, OT, and CT.
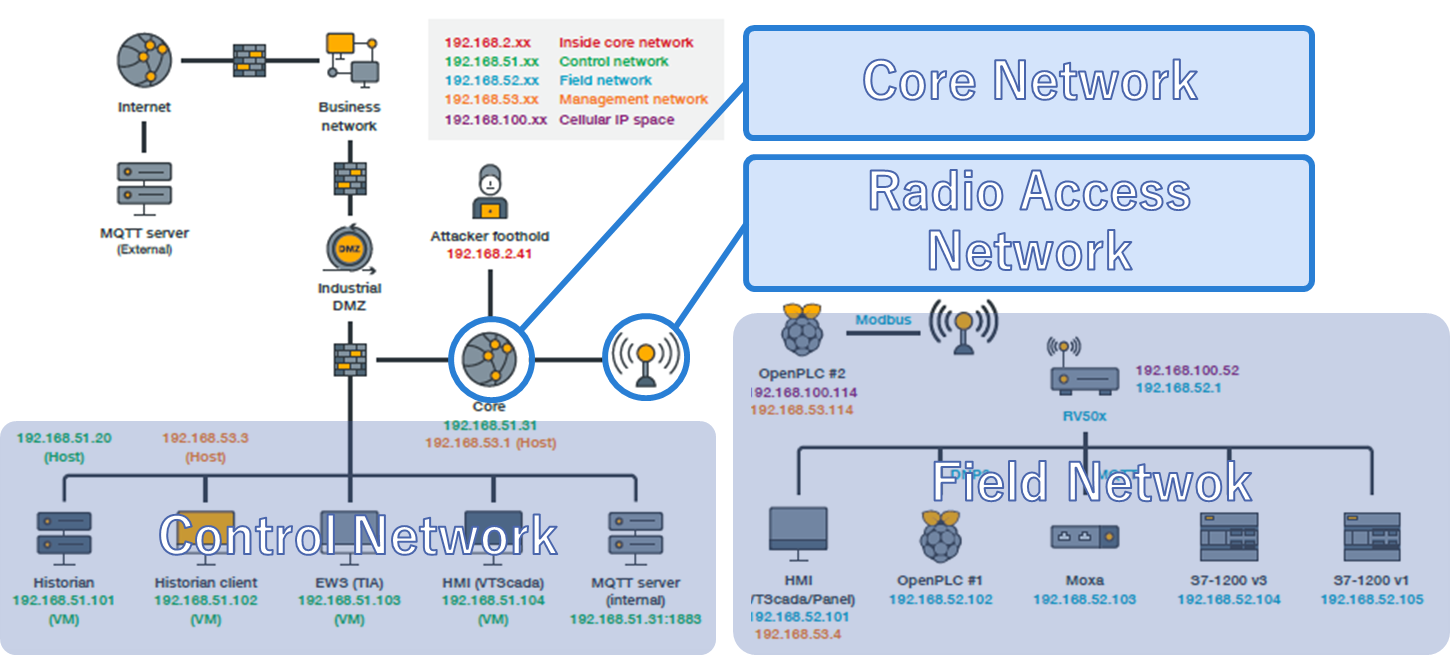
The bottom right of Fig. 3 represents the field network. PLCs and other devices are connected to this network, which replicates the physical environment at a steelworks. The control network is at the bottom left. This network is connected to the computers used by administrators, and this network controls the field network. The middle of the diagram features the core network and radio access network that serve as the main system in this test. These are both in the realm of CT. The core network functions as the control tower for the communication system, so it is one particularly vital area for implementing proprietary technologies for mobile communication networks.
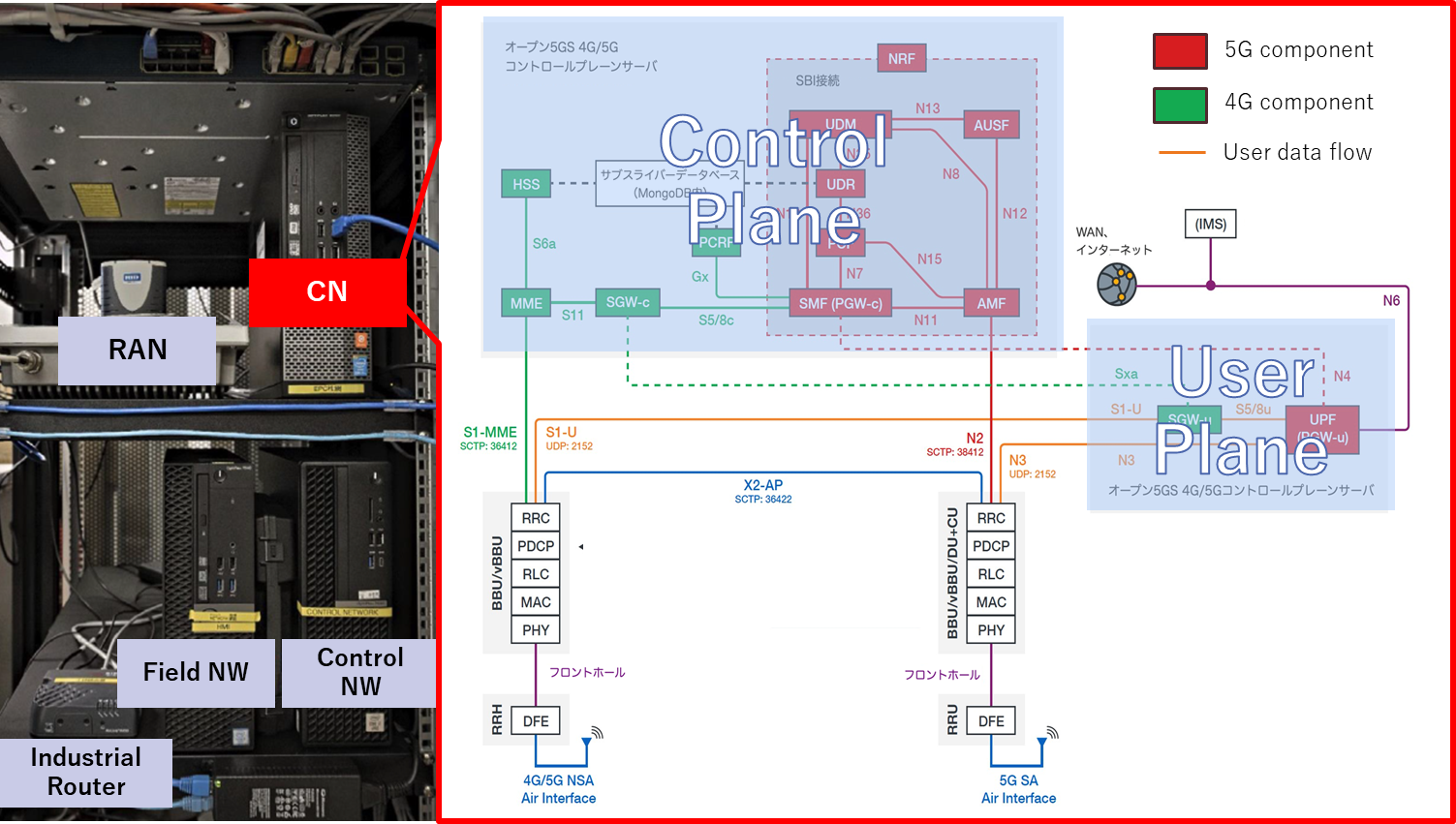
The left-hand side of Fig. 4 shows the actual field test environment. It looks extremely simple at first glance, but it houses an extremely complex software architecture as shown in the block diagram at the right. It is important to note that the core network is made up of the control plane that governs user registration and management, and the user plane that governs data processing. 5G communications rely on these two planes functioning correctly. The core network is made up of communication technology that is unfamiliar to corporate IT personnel, so this is unknown territory for users.
After conducting tests in this environment, we identified that the core network has four possible routes for penetration and three points for intercepting signals. Next time, I will describe these results in more detail.

YOHEI ISHIHARA
Security Evangelist,
Global IoT Marketing Office,
Trend Micro Incorporated
Graduated from the Department of Criminology, California State University, Fresno. Joined Trend Micro after experience with sales and marketing at a hardware manufacturer in Taiwan, and SIer in Japan. Collaborates with researchers worldwide to collect and provide threat information, with a focus on factory security, 5G, and connected cars. Works as a Security Evangelist to think about cyber risks in light of social conditions, and to raise awareness about security issues as a form of geopolitical risk.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




